Introduction to Common Web Vulnerabilities and Exposures
An overview of common web vulnerabilities and exposures (CVEs)
At Halodoc, we recognise the importance of protecting patient information and data security. That's why we've invested in a range of security measures, from regular vulnerability testing to employee training and continuous improvement. We know that the stakes are high when it comes to web security, and we're committed to providing our users with the peace of mind they need to trust us with their healthcare needs.
But what exactly are these vulnerabilities and exposures that we're so concerned about? In this blog post, we'll explore some of the most common web security issues that can put your data at risk, and provide you with tips on how to protect yourself and your information."
A vulnerability is a weakness that can be exploited by cybercriminals to gain unauthorised access to a computer system. After exploiting a vulnerability, a cyberattack can run malicious code, install malware, and even steal sensitive data.
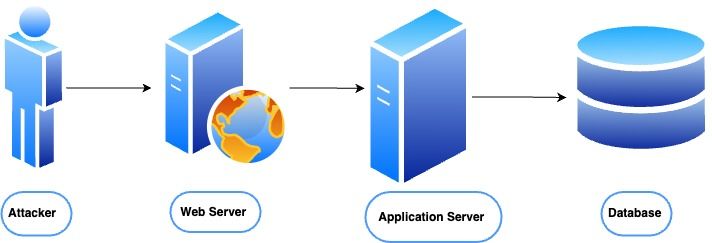
In this diagram, the attacker is outside the system and is attempting to exploit vulnerabilities in the web server, application server, or database to gain unauthorised access or cause harm to the system. The web server is responsible for handling incoming requests and responses, and may be vulnerable to attacks such as SQL injection or cross-site scripting (XSS). The application server is responsible for processing application logic and may be vulnerable to attacks such as code injection or buffer overflow. The database stores the system's data and may be vulnerable to attacks such as SQL injection or data tampering.
Real-world Web Security Breaches: Prevention Insights
There have been numerous major web security breaches in recent years, affecting businesses, governments, and individuals alike. Here are some examples of these breaches and how they could have been prevented:
- Equifax (2017) - This breach exposed the personal information of 143 million people. Equifax could have prevented this breach by patching a known vulnerability in their web application software.
- Target (2013) - This breach exposed the credit and debit card information of 40 million customers. Target could have prevented this breach by implementing better access controls and limiting the amount of sensitive data that employees had access to.
- Yahoo (2013-2014) - This breach exposed the personal information of all 3 billion Yahoo accounts. Yahoo could have prevented this breach by implementing better security practices, such as encrypting user data and using stronger passwords.
- Marriott (2018) - This breach exposed the personal information of 500 million guests. Marriott could have prevented this breach by detecting and responding to the breach sooner and implementing better security controls, such as multi-factor authentication.
- Capital One (2019) - This breach exposed the personal information of 106 million customers. Capital One could have prevented this breach by implementing better access controls, such as limiting the number of employees who had access to sensitive data.
In general, many web security breaches can be prevented by implementing better security practices, such as regularly patching vulnerabilities, implementing strong access controls, using multi-factor authentication, and encrypting sensitive data. It's also important for organisations to have a plan in place for detecting and responding to breaches in a timely manner.
Unveiling Web Vulnerabilities: Factors and Causes
- Poorly designed authentication and authorization mechanisms: Weak or poorly designed authentication and authorization mechanisms can allow unauthorised access to sensitive data or functionality.
- Insufficient input validation: Web applications often accept input from users, which can be manipulated or abused if the application does not properly validate the input. This can lead to vulnerabilities such as cross-site scripting (XSS) and command injection.
- Misconfiguration of web servers and applications: Configuration errors or oversights can leave a web application vulnerable to attacks such as directory traversal, file inclusion, or server-side request forgery (SSRF).
- Third-party software vulnerabilities: Many web applications rely on third-party libraries or plugins, which may contain vulnerabilities that can be exploited by attackers.
- Inadequate encryption and secure communication: If web applications fail to use encryption or secure communication protocols, attackers may be able to intercept or manipulate data in transit.
- Cross-site request forgery (CSRF): CSRF attacks exploit the trust that a web application has in a user's browser to execute unauthorised actions.
Web Vulnerabilities common Types and Examples
- Cross-site scripting (XSS): This occurs when an attacker injects malicious code into a web page, which is then executed by a victim's browser. This can allow the attacker to steal sensitive information, such as login credentials or session tokens.
- SQL injection: This occurs when an attacker inserts malicious SQL code into a web application's input field, which is then executed by the database. This can allow the attacker to access or modify sensitive data.
- Cross-site request forgery (CSRF): This occurs when an attacker sends unauthorised requests from a victim's browser to a web application, usually by tricking the victim into clicking on a link or button. This can allow the attacker to perform unauthorised actions, such as changing the victim's password or making unauthorised purchases.
- Broken authentication and session management: This occurs when a web application fails to properly authenticate users or manage their sessions. This can allow attackers to hijack user accounts or impersonate legitimate users.
- Insufficient input validation: This occurs when a web application accepts input from users without properly validating it. This can allow attackers to inject malicious code or exploit vulnerabilities in the application.
- Insecure direct object references: This occurs when a web application exposes sensitive data or functionality by using an identifier (such as a filename or database ID) that can be easily guessed or manipulated by attackers.
- Insecure cryptographic storage: This occurs when a web application stores sensitive data (such as passwords or credit card numbers) in an insecure manner, such as in plaintext or with weak encryption.
How the tech solved the problem for Halodoc
At Halodoc, we know that technology has a crucial role to play in ensuring the safety and security of our users' data. That's why we've invested in a range of cutting-edge technologies and strategies to help protect against web vulnerabilities and exposures.
One of the ways we've addressed this challenge is through the use of advanced encryption techniques. Encryption is the process of converting sensitive data into an unreadable format, so that only authorized users with the right key can access it. At Halodoc, we use encryption to protect user data both in transit and at rest, making it virtually impossible for hackers to intercept or steal sensitive information.
Another key technology we use is two-factor authentication (2FA), which adds an extra layer of security to our user login process. With 2FA, users are required to provide a second form of authentication, such as a code sent to their phone, in addition to their password. This makes it much more difficult for attackers to gain access to user accounts, even if they've managed to obtain a user's password.
Additionally, we conduct regular vulnerability testing and penetration testing to identify and address any potential weaknesses in our systems. This proactive approach allows us to stay ahead of the latest threats and vulnerabilities, and make sure that our users' data remains secure at all times.
Solving Web CVEs in Halodoc: Real-Life Examples
At Halodoc, we are committed to providing a secure and reliable platform for our users. As part of this commitment, we regularly monitor our systems for potential vulnerabilities, including those related to third-party software packages.
One of the ways we address package vulnerabilities is by using automated tools to scan our systems and identify any packages that are known to have vulnerabilities. When a vulnerable package is identified, we immediately assess the risk to our systems and determine the appropriate course of action.
- In many cases, the best solution is to update the vulnerable package to a fixed version that addresses the vulnerability. To do this, we first identify the fixed version that contains the necessary security patches. We then perform a thorough testing process to ensure that the updated package is compatible with our systems and does not introduce any new issues.
- If updating the package is not possible or practical, we may implement other measures such as patches or workarounds to mitigate the vulnerability until a permanent fix can be implemented.
- Throughout this process, we prioritize the safety and security of our users' data and take every possible measure to ensure that our systems remain secure and protected against vulnerabilities. We also keep our users informed about any potential security issues and the steps we are taking to address them, so that they can feel confident and secure when using our platform.
Overall, web vulnerabilities can pose a serious threat to the security of web applications and the data they store. It is essential for developers to stay informed about the latest vulnerabilities and best practices for securing their applications.
Here are some ways to prevent web vulnerabilities in your website
- Input validation: Proper input validation is critical to prevent many types of web vulnerabilities. Always validate and sanitise user input on the server-side, and use parameterised queries to prevent SQL injection attacks.
- Use a web application firewall: A web application firewall (WAF) can help detect and block attacks before they reach your web application. WAFs can filter out malicious traffic, block SQL injection attempts, and prevent cross-site scripting attacks.
- Regularly update software and libraries: Keep your web application and all related software and libraries up-to-date with the latest security patches and updates.
- Implement secure authentication and session management: Use strong passwords, multi-factor authentication, and proper session management to prevent attacks that exploit weak authentication and session management.
- Use secure coding practices: Follow secure coding practices, such as avoiding hard-coded passwords and sensitive information in source code, properly handling errors and exceptions, and using secure communication protocols.
- Perform regular security audits and penetration testing: Regularly audit your web application's security and perform penetration testing to identify and address vulnerabilities.
Educate your users: Educate your users about safe browsing habits, such as avoiding suspicious links and not sharing sensitive information with unauthorised users.
By following these best practices, you can help prevent web vulnerabilities and protect your website and its users from cyber attacks.
Secure Web Software: Stay Updated, Stay Safe
Keeping web software up-to-date is crucial to prevent vulnerabilities that can be exploited by attackers. Web software, including content management systems, web servers, and web applications, are complex systems that are constantly evolving. As new features are added and bugs are fixed, vulnerabilities may also be discovered.
When software vulnerabilities are identified, software vendors release patches or updates to fix them. These patches typically address security issues that could be exploited by attackers. If the software is not updated, it will remain vulnerable to known security issues, leaving it open to attack.
Attackers are constantly searching for vulnerabilities in software to exploit. Once a vulnerability is discovered, attackers will attempt to exploit it before a patch is released. If a patch is not installed, attackers can gain access to sensitive data, take control of the system, or use the system to launch attacks on other systems.
In addition to the security benefits of keeping web software up-to-date, there are other benefits as well. Updates often include new features, improved performance, and bug fixes. By keeping software up-to-date, organisations can take advantage of these improvements, which can improve productivity and efficiency.
In summary, it is essential to keep web software up-to-date to prevent vulnerabilities that can be exploited by attackers. Regularly updating software not only protects against known vulnerabilities but also provides access to new features, improved performance, and bug fixes.
Summary
In conclusion, web security vulnerabilities can have serious consequences for both users and businesses. Through this article, we have discussed the importance of identifying and addressing these vulnerabilities through regular assessments and patching, as well as following best practices for web security.
We have also explored the role of CVEs in helping to identify and report security issues, and the importance of staying informed about potential threats in the web security landscape.
By taking proactive measures to protect against web security vulnerabilities, we can help to prevent potential attacks and safeguard sensitive information. It is our responsibility to remain vigilant and ensure the safety and security of web applications for all users.
Join us
Scalability, reliability and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com.
