Securing the Organisational Perimeter: Proactive Attack Surface Management
In today’s digital landscape, organizations rapidly adopt cloud services, microservices, remote work setups, and third-party applications. While these advancements drive innovation, they also significantly expand the attack surface
Unpatched systems, exposed endpoints, misconfigurations, and shadow IT resources introduce vulnerabilities that threat actors can exploit to steal data or disrupt the business operations. This underscores the needs of having robust security control and continuous monitoring to mitigate these risks.
At Halodoc, we are leveraging the Attack Surface Management (ASM) platform as a core element of our security strategy. By leveraging tools like SOC Radar, we have improved our ability to identify, track, and address potential exposures to the internet that could be exploited by the threat actors.
In this blog, we will explain how the ASM enables our security team to proactively identify, mitigate, and prevent vulnerabilities or misconfigurations before they can be exploited.
What is ASM?
Attack Surface Management (ASM) refers to the continuous process of discovering, tracking, and protecting all digital assets, data, and systems that are accessible via the internet. The attack surface includes all external-facing assets of an organisation, which can include websites, cloud platforms, APIs, network infrastructure, applications and more.
Importance of ASM:
- Proactive Defence: ASM shifts from a reactive approach to a proactive identification by focusing on identifying, mitigating, and preventing vulnerabilities before they can be exploited by threat actors. Unlike reactive approaches, which address threats after they occur, proactive defense emphasizes continuous monitoring, preemptive actions, and enhanced visibility to minimize risks associated with an organization’s exposed assets.
- Comprehensive Visibility: ASM provides detailed inventory of the organization's external-facing assets, including misconfigurations, cloud resources, applications and third-party exposures, enabling a holistic view of our entire attack surface.
- Risk Reduction: By continuously identifying and prioritising vulnerable assets and potential threats, ASM enables us to proactively address risks and prevent threat actors from exploiting security vulnerabilities or misconfigurations to gain unauthorised access to the critical resources.
Leveraging ASM to Strengthen Security at Halodoc
As a health-tech platform, Halodoc operates in a critical space where safeguarding sensitive data is utmost important. Keeping patient information secure and protecting our systems from evolving threats is essential for maintaining resilience and earning user trust.
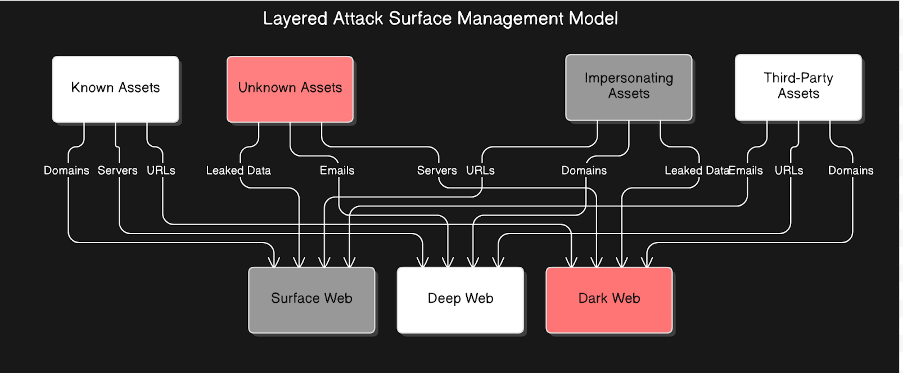
Below are some of the key challenges which we have addressed:
- Credential Leaks: Exposed credentials, whether accidentally published on public platforms or stolen and released on the dark web, can be used by threat actors to gain unauthorised access to systems, and compromise the sensitive data.
- Shadow IT: The use of unauthorised tools or services within the organization can evade standard security oversight, leaving unmonitored vulnerabilities that could create entry points for threat actors for exploitation.
- Cloud Misconfigurations: As our cloud infrastructure grows, misconfigurations like overly permissive roles or access policies can make it easier for data to be accidentally exposed or accessed without authorization, increasing the risk of data being leaked.
- Impersonation Domains: Threat actors can register typosquatted domains (e.g., "hal0doc.com" instead of "halodoc.com") to mislead users and to perform social engineering attacks such as phishing. If not addressed, these domains could pose risks to user trust and our brand reputation.
Securing the Organisational Perimeter with ASM
To address the complexities of securing our expanding infrastructure, we utilise SOC Radar, a comprehensive threat intelligence platform with integrated ASM capabilities. SOC Radar provides real-time visibility into our attack surface, enabling us to identify and mitigate risks before exploitation. By continuously scanning for potential threats across our applications, network, and third-party services, we have adopted a proactive approach to defending against the threat actors and safeguarding both our platform and infrastructure
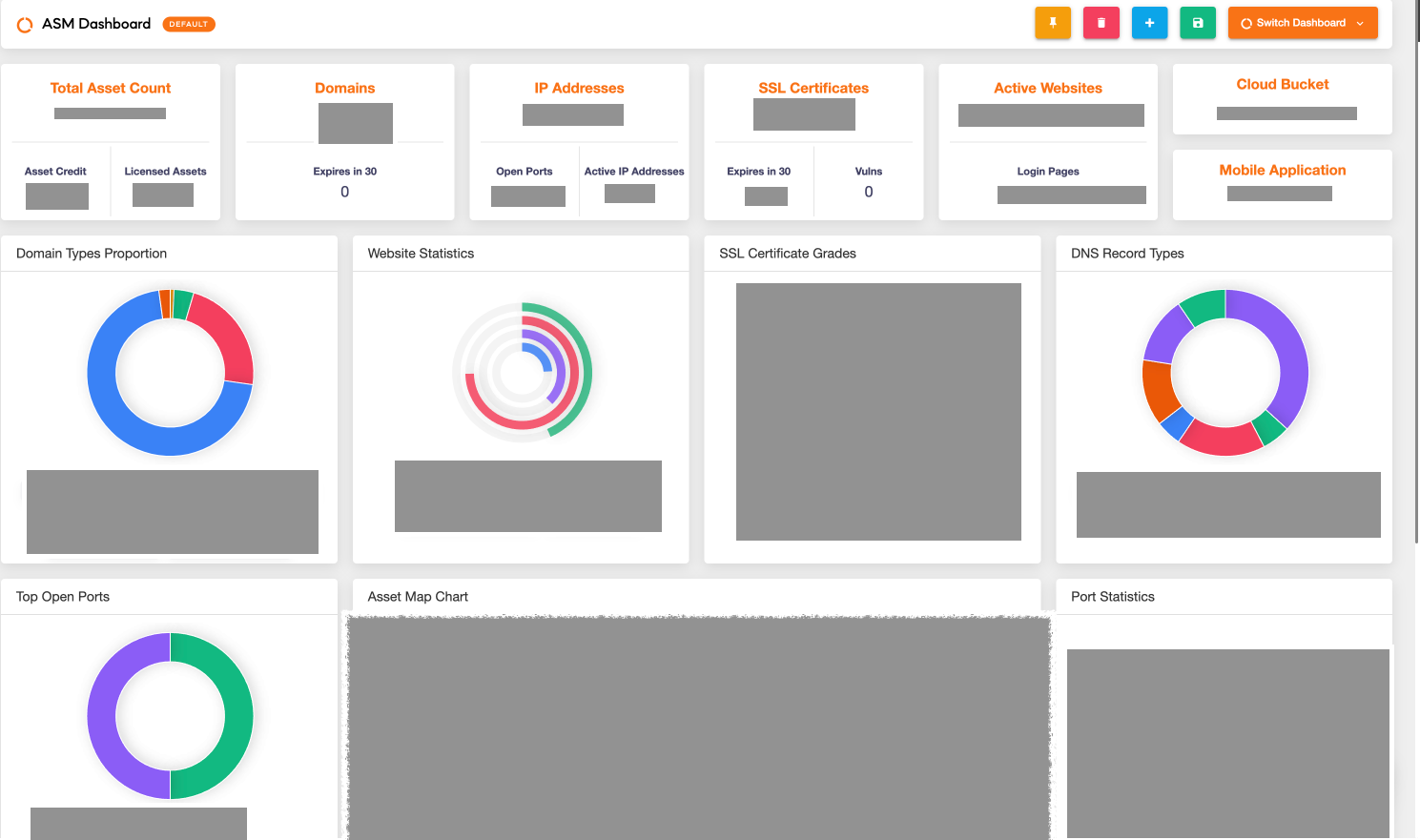
Key Benefits and Features of Our ASM Strategy
Our ASM offers several key benefits that enhance our security posture and play a vital role in protecting our environment. The essential features and advantages includes:
- Real-Time Threat Intelligence: SOC Radar’s continuous monitoring and threat intelligence enable us to proactively identify security vulnerabilities and misconfigurations. This proactive approach addresses potential issues before escalation, minimising exposure and enhancing our response times.
- Automated Asset Discovery and Classification: Through automated asset discovery, we can identify every component of our digital infrastructure. By classifying assets based on their risk profile and sensitivity, we can prioritize security measures to protect high-risk assets and sensitive information effectively.
- Visibility Into the Full Attack Surface: ASM ensures comprehensive visibility across the entire attack surface. By continuously monitoring external-facing systems including third-party services, cloud platforms, and applications, we can proactively detect and address vulnerabilities before they can be exploited by the threat actors.
From Risk to Resolution: ASM in Action at Halodoc
At Halodoc, ASM plays a crucial role in addressing the challenges of an expanding digital environment. Using SOC Radar, we continuously identify potential risks, monitor emerging threats, and mitigate vulnerabilities before they can be exploited. See these following key scenarios demonstrating the security playbooks implemented within our ASM module.
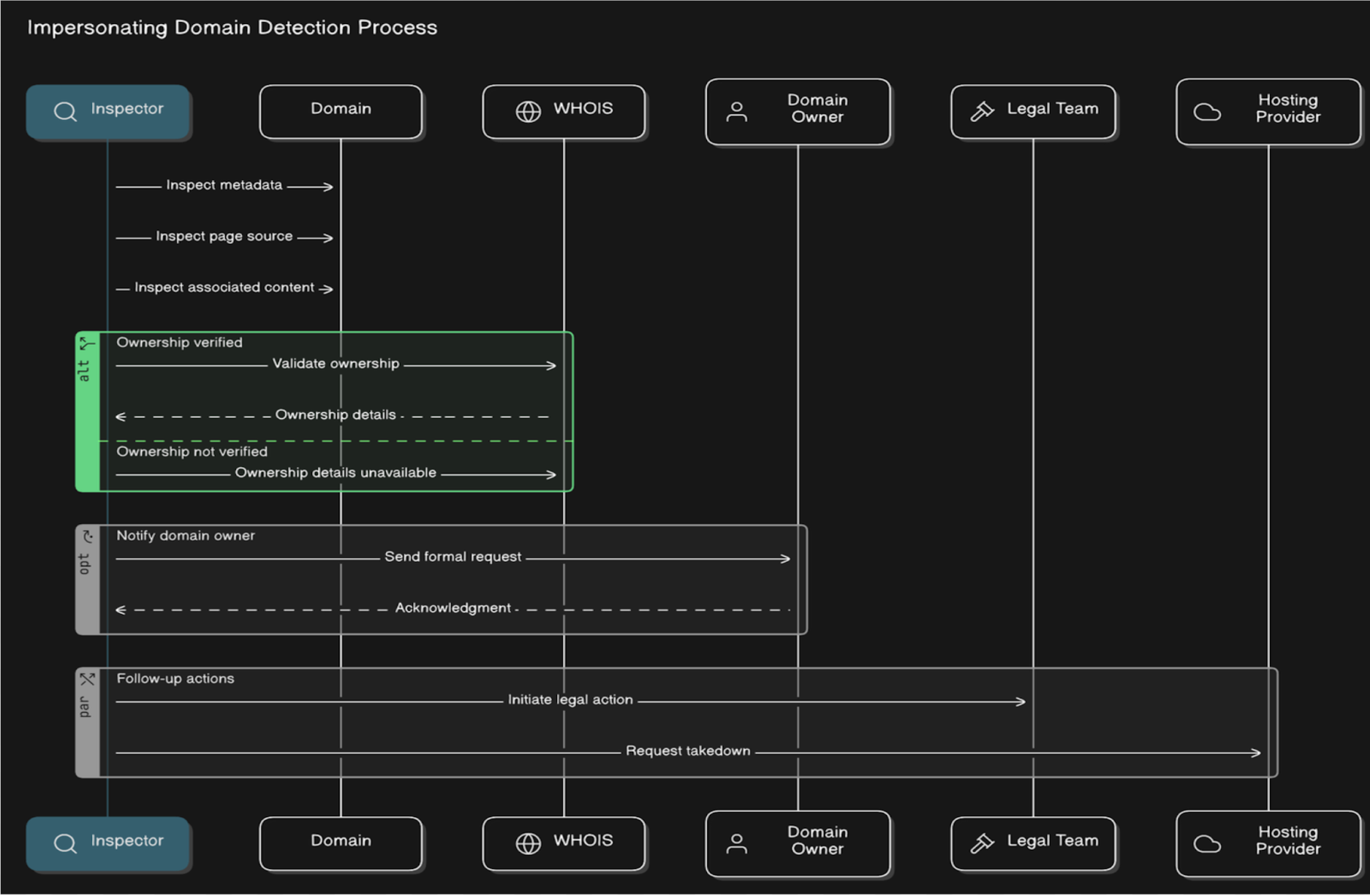
1. Detecting Impersonating Domains with ASM
One critical area is doing the detection and mitigation of risks posed by domain impersonation. Threat actors often register domains that closely resemble legitimate company domains to trick users, conduct phishing attacks, or distribute malware. ASM allows us to continuously monitor domain registrations, identify suspicious domain, and take corrective action to prevent these threats from impacting our organization.
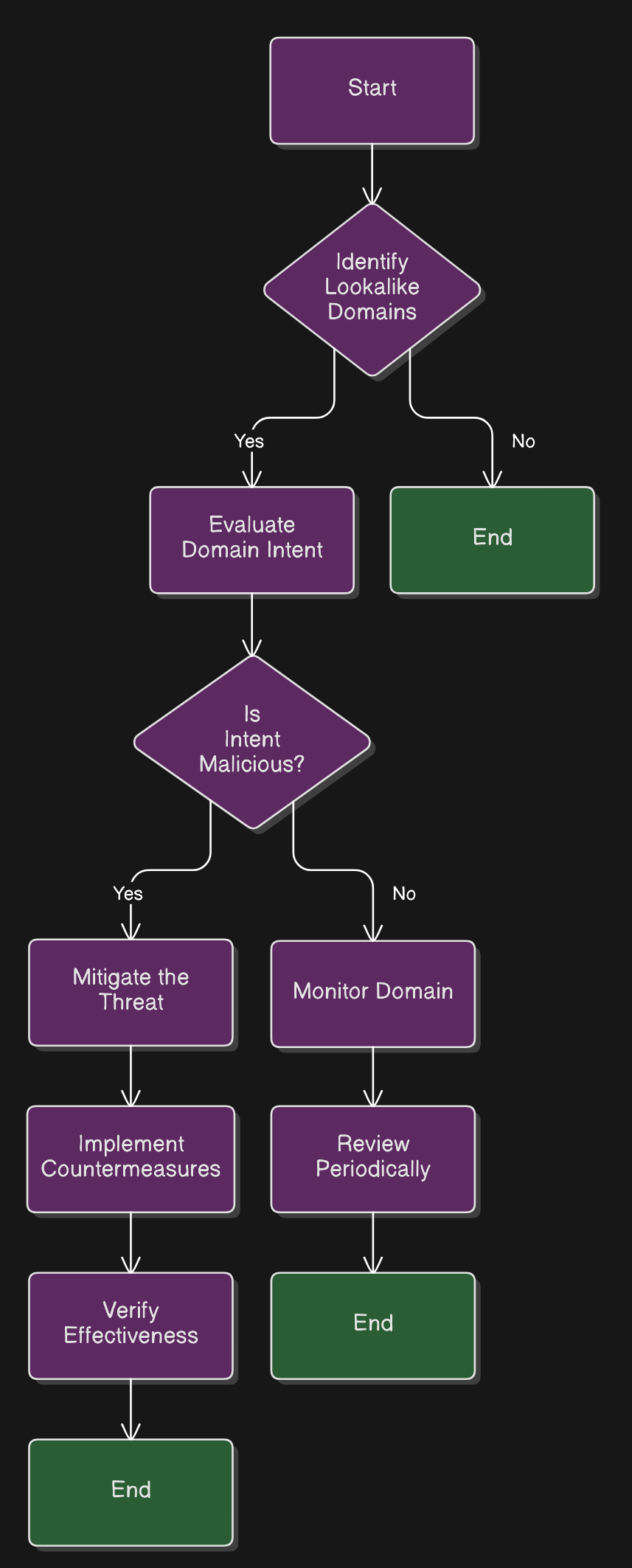
- Proactively Identify Suspicious Domains: SOC Radar continuously scans for newly registered typosquatted domains that mimic our brand, such as using misspelled versions of our primary domain (e.g., "haladoc.com" or "hal0doc.com").
- Evaluate Domain Risks: Each detected domain is analyzed to determine its intent. Indicators like active phishing campaigns, associated malware, or parked pages are flagged for immediate investigation.
- Mitigate the Threat: Upon confirming an impersonating domain, our team collaborates with registrars or hosting providers to facilitate the takedown. In some cases, we also use legal channels to prevent further misuse.
- Active monitoring: Once the domain is confirmed malicious, our team adds the domain across different security tools as IOC’s (Indicators of Compromise) and enables continuous monitoring.
This proactive approach ensures that our brand reputation and shields our users from impersonation attacks.
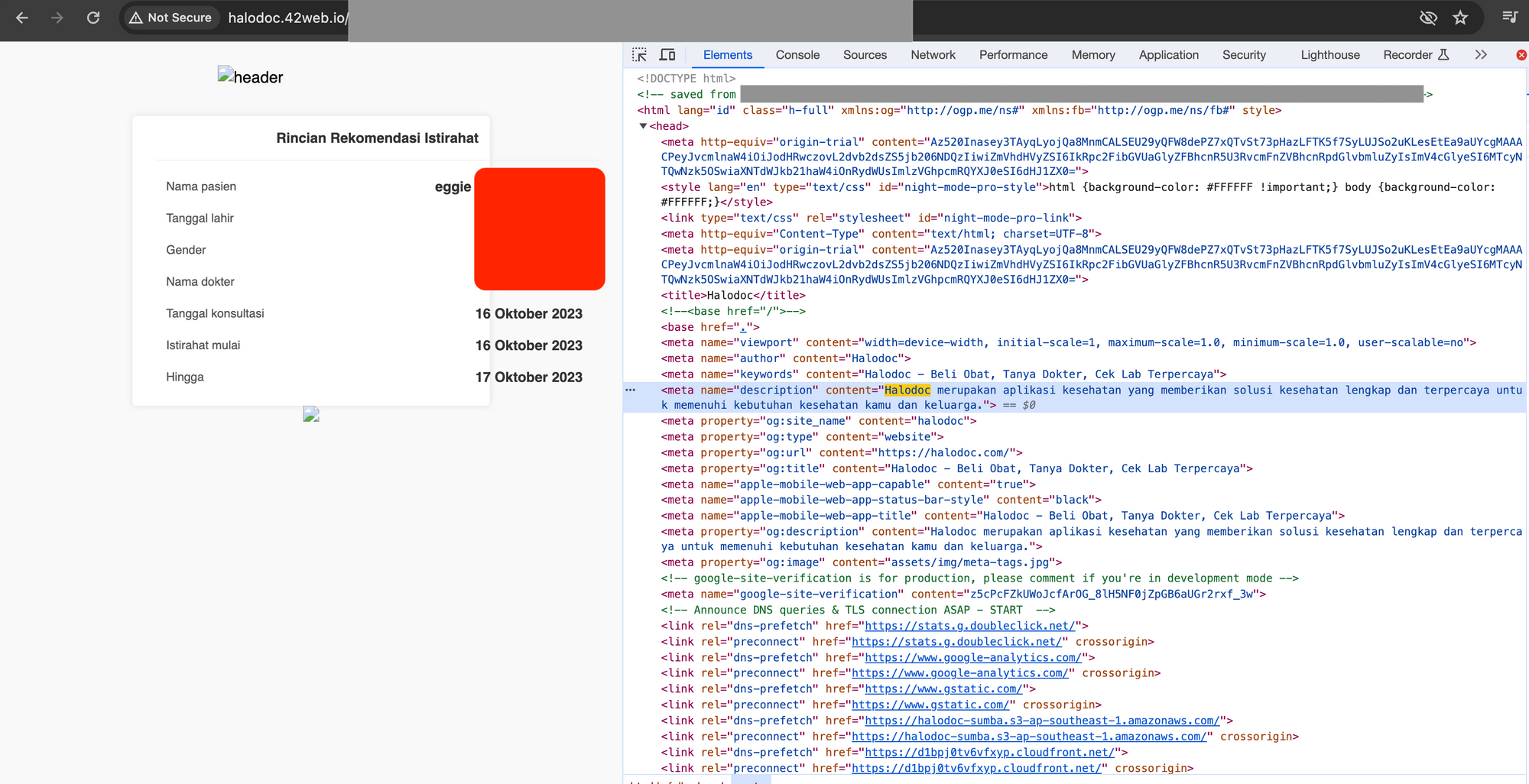
Post Identification of Domains
To address impersonating domains, our approach involves thorough examination and prompt action:
- Data Inspection: We closely examine suspected domains by inspecting their metadata, page source (using tools like "Inspect Code"), and associated content. This process helps us determine whether the domain is attempting to impersonate our legitimate services or tricking the users.
- Verification of Ownership: Post-identification, we validate the ownership of the impersonating domain using WHOIS data or other domain registration records. This helps us determine if the domain belongs to a known entity or unknown entities.
3. Communication with Domain Owners: Once impersonation is confirmed, we issue formal notifications to the domain owners, urging them to take immediate steps to remove or alter the domain.
By following this structured approach, we effectively address the risks of domain impersonation, reinforcing our focus on user safety and data protection.
2.Proactive Prevention of Credential leakage
Credential leakage is a critical threat, as compromised credentials can provide unauthorised access to sensitive systems. This highlights the importance of prompt detection and immediate containment. Below is an overview of how ASM helps prevent credential breaches:
- Continuous Credential Surveillance: SOC Radar monitors various public platforms, such as GitHub and Pastebin, as well as the dark web, for any instances of Halodoc-related credentials. This continuous monitoring ensures that any leaked credentials are detected as soon as they appear online, allowing us to do the immediate action for containment.
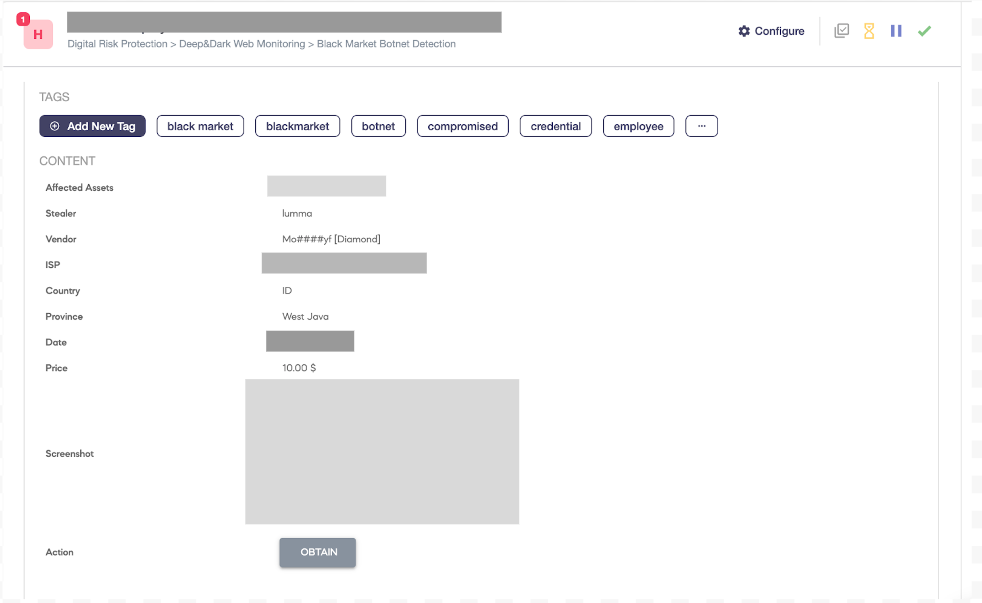
- Prompt Verification: Upon detecting a credential leak, our team verifies the authenticity and impact of the breach by cross-referencing the leaked credentials with our internal systems. We assess whether the compromised credentials belong to privilege accounts, such as root accounts, or are commonly reused across different services, increasing the attack surface and potential risks. This process helps determine the severity and immediate steps required to contain the breach
- Swift Action: Once verification is completed, we take the following steps:
a. Revoke or reset the compromised credentials for containment to prevent unauthorised access
b. Notify the impacted users or teams on the credential leakage case and as an extra precaution we will also monitor the user activity for any unusual or unauthorised action related to the impacted accounts.
c. Impose temporary access restrictions on sensitive systems if necessary.
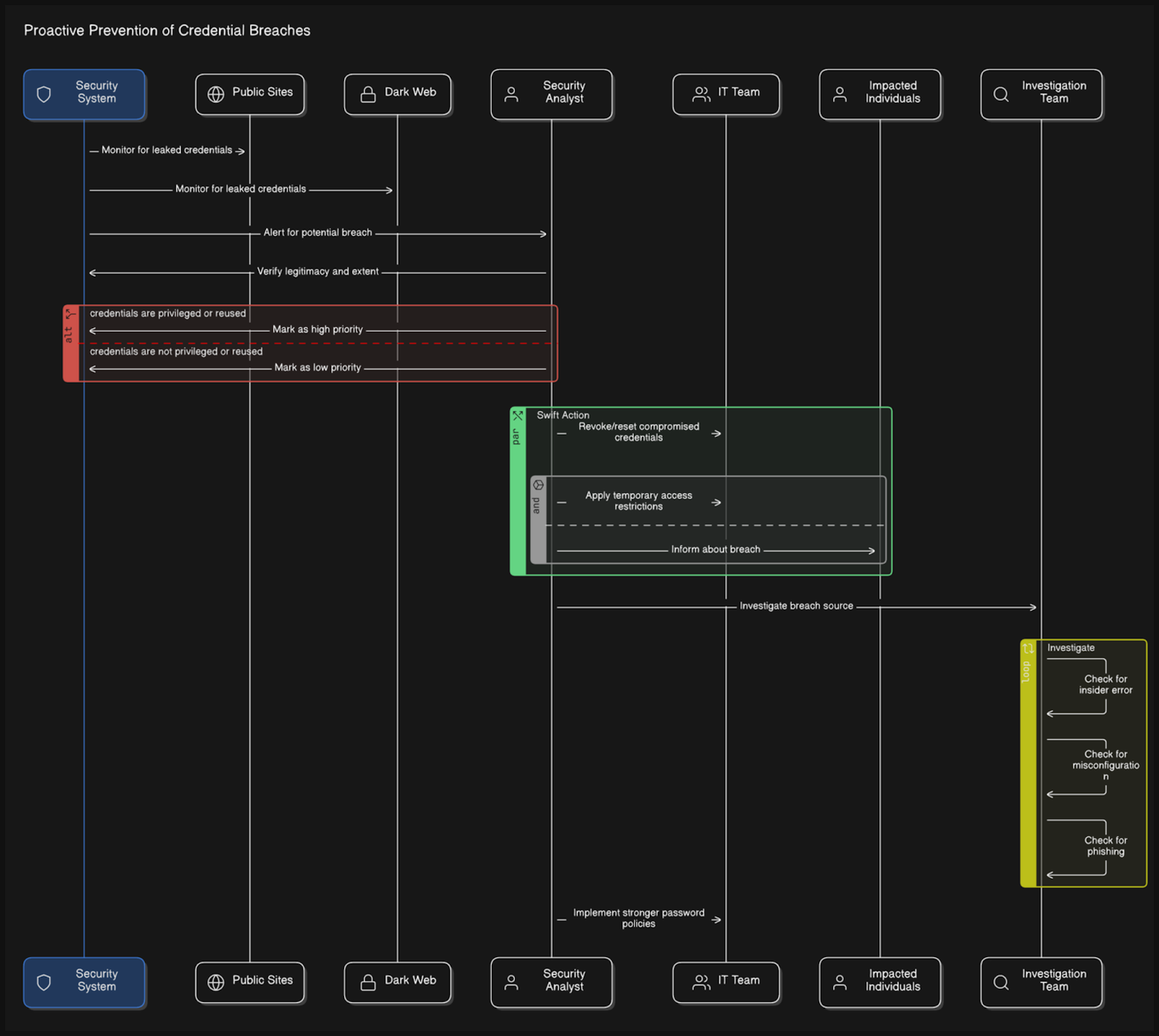
- Root Cause Examination: After addressing the incident, we conduct analysis to identify the underlying cause of the leak. This analysis covers potential factors such as human error, exploited vulnerabilities, or some phishing attacks. The findings will be used to strengthen our defenses and reduce the likelihood of similar incidents in the future.
- Enhanced Preventive Measures: Based on the analysis, we will improve our security measures, such as stricter password management policies, mandatory multi-factor authentication (MFA), and regular security awareness training for employees
By incorporating credential monitoring into our ASM processes, we reduce the likelihood of security incidents related to the credential leakage that potentially can compromise our user data or disrupt our business operations.
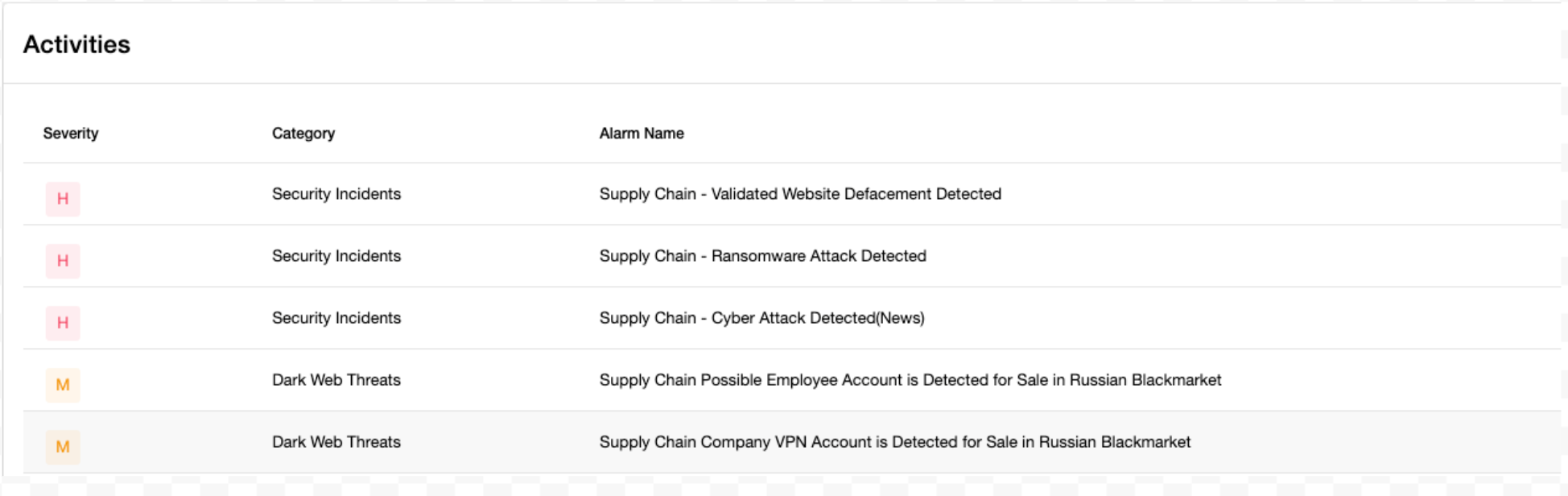
3.Expanding ASM with ThreatFusion: Managing Supply Chain and Third-Party Security
The attack surface extends beyond our internal resources and includes the loophole from the third-party software and emerging threats on the dark web. By utilising ThreatFusion, we improve our capabilities with practical insights related to supply chain vulnerabilities and cybercriminal activities, strengthening our security posture against the evolving threats.
Addressing Supply Chain Risks with External Intelligence
Integrating third-party tools, such as Chrome extensions, Slack applications, and APIs, is essential for operational efficiency but may unintentionally expose sensitive information.
How ThreatFusion Strengthens Supply Chain & Third-Party Security
- External Risk Evaluations: Continuously monitors the security posture of interconnected applications to identify vulnerabilities in the early stage.
- Threat Prioritisation: Enables security team to focus on remediating risks based on their potential impact, minimising the likelihood of exploitation through compromised external tools from the third party.
- Early Leak Detection: Conducts continuous scanning of public and dark web platforms for credentials, tokens, and other leaked data related to third-party services, ensuring early identification of potential breaches.
- Risk Assessment and Prioritisation: Analyses the criticality of third-party leaks, enabling targeted mitigation efforts for high-risk exposures.
- Vendor Collaboration: Coordinates promptly with affected third parties upon detecting a leak to resolve the issue such as revoking the compromised credentials, removing the sensitive data in the third party infrastructure and implementing stricter security controls.
4.Combating Rogue Applications
Rogue applications, whether unauthorised or malicious, pose a significant challenge to our digital infrastructure. These applications can be altered to exploit security vulnerabilities, potentially tricking the users to compromise their sensitive data and potentially impacting our brand reputation. Effectively addressing these risks is critical to safeguarding our systems and maintaining trust to our customers.
How ASM Identifies Rogue Applications
Our ASM strategy includes tools and processes designed to identify and address the rogue applications effectively :
- Automated Discovery: Scans external systems and third-party app stores to identify unauthorised or potentially malicious applications.
- Real-Time Monitoring: Continuously monitor the activity of the applications to detect unusual or unauthorised behaviors.
- Comprehensive Visibility: Provides a clear overview of external-facing systems, enabling us to locate rogue applications and evaluate their risks.

By identifying and removing rogue applications, we address our key challenges and enhance our overall attack surface management strategy. This proactive approach secures our attack surface and strengthens defenses against emerging threats.
Conclusion
At Halodoc, our proactive cybersecurity strategy adopts Attack Surface Management (ASM), enabling us to identify and address risks before they are exploited. By leveraging tools like SOC Radar, we ensure continuous monitoring of our digital presence, mitigating threats such as domain impersonation, credential leakage, and rogue applications.
Any organization can adopt the ASM platform to reduce their attack surface by focusing on continuous monitoring, automated risk detection, and effective prioritisation. Real-time visibility into externally facing assets allows us to detect vulnerabilities early, whether caused by security vulnerabilities or misconfigurations. Tools like SOC Radar provide actionable insights to strengthen our overall security posture.
ASM empowers security teams to navigate the dynamic threat landscape by minimising exploitable entry points, safeguarding sensitive data, and reducing business disruptions. Whether in health-tech or other industries, ASM is essential for adapting to the continuously changing digital landscape.
References
- https://medium.com/@micallst/attack-surface-management-youre-probably-doing-it-wrong-608719da1cab
- https://rodelllemit.medium.com/introducing-to-attack-surface-management-asm-ad7bd589dd15
- https://socradar.io/wp-content/uploads/2023/12/socradar-whitepaper-whats-asm.pdf
Bug Bounty
Got what it takes to hack? Feel free to report a vulnerability in our assets and get yourself a reward through our bug bounty program. Find more details about policy and guidelines at https://www.halodoc.com/security
Join Us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek, and many more. We recently closed our Series D round and in total have raised around USD$100+ million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.




