Implementing AWS Shield Advanced & WAF using AWS Firewall Manager
Introduction:
Security is always a top priority at Halodoc. Apart from our regular internal and external audit, we also have a self managed Bug Bounty Program as well as private Bug Bounty Program.
This blog explains how we used AWS Firewall Manager to implement DDOS protection via AWS Shield Advanced and centrally manage WAF for the resources.
What is DOS & DDOS attack?
A denial-of-service (DoS) attack floods a server with spurious traffic, preventing genuine users from accessing a website or resource. A distributed denial-of-service (DDoS) attack is a DoS attack that uses multiple computers or machines to flood a targeted resource and attempt to impact the availability of a targeted resource.
Impact:
Both types of attacks overload a server or web application with the goal of interrupting services which has a huge impact on the business.
How does AWS Shield Advanced help us tackle DDOS attacks?
AWS Shield Advanced is a managed service that helps us protect our application against external threats, like DDoS attacks, volumetric bots, and vulnerability exploitation attempts when subscribed to AWS Shield Advanced.
In real time, L3 (Network layer) & L4 (Transport layer) attacks are auto mitigated by AWS shield Advanced, while for L7 (Application layer) we need to configure Automatic application layer DDoS mitigation first in count mode for each resource and then based on the review proceed to block mode as direct block mode at first might block even the legitimate traffic .
What is WAF?
Web Application Firewall (WAF) helps us in protecting our resources (websites and API’s) by monitoring and filtering out threats that cause potential risk to our resources.
At Halodoc, we use AWS WAF to allow or block requests before it reaches the application by defining customisable web security rules or by using AWS Managed rules.
Each request is being monitored and if the request is allowed , then it provides access to the content else it blocks with status code 403 Access Denied.
What is AWS Firewall Manager & Why to use it?
Firewall Manager (FM) is a security management service provided by AWS that allows us to centrally configure and manage firewall rules across our accounts in AWS Organisations.
With Firewall Manager, we can build firewall rules, create security policies, and enforce them in a consistent, hierarchical manner across our entire infrastructure (Single account or OU’s), from a central administrator account which helps manage the policies centrally.
Usage of Firewall Manager at Halodoc:
At Halodoc we follow a parent - child account for managing WAF in which we have an account dedicatedly for managing security services.
The Firewall Manager policies are created in the Security account (Parent account/Administrator account) and we use tag based approach (Key : Value) to attach the WAF / AWS Shield Advanced services to the AWS resources in the child account.
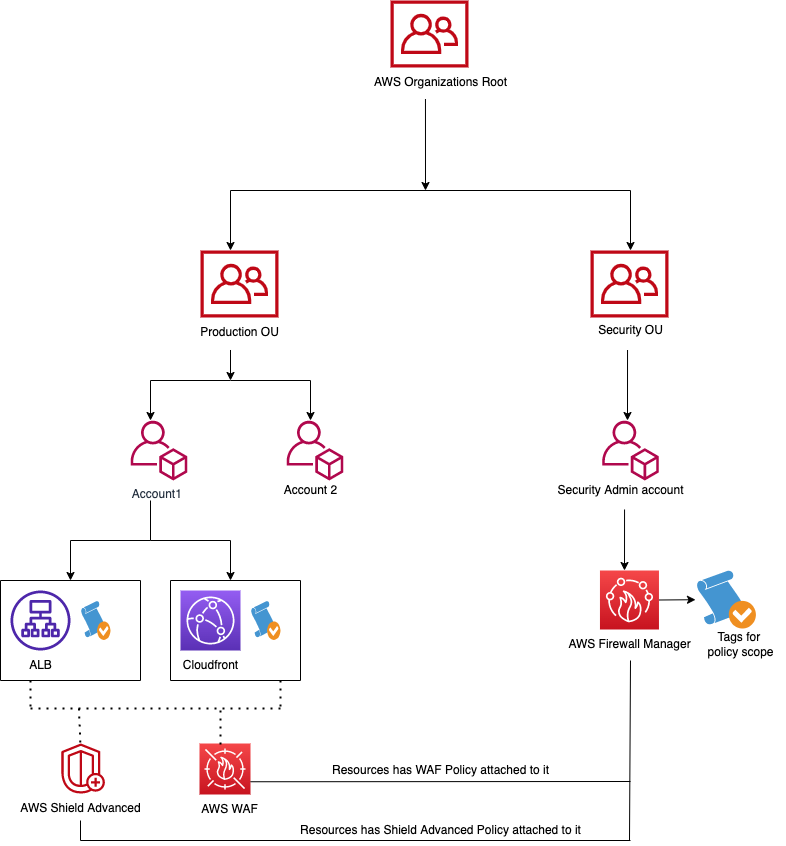
We use a general FM policy for resources that require common WAF in place and for resources which require unique Firewall Manager WAF policies we create them separately for stage and for prod.
We create our own rules for certain cases and for a few use cases we use AWS Managed WAF rules.
Steps involved in creating WAF Policies under AWS Firewall Manager in the Security account (Parent account):
- Visit AWS Firewall Manager and proceed to security policies under Firewall Manager service.
2. Create a Firewall Manager Policy by selecting the AWS services (WAF) and select the region in which the resource is present (Global for Cloudfront).
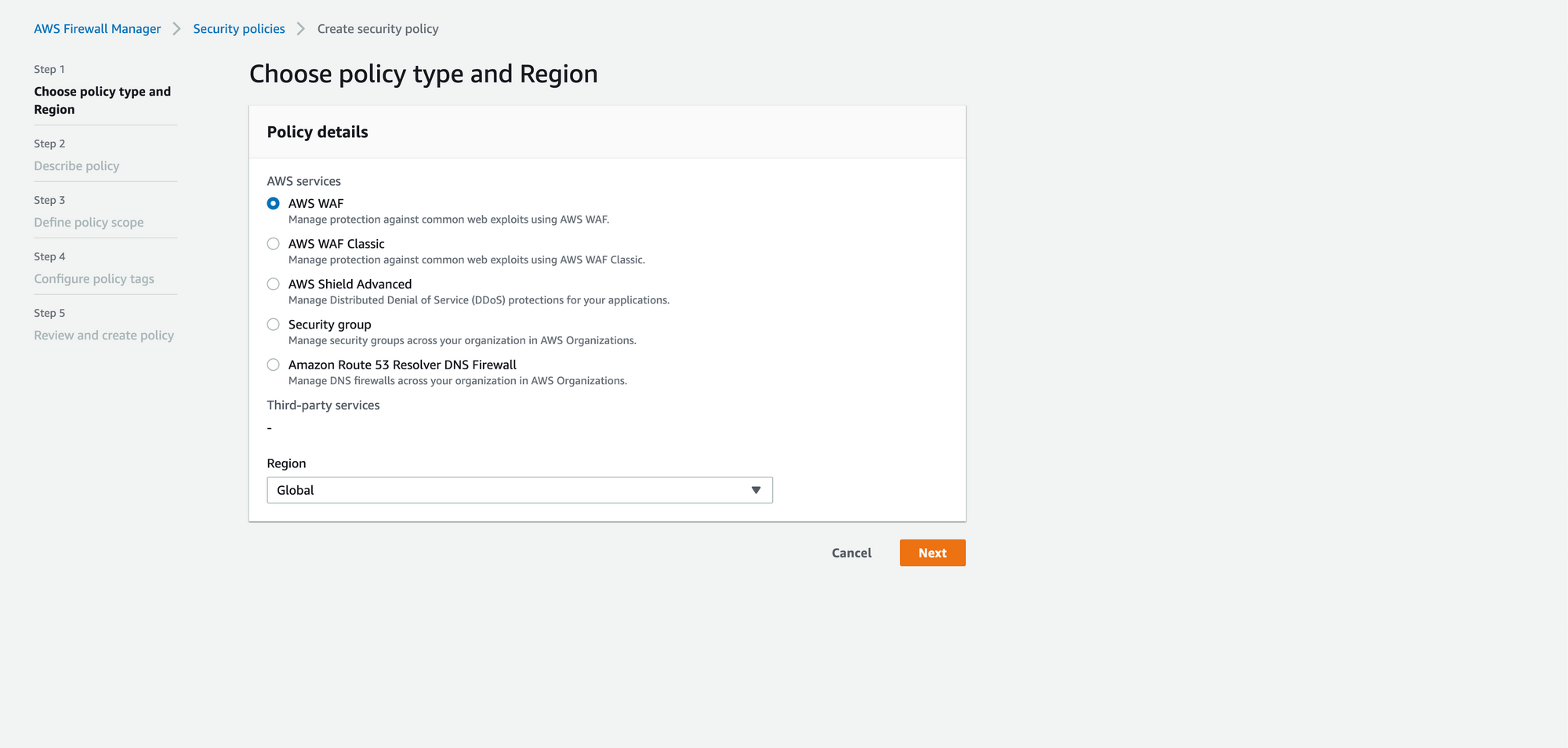
3. Next step is to associate rule groups which are needed for our use case.
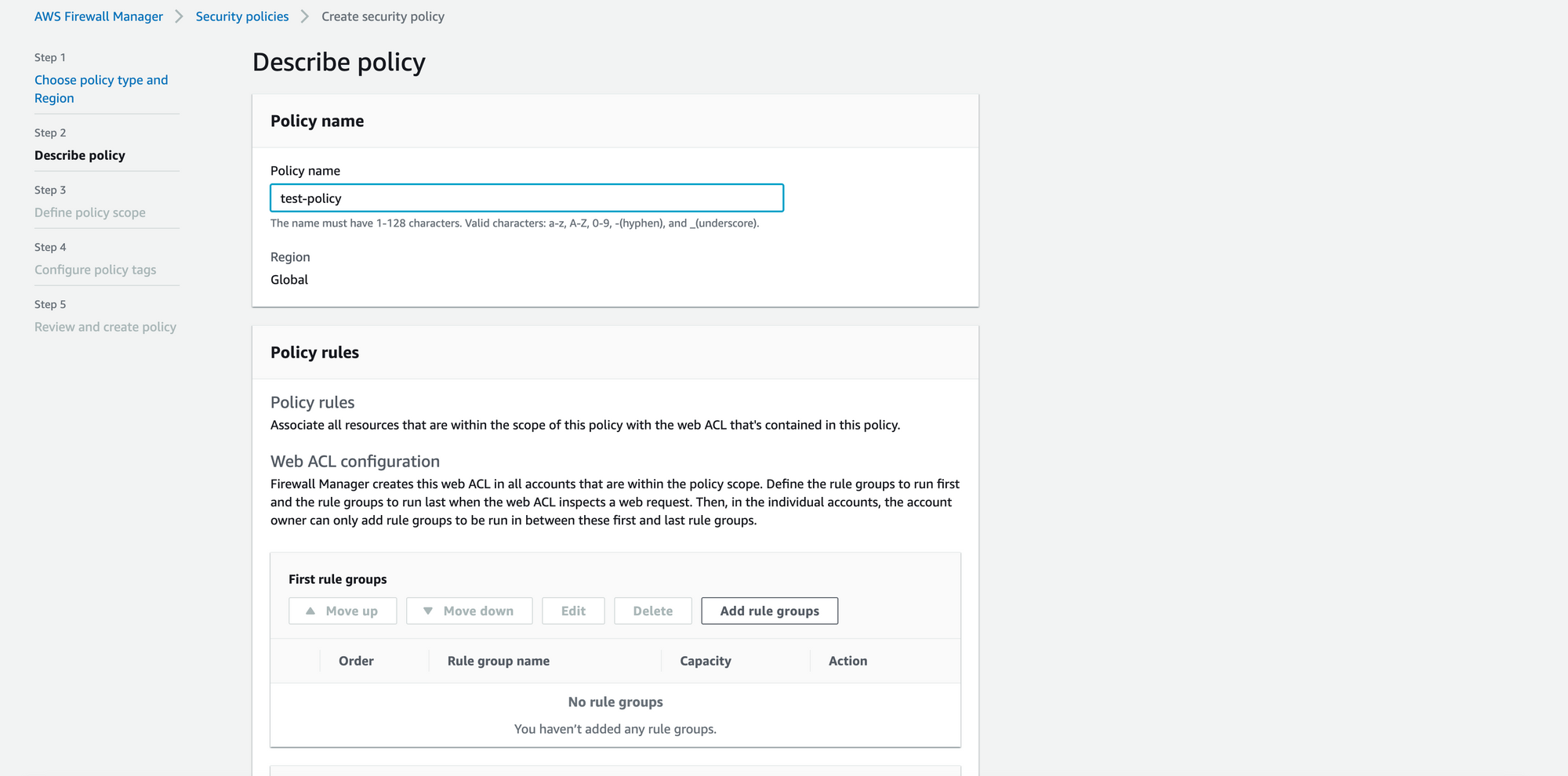
4. In the rule group we can add the custom rules created for our use case like IP whitelisting , URI / api rate limit , custom URI block etc. We can also use AWS Managed rule groups in order to use the rules which are maintained by AWS like SQL Database rules , Core rules etc. We can also subscribe to third party rule groups in order to use their rules.
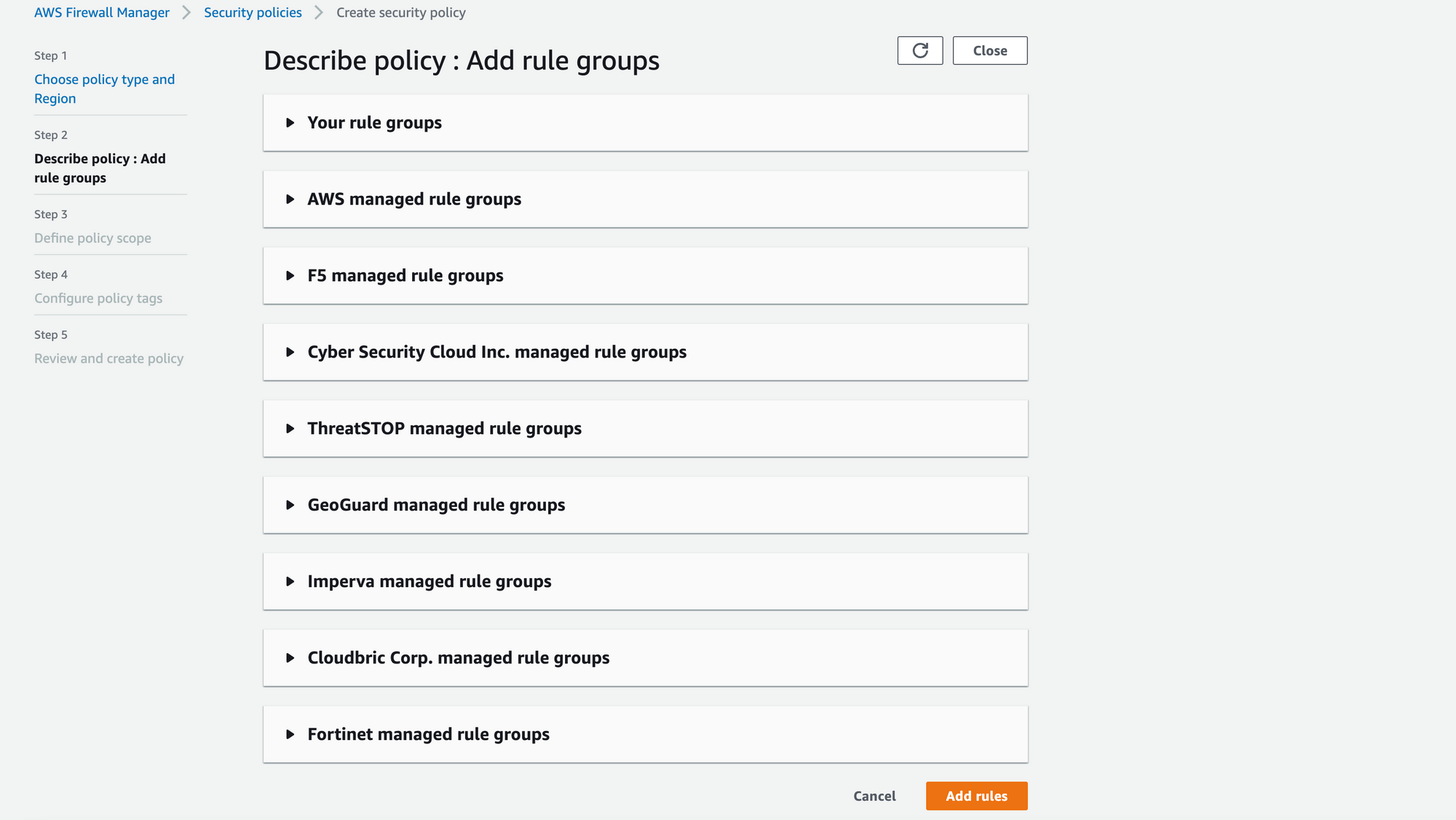
5. Once the rules are added we can perform the policy action to first identify and review the resources that don't comply with the policy rules, and then we can enable auto remediation to fix the noncompliant resources.
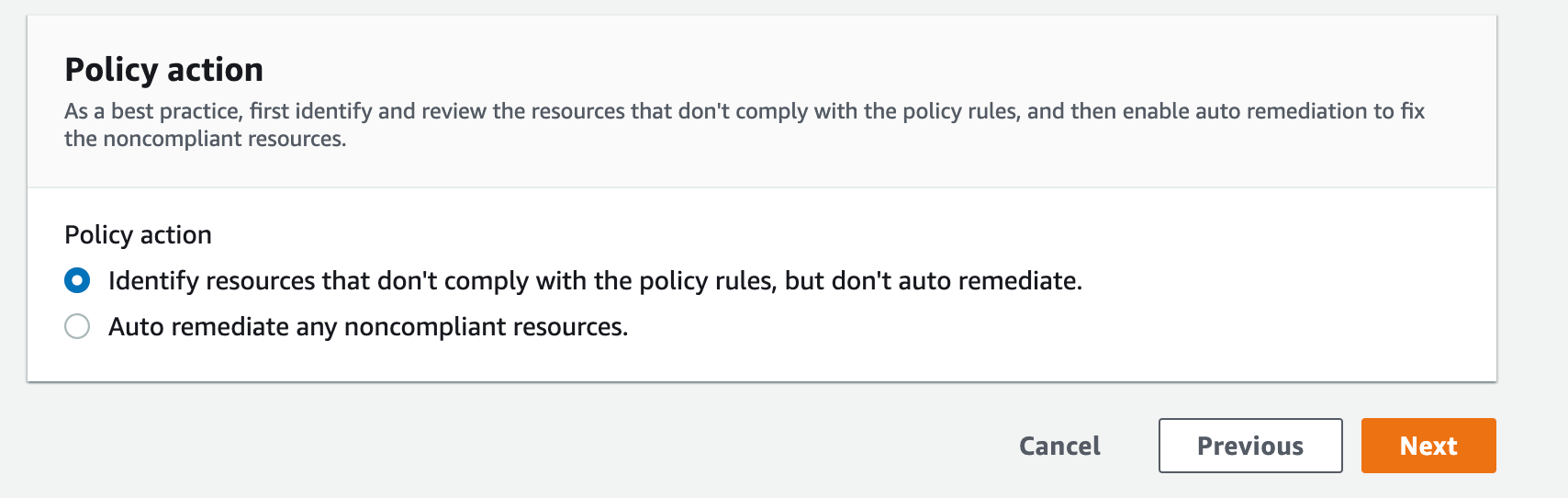
6. We can also define the policy scope for which the Firewall Manager Security Policy can be utilised based on OU’s or individual accounts. Since we are using tag based approach we can select “Include only resources that have all the specified resource tags” Specifying the tag based on the our org’s standardisation (Ex: FM as key and halodoc-<env>-<service_name>-waf-policy as value).
7. Add relevant tags for the policy and once reviewed we can create the policy.
In Child account:
- Add the created tags to the resources in the child account (here at cloudfront resource).
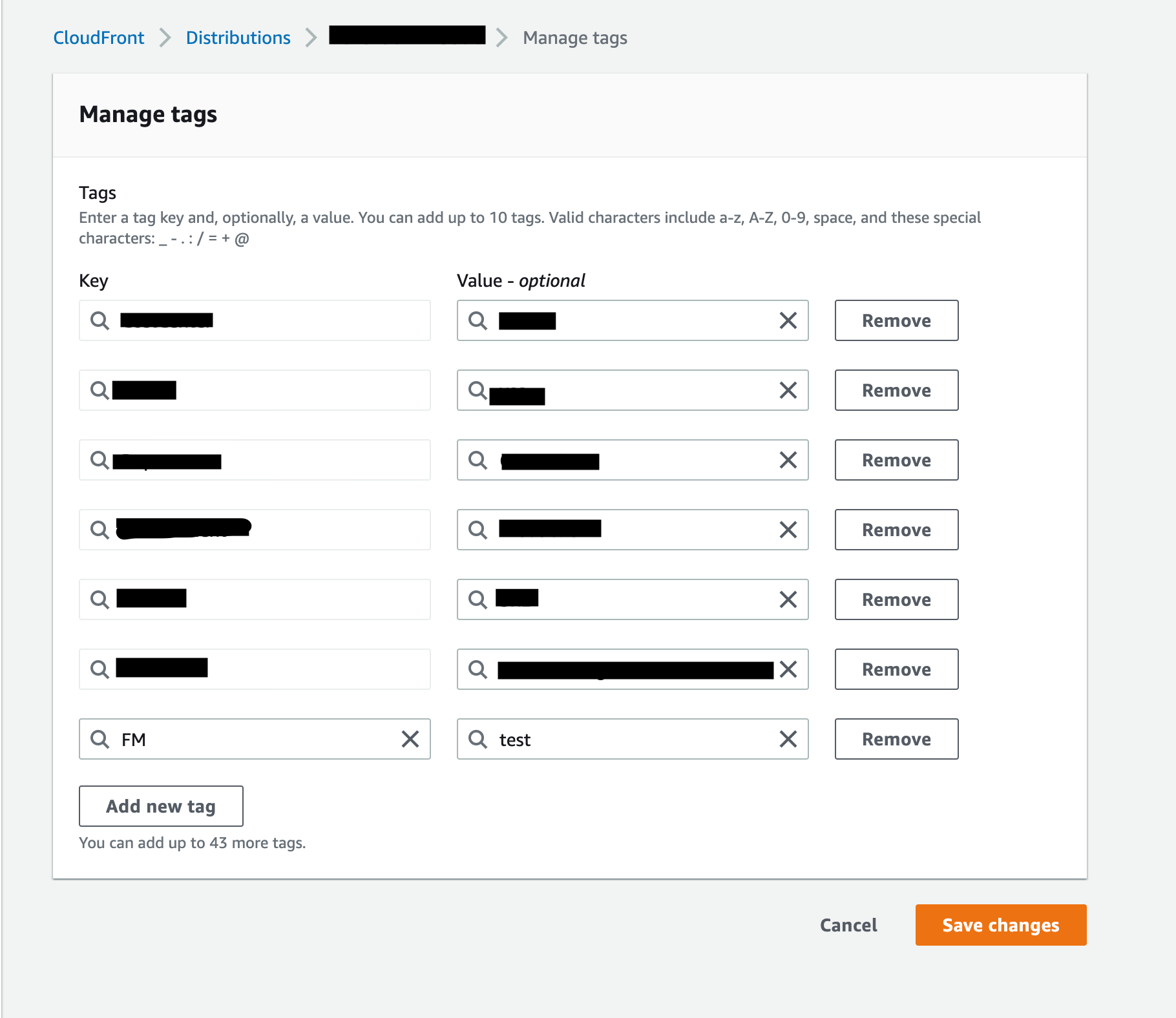
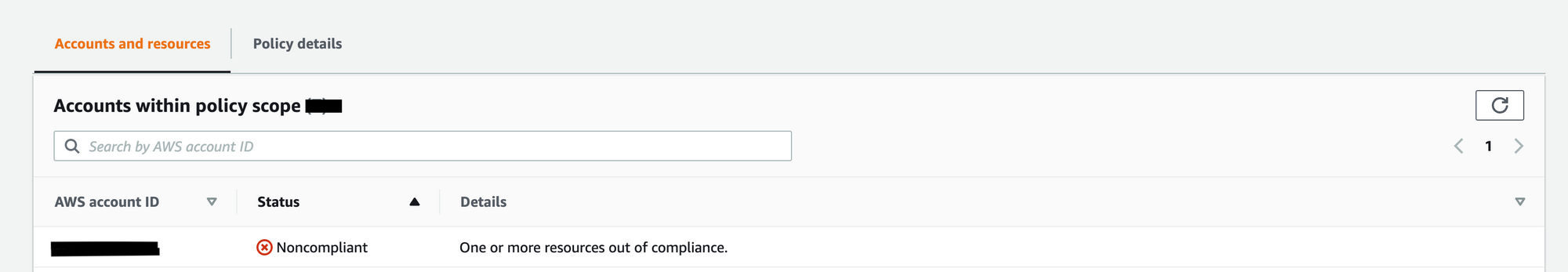
2. In the parent account we could see the account in which the resource got tagged will be identified as Non compliant and we can enable auto remediation to make it compliant.
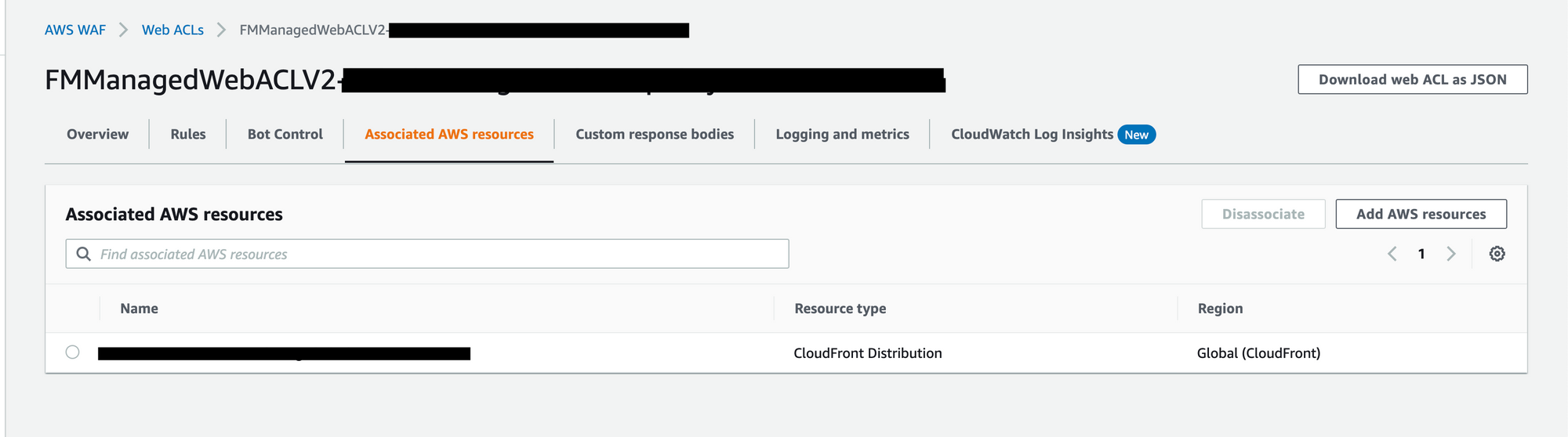
3. Once the auto remediation is made we will be able to see the WAF policy being propagated in child account with the resource attached to it.
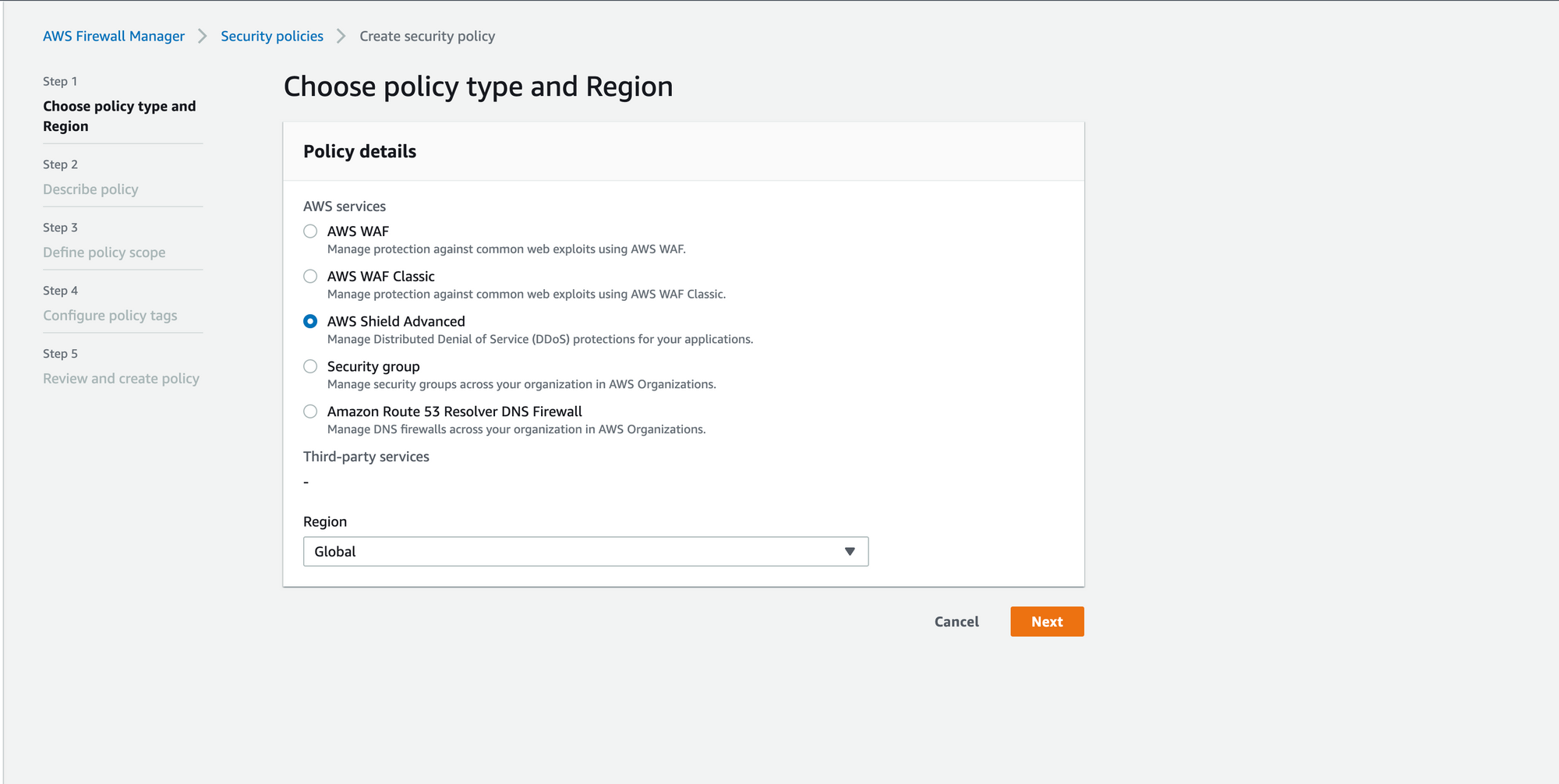
Steps involved in creating Shield Advanced Policy under AWS Firewall Manager in Security account (Parent account):
- Create the Firewall Manager policy using Shield Advanced as policy type.
2. Enable Automatic application layer DDoS mitigation with "count" mode as rule action and based on the review of the traffic , it can be changed to "block" mode.
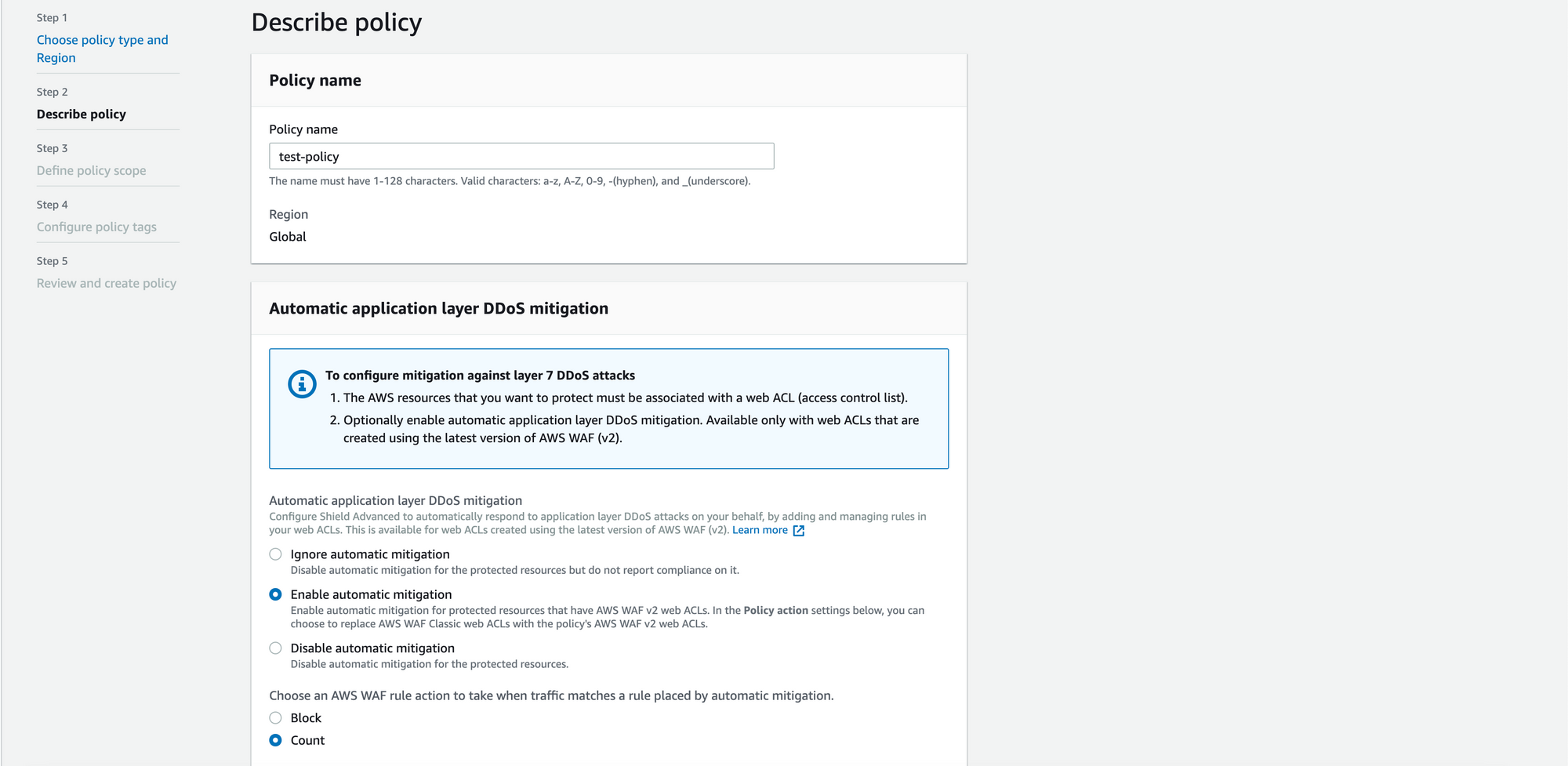
3. Follow the same steps involved in WAF policy creation (Steps 5 to Step 7).
In Child account:
Follow the same steps involved in WAF Policy creation in (Steps 1 to Steps 3).
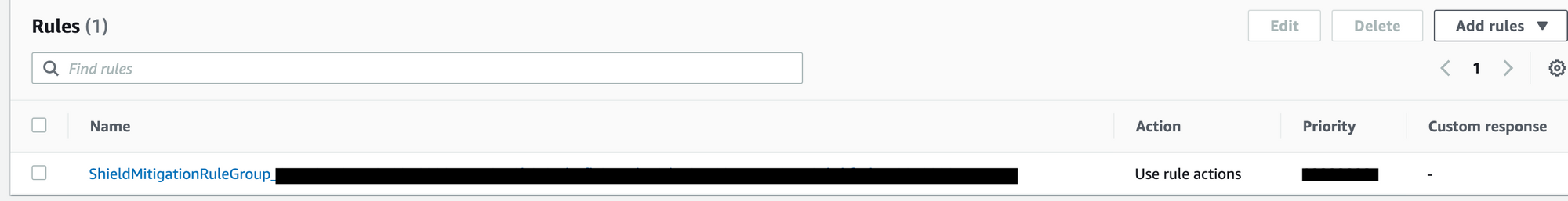
Once it's enabled we can see the ShieldMitigationRuleGroup getting enabled on the protected resource under WAF.
Benefits of using AWS Shield Advanced:
- Automatic application layer DDoS mitigation – Custom WAF rules are automatically deployed to protected resources to block malicious traffic during the detection of DDOS attack
- Health-based detection – Using Amazon Route 53 health checks with Shield Advanced provides faster detection and mitigation when the resource becomes unhealthy and also reduces the false positiveness.
- Enhanced visibility into DDoS events and attacks - Provides access to advanced, real-time metrics and reports for extensive visibility into events and attacks on our protected AWS resources.
- SRT Proactive engagement - With proactive engagement, the Shield Response Team (SRT) contacts us directly when the availability or performance of our application is affected because of a possible attack.
- Cost protection opportunities – Incase of DDOS related usage spikes, cost protection is offered to safeguard against scaling charges on protected resources.
Conclusion:
In this blog , we have provided a high-level view of how Halodoc uses Firewall manager to centralise WAF and DDOS Protection using Shield Advanced that helps continuously monitor, analyse and prevent the potential threat or attack on a real-time basis for the protected resources.
References:
https://docs.aws.amazon.com/waf/latest/developerguide/ddos-advanced-summary-capabilities.html
Join us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com.
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 4000+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek and many more. We recently closed our Series C round and in total have raised around USD$180 million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.