Automated API Security Testing to Enhance Security Posture
At Halodoc, we recognise the importance of safeguarding our information systems. Therefore, we have adopted a comprehensive approach to improve the effectiveness of our security measures and as part of our continuous efforts, we have recently implemented an innovative tool specifically tailored for automated security testing of our APIs. We invite you to join us on this journey as we delve into the introduction, explaining the benefits of Automated API Security testing with Pynt and how we do the integration with our CI/CD pipeline to strengthen our organisation’s security postures.
Automated Security Testing of APIs
Ensuring APIs are secure is crucial in the constantly evolving world of technology today. Strong security measures are more important than ever since APIs serve as essential channels for data transmission between servers and applications. To address these challenges, we have started leveraging PYNT, an automated API security testing tool, to streamline the API security testing and facilitating the collaboration between the security team and QA testers to detect the security issues on the API level based on the OWASP Top 10 API security risks during early stages of application development.
Key Benefits of PYNT
- Automation Capabilities: With PYNT, the process of generating API security tests is streamlined through automation, enabling developers and testers to save time and focus on remediation efforts.
- Seamless Integration: PYNT seamlessly integrates with popular tools such as Postman, Newman, and CI/CD workflows, making it effortless to incorporate into existing development pipelines.
- Comprehensive Assessment: PYNT provides thorough coverage of the OWASP top 10 API security risks, as well as other API Security risks, ensuring that no stone is left unturned in the quest for a secure API environment. It greatly serves the Application Security team’s knowledge around API vulnerabilities.
- Enhanced Flexibility with PYNT-CLI: The PYNT command-line interface (CLI) enhances flexibility, empowering users to conduct security tests on API automation scripts using either Python or Java.
- Generate Reports: Utilise the 'Show Report' API from the PYNT collection to generate detailed HTML reports of your security tests. These reports categorise issues for efficient prioritisation and resolution.
Installation, Prerequisites and Setup
Prerequisites
- Python 3.9 or Later
- Docker in the latest version available
Installation
For the sake of demonstration purposes we are currently using an EC2 instance. By the time this blog comes out, the support for setting it up in an EKS node will also be provided by the Pynt team for better compatibility with all the infrastructures. The current EC2 Instance that is being used is also configured as a Jenkins agent.
The Pynt tool should be installed in the Jenkins Agent EC2 machine using python-pip since Pynt is available as a PIP package. The below provided command line will install when executed through a bash terminal.
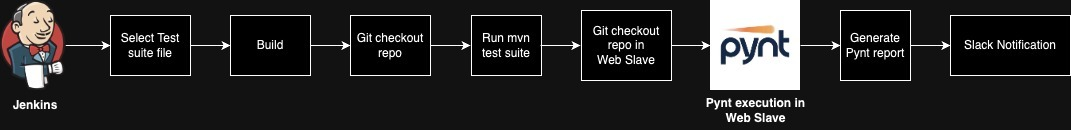
For this instance, we are currently using the Jenkins shared Library. However the setting up of the pipeline can also be done through the conventional GUI of Jenkins too. The below provided are the stages involved before the Integration of Pynt in a normal scenario of executing just a conventional Sanity/Regression test suite.
Pipeline before Pynt installation
- Stage 1: Pulling the respective Sanity/Regression Test suite from the Gitlab instance.
- Stage 2: Executing the maven test suite.
- Stage 3: Obtaining the results of the maven testsuite.
- Stage 4: Sending a slack notification that the test is completed and attaching the allure report URL in the same slack message.
Once installation of the Pynt is done, we have to add a different stage for Pynt execution where the Pynt command is running which also generates the report in .html format.
The Groovy code below adds an additional stage to the existing Jenkins pipeline, which is divided into two different parts to ease the explanation.
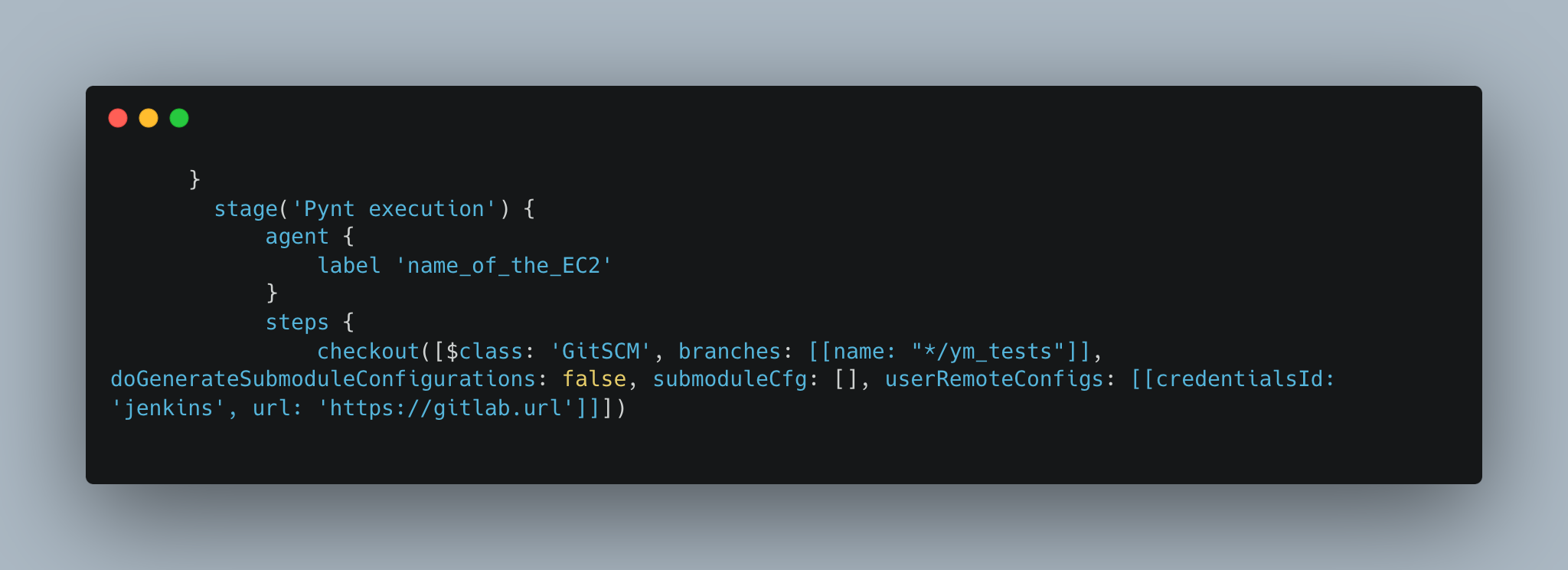
The below provided screenshot defines a new stage in Jenkins called “Pynt execution”, and initiates the first step of the process to download the maven testsuite file into the jenkins EC2 agent.
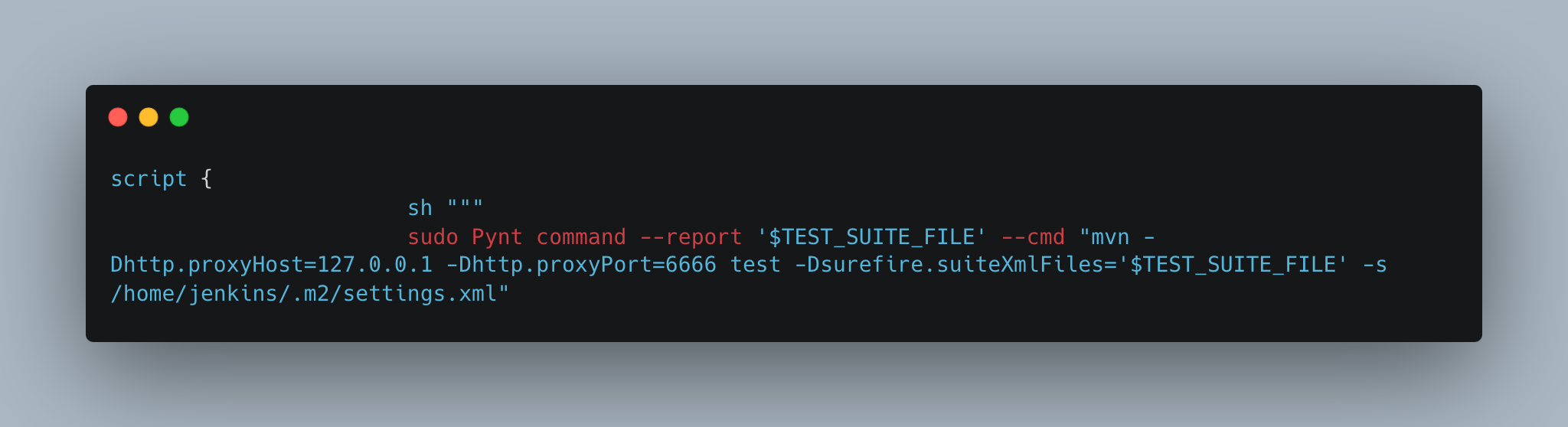
The below provided screenshot handles the Pynt execution. The “command” option in the Pynt CLI is used for executing the maven file and routing the traffic to the Pynt docker container which is listening on port 6666.
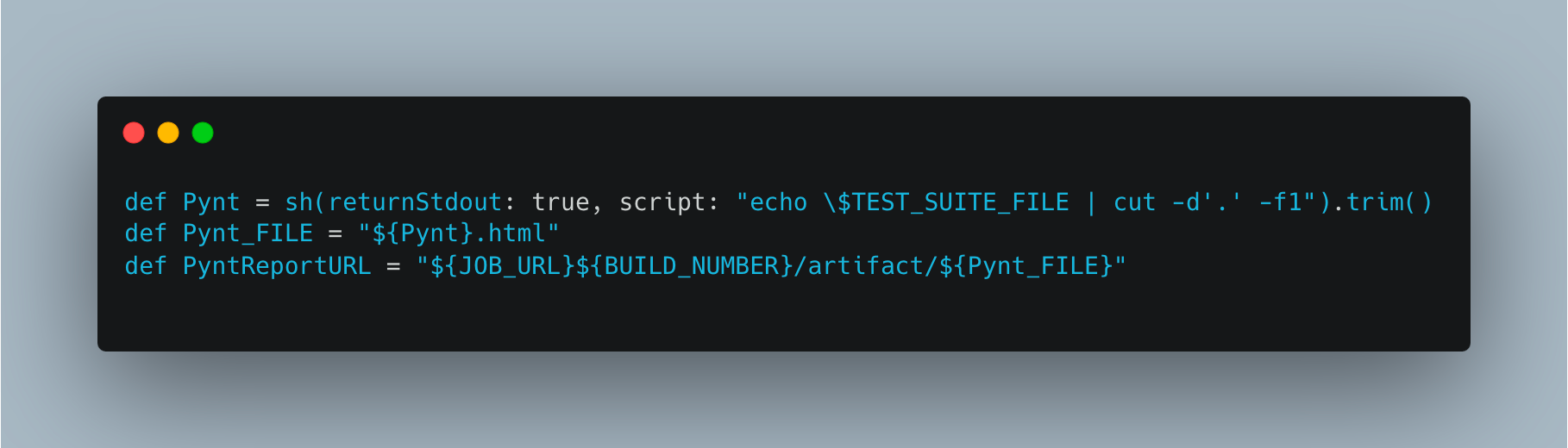
In the next part of the code snippet, we have defined multiple variables, which helps in fetching the report and archiving the report after the scan has been completed.
Pipeline after Pynt installation
- Stage 1: Pulling the respective Sanity/Regression Test suite from the Gitlab instance.
- Stage 2: Executing the maven test suite.
- Stage 3: Pulling the respective Sanity/Regression Test suite from the Gitlab instance to the Jenkins Agent EC2 Machine.
- Stage 4: Execution of Pynt.
- Stage 5: Generate Pynt report after executing the security test cases.
- Stage 6: Obtaining the results of the maven testsuite and Pynt.
- Stage 7: Sending a slack notification that the QA test is completed and attaching the allure, Pynt report URL in the slack message.
Usage
Once the installation process is completed, the Pynt execution stage will be added to the respective Jenkins pipeline.
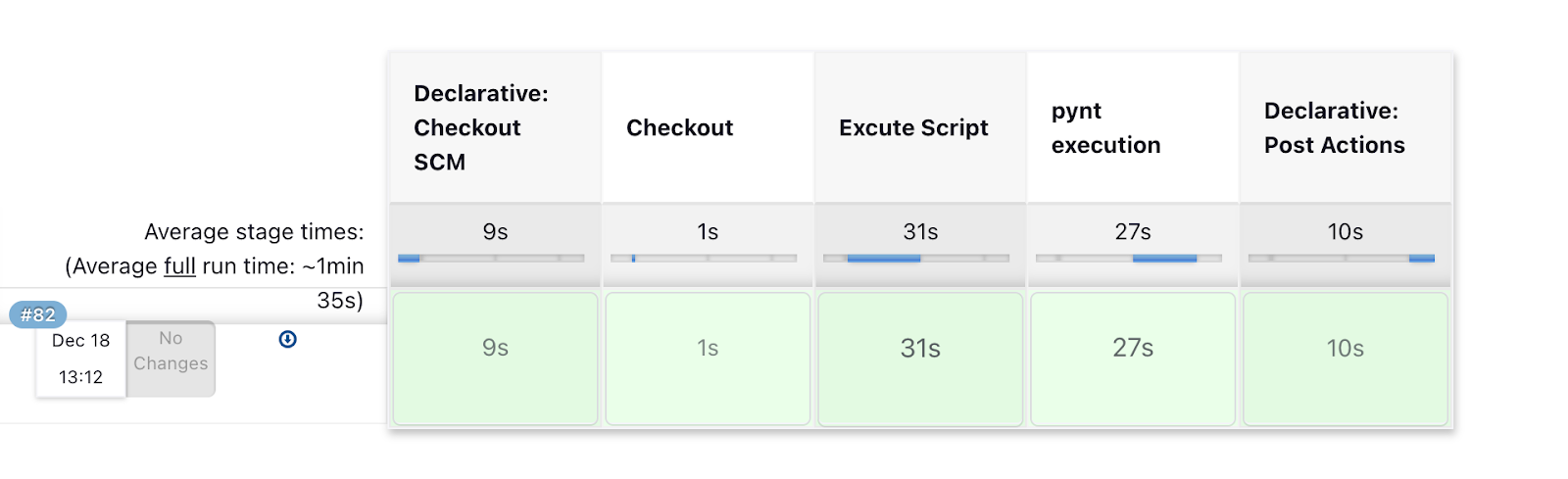
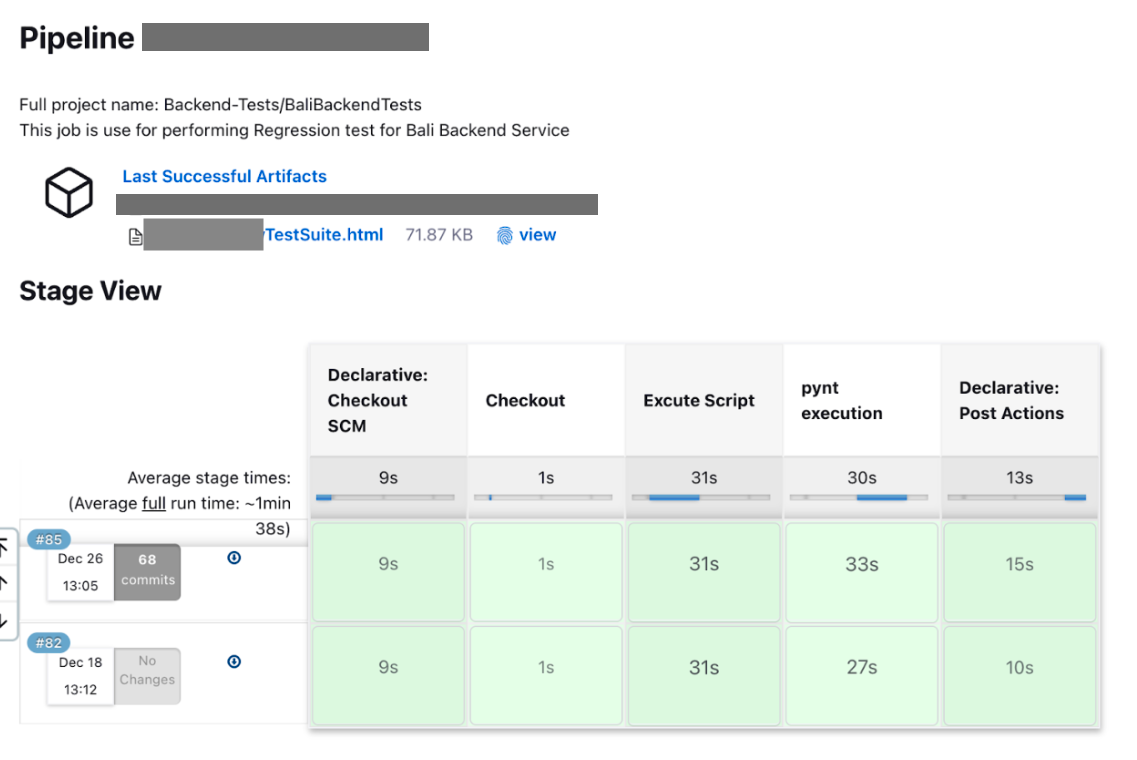
The final result for a particular job will be available in the “Last Successful Artifacts” section of the respective job after the job is completed.
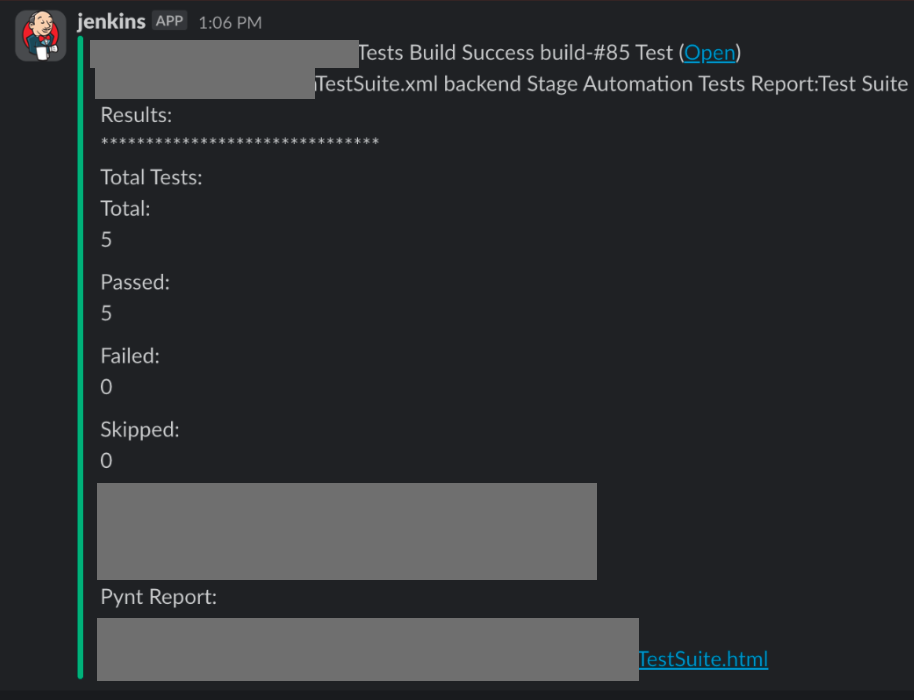
You can also directly navigate to the Pynt report through the slack messages that are posted in the respective slack channel.
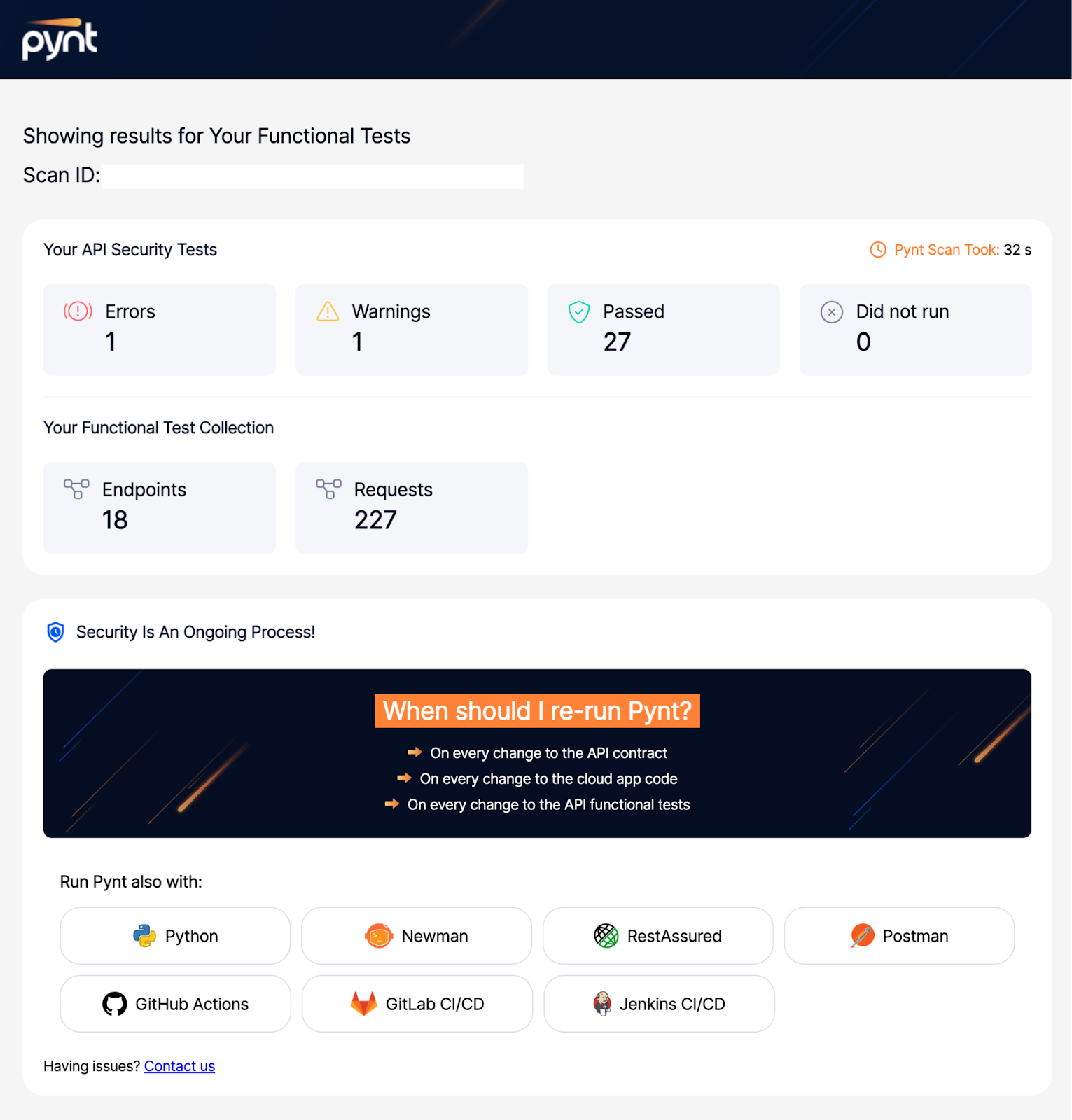
Pynt’s report
See this following sample of the report by Pynt which offers a glimpse of the test results that helps us to identify the number of Warnings, Endpoints and also the total number of requests sent.
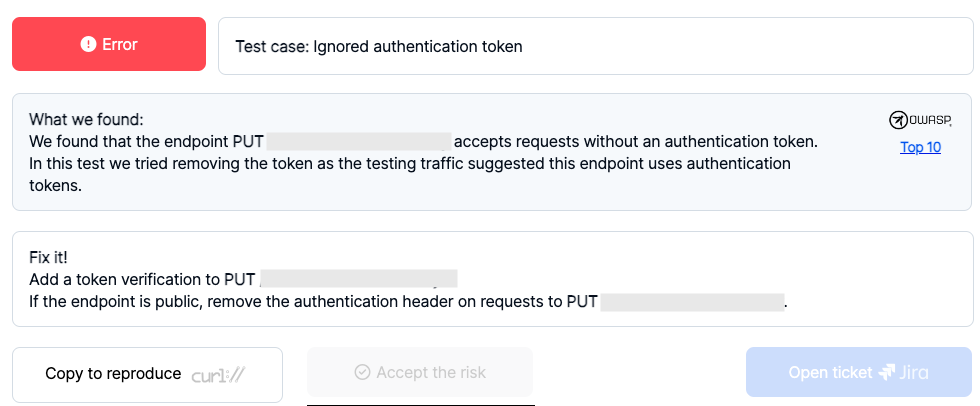
Pynt’s Vulnerability Identification and Fix Suggestion
The below provided screenshot gives a detailed explanation on the identified vulnerabilities. It also provides a brief statement on how to fix the respective issue. For some of the issues, the report will also have an option to copy the curl command of the request associated with the vulnerability. The below provided screenshots show how easy and convenient it is to reproduce the vulnerability found by Pynt.
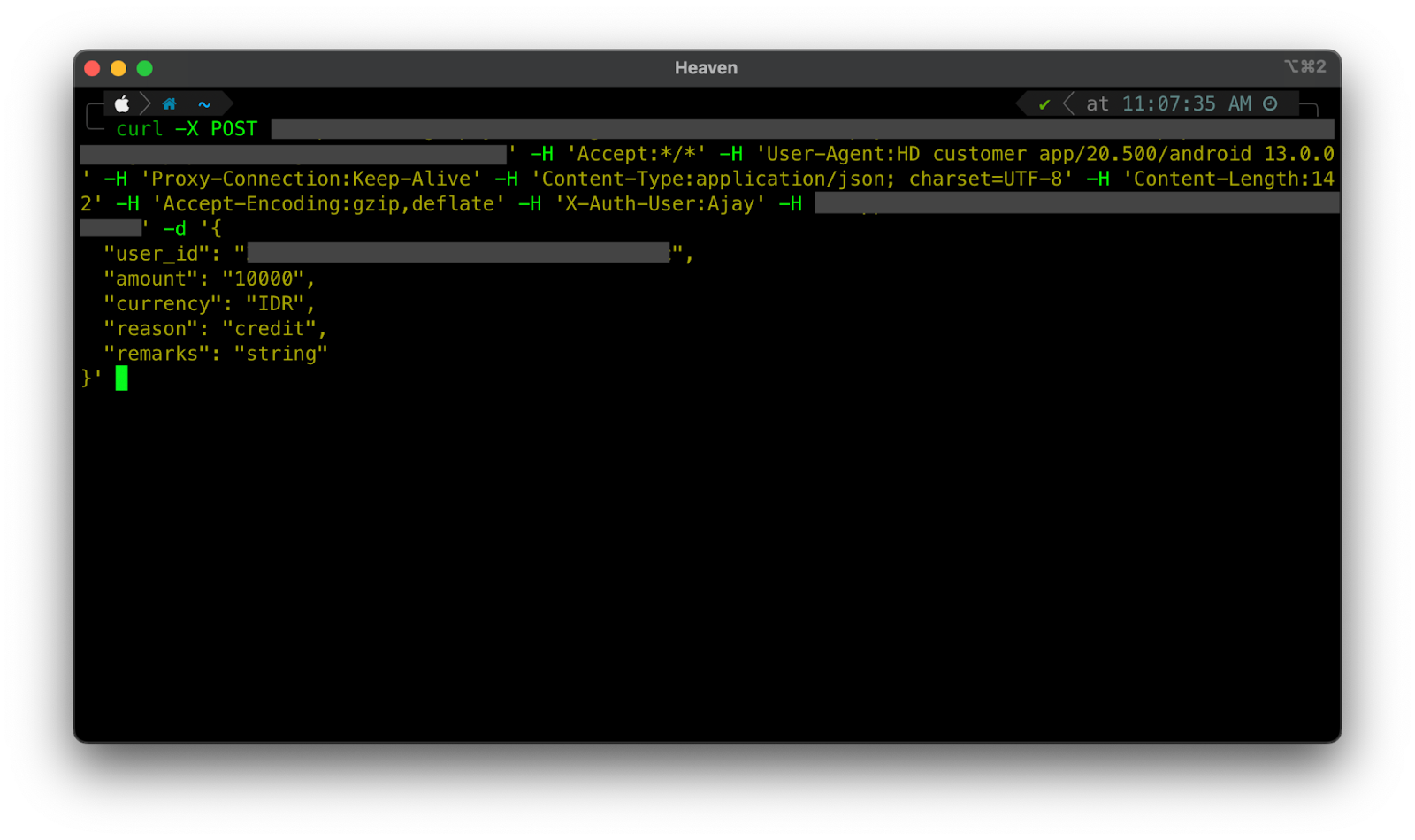
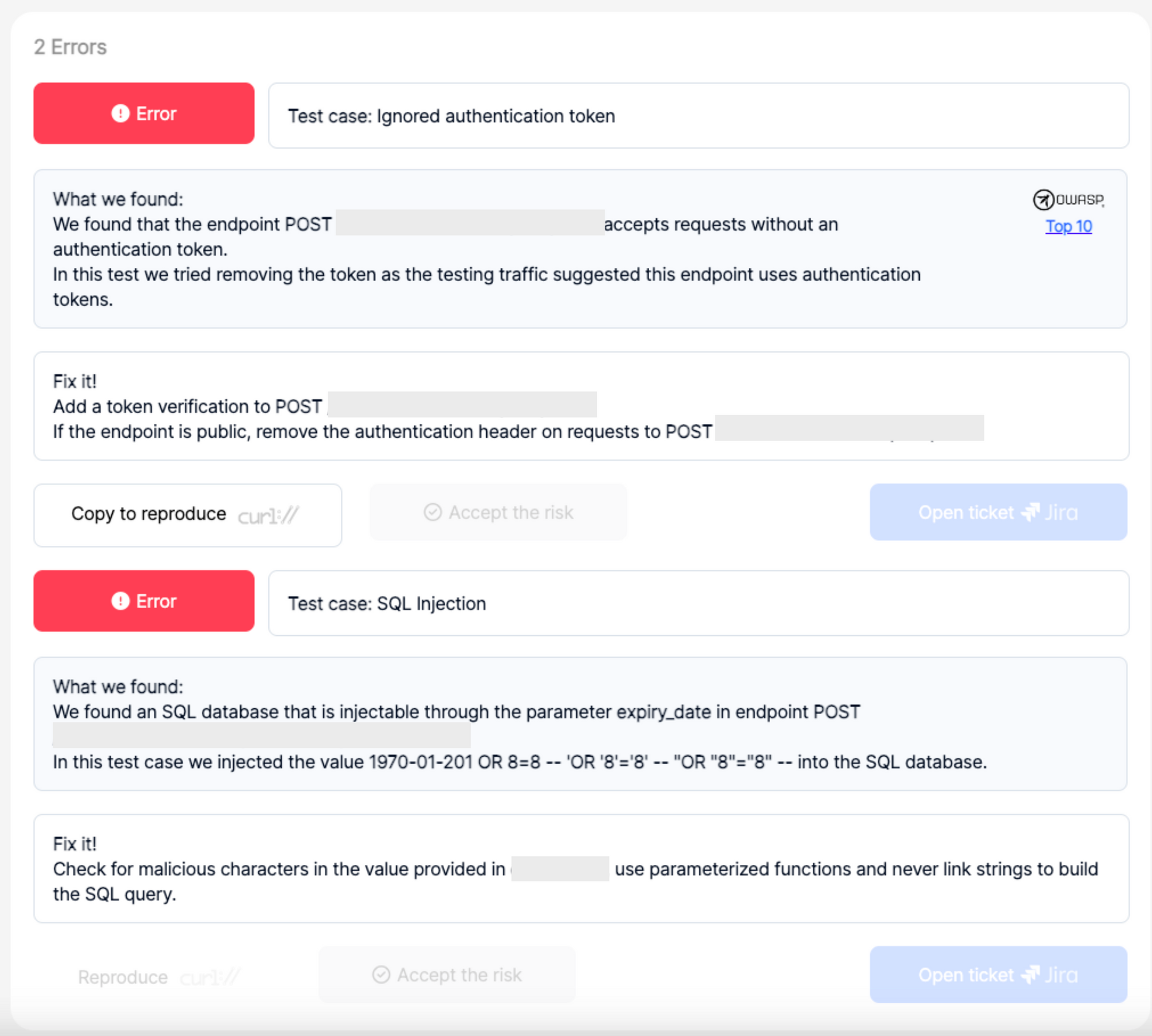
Conclusion
In conclusion, we have identified Pynt as an invaluable enhancement to Halodoc's product security infrastructure. Its seamless collaboration with QA testers and provision of insightful data have proven to be highly advantageous for our security team. Pynt's early identification of vulnerabilities has significantly fortified our security. Offering comprehensive coverage of OWASP top 10 risks, high accuracy rates, and minimal false-positive alerts, along with its effortless integration, Pynt delivers additional value that perfectly aligns with our security objectives.
Bug Bounty
Got what it takes to hack? Feel free to report a vulnerability in our assets and get yourself a reward through our bug bounty program. Find more details about policy and guidelines at https://www.halodoc.com/security
Join Us
We are always looking out for top engineering talent across all roles for our tech team. If challenging problems that drive big impact enthral you, do reach out to us at careers.india@halodoc.com.
About Halodoc
Halodoc is the number 1 Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek, and many more. We recently closed our Series D round and in total have raised around USD$100+ million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalized for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.




