Apply rate-limiting to your resources using AWS Cloud-front and WAF
At Halodoc, we take security very seriously. We also run a security bounty program. We audit our systems regularly.
This blog talks about one security measure called rate-limiting.
What is rate-limiting?
Rate-limiting keeps the frequency of operation below a defined constraint. In large-scale systems, we use rate-limiting to protect underlying services and resources.
The most popular type of rate limiting is "user rate-limiting". User rate-limiting associates the number of requests a user is making to their API key or IP. If the user exceeds the rate limit, then any further requests will be denied. User will have to reach out to the developer to increase the limit or wait until the rate limit timeframe resets.
Why we need rate-limiting?
Rate limiting is put in place as a defensive measure. Services need to protect themselves from excessive use—whether intended or unintended—to maintain service availability.
Even highly scalable systems should have limits on consumption at some level. Rate limiting on both the client-side and the server-side is crucial for maximizing throughput and minimizing end-to-end latency across large distributed systems.
What are all the different ways to apply rate-limiting?
There are various ways to implement rate-limits. Rate-limiting can be done at the server level; it can be implemented via a programming language or even as a caching mechanism.
At Halodoc, we have implemented the rate-limiting for few of our customer-facing application resources using AWS cloud-front server and WAF. In the following section, we will dive into how this is implemented.
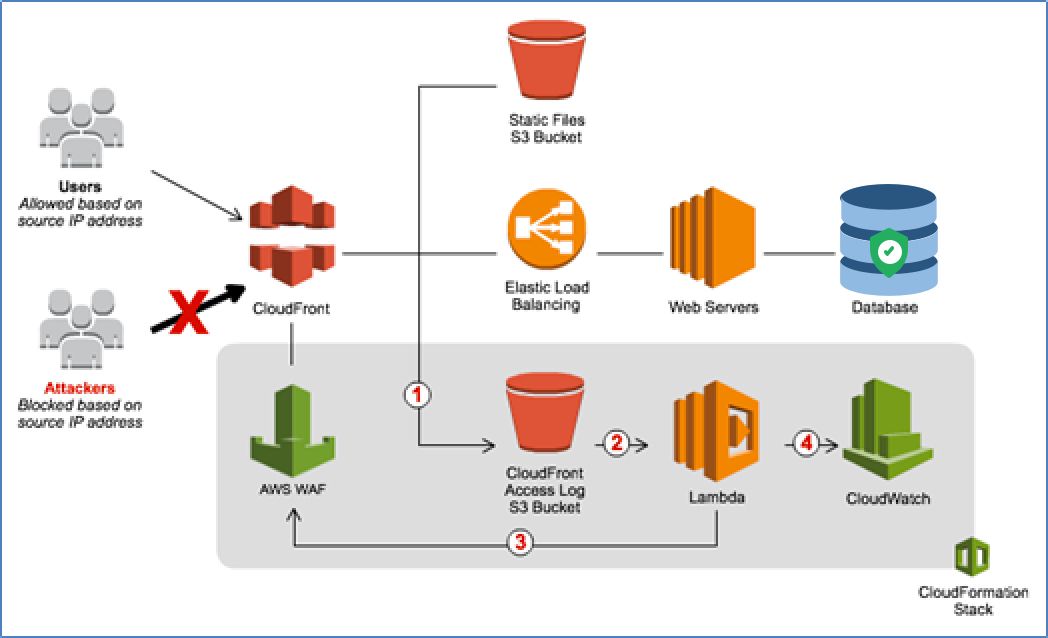
Benefits of enabling rate-limiting with AWS CloudFront
Easy analysis of data using Athena
Amazon Athena is an interactive query service that makes it easy to analyse data directly in Amazon Simple Storage Service (Amazon S3) using standard SQL. Athena helps you analyse unstructured, semi-structured, and structured data stored in Amazon S3. If your application is serving through AWS CloudFront, all the access logs are stored in S3. With a few actions in the AWS Management Console, you can point Athena at your data stored in S3 and begin using standard SQL to run ad-hoc queries and get results in seconds. This will be very helpful in right-sizing the rate-limiting rule.
Plugin conditions
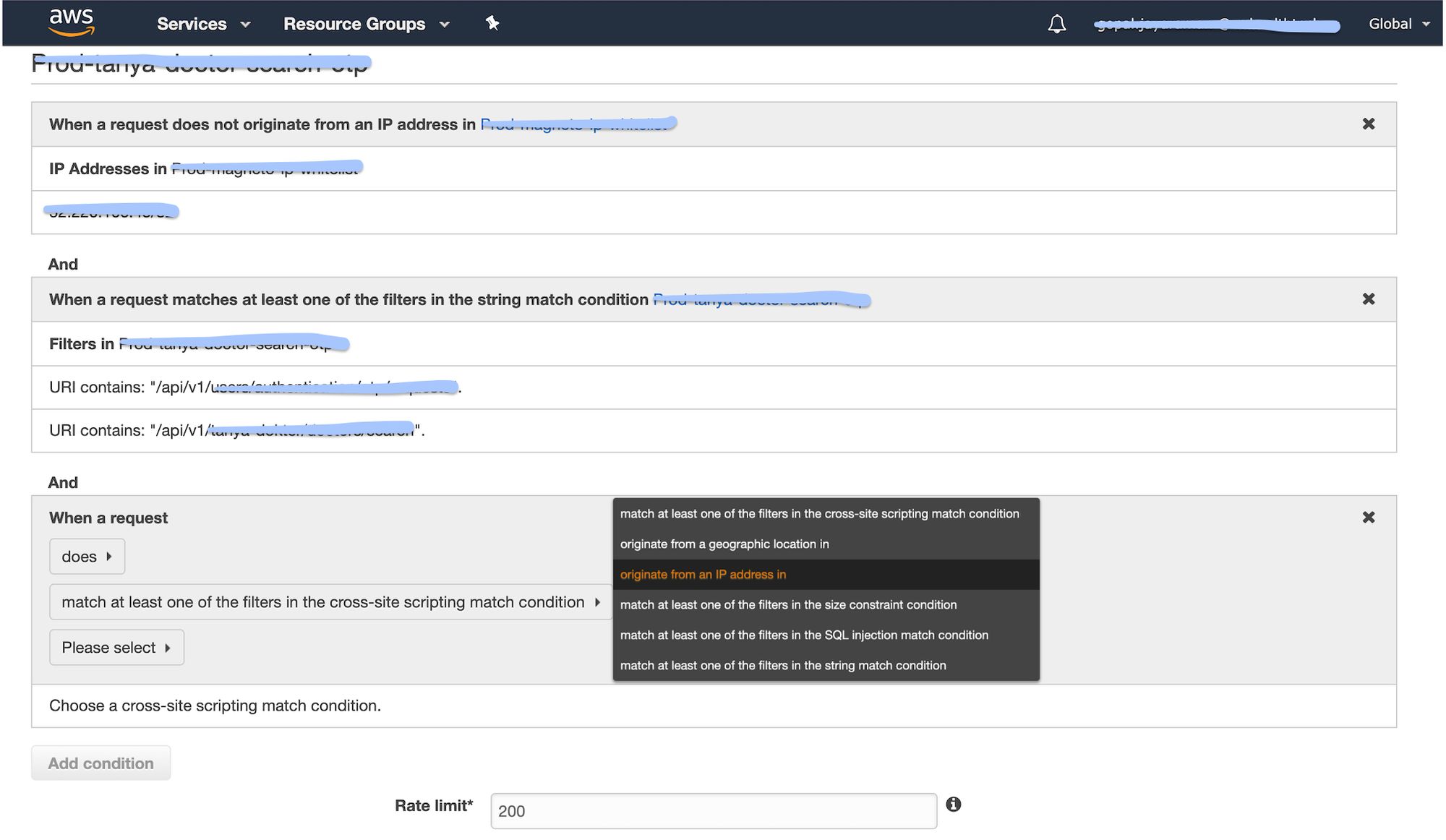
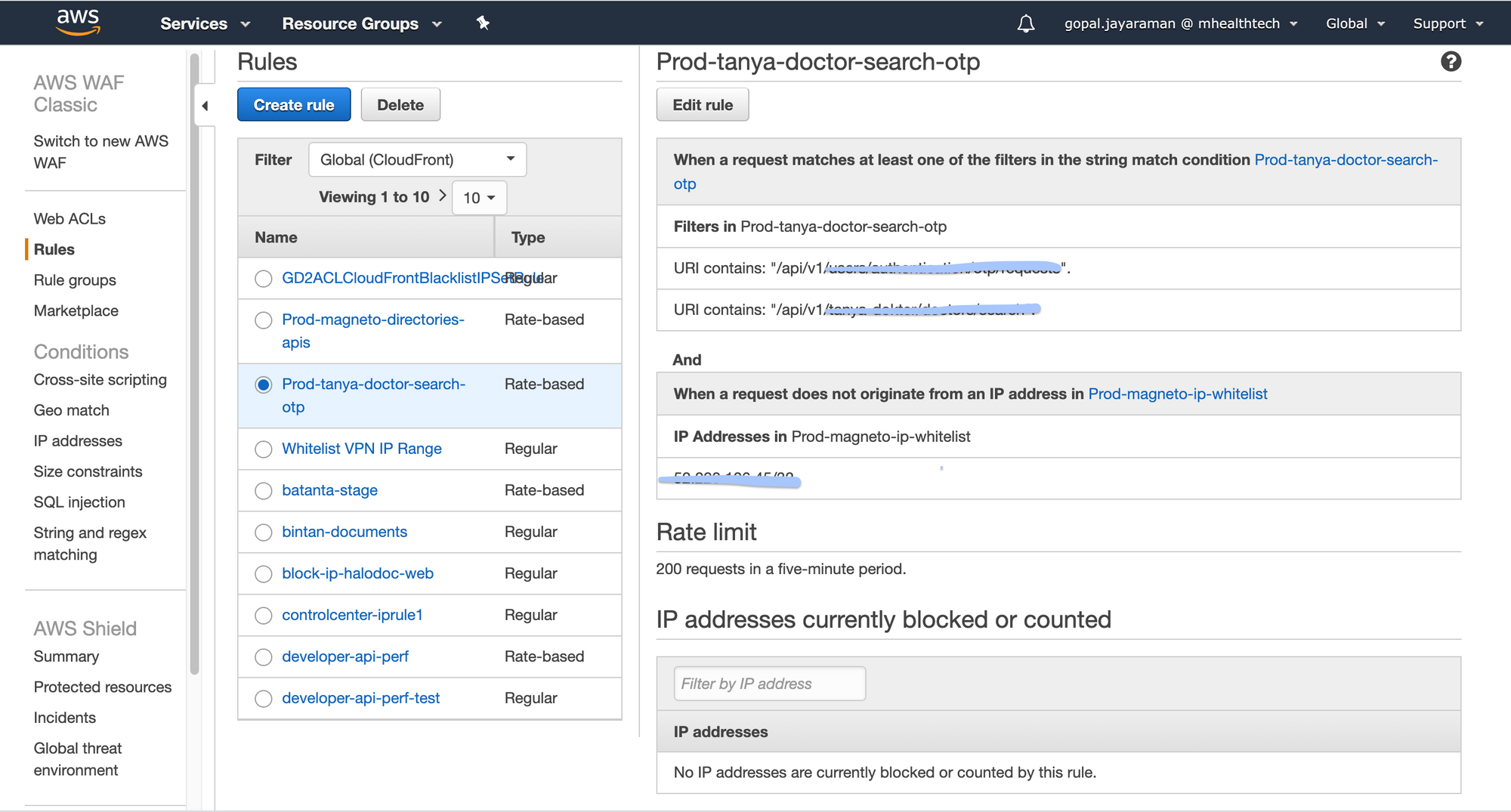
You can specify a rate-limit alone, or rate-limit and additional conditions. If you specify only a rate-limit, AWS WAF places the limit on all IP addresses. If you specify a rate-limit and IP addresses as conditions, AWS WAF sets the limit on IP addresses that match the conditions.
Quick action
When an IP address reaches the rate limit threshold, AWS WAF applies the assigned action (block or count) as quickly as possible, usually within 30 seconds. Once the action is in place, if five minutes passed with no requests from the IP address, AWS WAF resets the counter to zero.
Fixed time window
For a rate-based rule, enter the maximum number of requests to allow in any five minute periods from an IP address that matches the rule's conditions. The rate limit must be at least 100.
Whitelisting internal IPs
From a security point of view, it's easier and much more efficient to put a complete ban on everything, and only let in a selected few. When just trusted users can gain access, IP whitelisting allows you to control and limit access based on a list of specified IP addresses. It's commonly used by administrators to prevent unauthorised users from accessing corporate digital assets. We can whitelist the internal IPs which will consume the groups of APIs which are applying rate-limit. There won't be any restriction for the internal IPs using those APIs.
Steps to enable rate-limiting with AWS CloudFront
1. Right-sizing (allowed count) for the respective API or APIs group
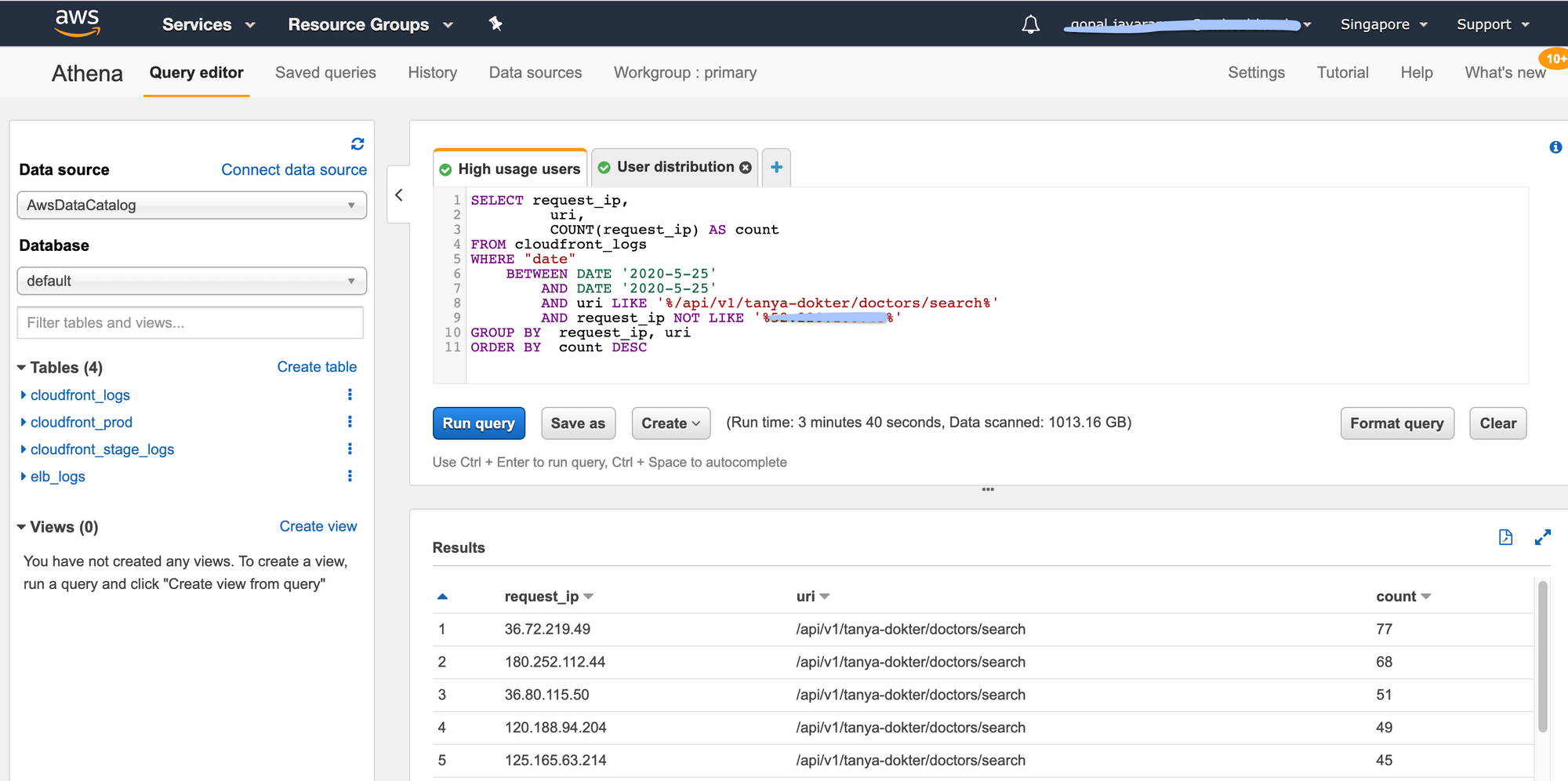
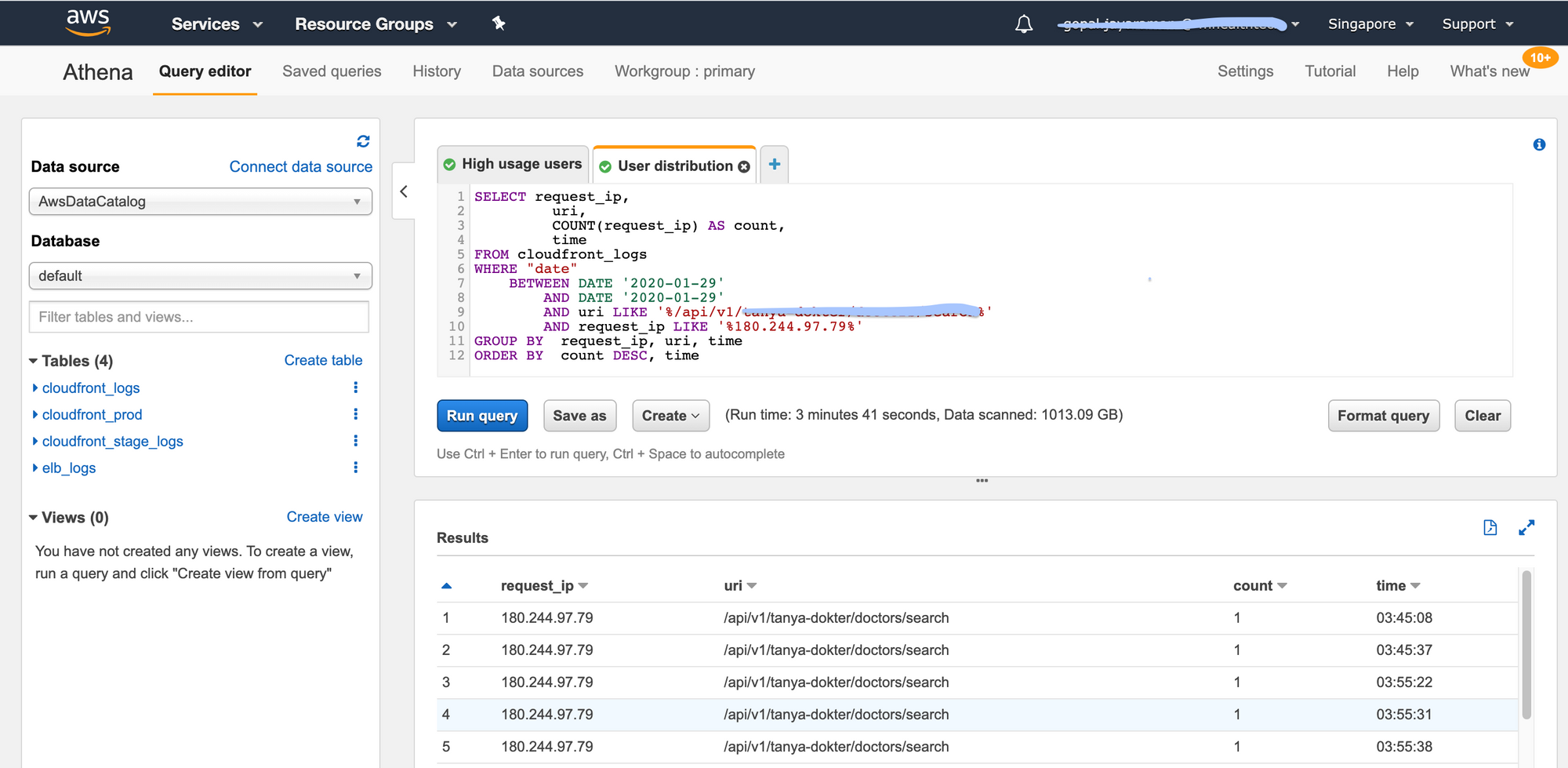
The very first step is to analyse the past data and come up with the allowed count. We can use GA(Google Analytics) to get the dates where the page views are high or specific dates when marketing events occur. We then use AWS Athena to query for high usage users and specific user distribution patterns. We do this for a few dates so that we can get approximate that we can use to determine allowed count.
2. Configuring the cloud-front
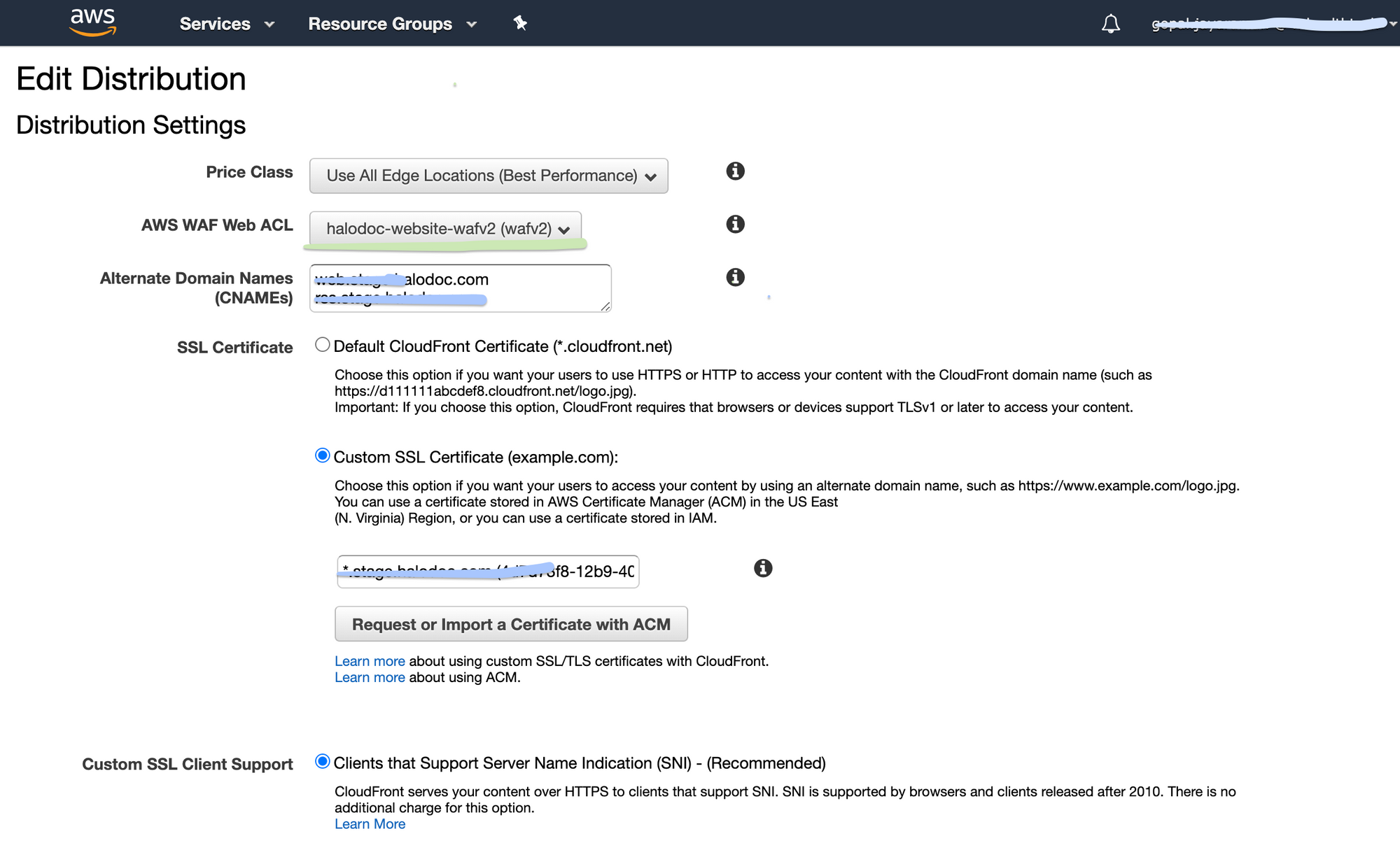
Once we get the allowed count, we apply it in the AWS WAF by creating a custom rule. The next step is attaching the created WAF rule to the CloudFront. We have now applied rate-limiting to the resources.
What will happen if the limit is exceeded?
If a user sends too many requests, API rate limiting can throttle client connections instead of disconnecting them immediately. Throttling lets clients still use your services while still protecting your API.
Conclusion
Unregulated API requests can also lead to slow page load times for websites. Not only could this leave an unfavorable opinion with your customers, but it can also tank your SEO rankings.
As we've seen, rate limiting is an essential mechanism. If you're using API requests in any regard, consider these rate-limiting techniques to increase security, business impact, and efficiency across the board.
Interesting in exploring with us
We are always looking out for top engineering talent across all roles for our tech team. If challenging problems that drive big impact enthral you, do reach out to us at careers.india@halodoc.com
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke.
We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 2500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allows patients to book a doctor appointment inside our application.
We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates foundation, Singtel, UOB Ventures, Allianz, Gojek and many more. We recently closed our Series B round and In total have raised USD$100million for our mission.
Our team work tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.




