Seamless IOC Integration to Improved Threat Detection and Response
At Halodoc, we recognize the importance of a proactive approach to cybersecurity in today's ever-evolving landscape of cyber threats. To ensure the highest level of security for our platform and users, we rely on a multitude of external sources, including threat intelligence providers, security researchers, and industry-specific organisations. These external sources play a crucial role in providing us with Indicators of Compromise (IOCs), which are vital artifacts that indicate the presence of cybersecurity threats. IOCs can take various forms, such as IP addresses, domain names, hashes, or patterns of malicious behaviour. However, some key challenges are faced in maintaining accurate and up-to-date Indicators of Compromise. Also, the traditional approach of manually procuring and collating IOCs from various sources is time-consuming, and prone to human errors.
By having that fact, the objective of this blog is to shed light on the importance of collating IOCs and the challenges associated with the traditional approach of procuring them and finally how this process is automated at Halodoc. The blog will also provide an overview of key components utilised such as EDR (CrowdStrike), OTX AlienVault, and VirusTotal which are the main parts used in this automation process.
The Importance of Collating IOCs
IOCs are artifacts or evidence that indicate the presence of malicious activity or a security breach. They are used to identify and detect potential security incidents, threats, or compromises within an organisation's systems, networks, or applications. Here, we explore the importance of collating IOCs and its impact on overall cybersecurity resilience as follows:
- Comprehensive Threat Visibility and Knowledge Sharing
By aggregating IOCs from threat intelligence feeds, security reports, and incident response activities, organisations can gain a holistic view of the indicators associated with potential cyber threats. Also, this comprehensive visibility enables knowledge sharing and collaboration within the cybersecurity community such as trusted partners, industry peers, and security organisations. This collaborative approach strengthens the collective defence against emerging threats and facilitates the development of more effective security measures and countermeasures. - Early Threat Detection and Prevention
By analysing and correlating collected IOCs with their existing security infrastructure, organisations can identify patterns and signatures of known threats. This proactive approach allows security teams to block or mitigate potential attacks before they cause substantial harm, minimising the impact on systems and data. Additionally, as part of incident investigation, having a comprehensive repository of IOCs enables rapid identification and analysis of compromised systems. Security teams can compare collected IOCs against their network logs and security systems to determine the extent of the incident, identify affected assets, and execute appropriate response measures promptly. - Proactive Vulnerability Management
IOCs collected through collation efforts help organisations stay proactive in vulnerability management. By regularly analysing and updating their IOC repositories, organisations can identify new attack vectors and vulnerabilities. This enables them to apply appropriate patches, update security configurations, and implement necessary safeguards to protect against emerging threats targeting their systems.
Challenges with current approach
Traditionally at Halodoc, this practice required the manual gathering and input of Indicators of Compromise (IOCs) into security systems, leading to significant time consumption and an increased vulnerability to human errors.
- Time-Consuming: Manually collecting IOCs required significant time and effort. Security analysts had to search for IOCs from various sources, such as threat intelligence feeds, reports, and research papers. This manual process involved sifting through large volumes of information, which could be a time-consuming task.
- Potential for Errors: Manual collection and ingestion of IOCs were prone to human errors. Security analysts could miss relevant IOCs or introduce inaccuracies during the data entry process. These errors could lead to incomplete or incorrect IOC data, compromising the effectiveness of threat detection and incident response.
- Lack of Scalability: Manual processes limited the scalability of IOC collection. As the number of IOCs grew and new sources of threat intelligence emerged, it became increasingly challenging for security teams to keep up with the volume and variety of IOCs manually. This limitation hindered the ability to effectively detect and respond to evolving cyber threats.
- Inefficiency in Real-time Updates: The manual nature of IOC collection often resulted in delays in updating security systems with the latest IOCs. As new threats emerged, security teams had to manually identify, validate, and input the relevant IOCs, causing a lag between the detection and mitigation of emerging threats. This lag increased the organisation's exposure to potential attacks during the update process.
- Risk of Inconsistent Data Formats: IOCs can be represented in various formats, including IP addresses, domain names, file hashes, and patterns of behaviour. Manually collecting IOCs increased the risk of inconsistencies in data formats, making it difficult to effectively analyse and correlate IOCs across different security systems. This inconsistency could lead to missed or ineffective threat detection.
- Resource Intensive: Manual IOC collection required dedicated resources, including skilled security analysts, to continually search for and ingest IOCs into security systems. This resource-intensive process diverted valuable human resources from other critical security tasks, limiting the overall efficiency and effectiveness of the security team.
Overview about CrowdStrike, OTX ALienVault and VirusTotal
CrowdStrike is one of the Endpoint Detection and Response (EDR) that is used in Halodoc. EDR solution utilised by Halodoc, plays a vital role in maintaining IOCs by collecting and analysing threat intelligence from diverse sources. It offers seamless integration of IOCs into security systems, enabling real-time threat detection and prevention. Additionally, EDR allows organisations to manually inject their own IOCs, derived from internal or unique sources, enhancing their cybersecurity defenses by tailoring them to specific needs and intelligence. This allows organisations to provide their own specific IOCs, derived from internal sources or unique threat intelligence, and incorporate them into their security infrastructure. By allowing manual injection, EDR enables organisations to tailor their defence strategies based on their specific needs and intelligence, enhancing the effectiveness of their cybersecurity defenses.
OTX (Open Threat Exchange) by AlienVault is a collaborative platform designed for sharing and accessing threat intelligence. It operates as an open-source project that enables security researchers, organisations, and individuals to contribute, analyse, and share information concerning various threats, including indicators of compromise (IOCs), vulnerabilities, malware samples, and more.
VirusTotal is a widely-used online service that analyses files and URLs for potential malware and other security threats. It aggregates results from various antivirus engines and other security tools, providing insights into the reputation and detection status of submitted samples. With its extensive database and collaborative nature, VirusTotal offers valuable information to security professionals, enabling them to make informed decisions and enhance their threat detection capabilities.
Implementing the automation IOC injection process
To streamline the process of injection of IOCs into EDR, we are developing an automation script to ingest IOC automatically from a third-party source - AlienVault to EDR. Please refer the image below to have a better understanding.
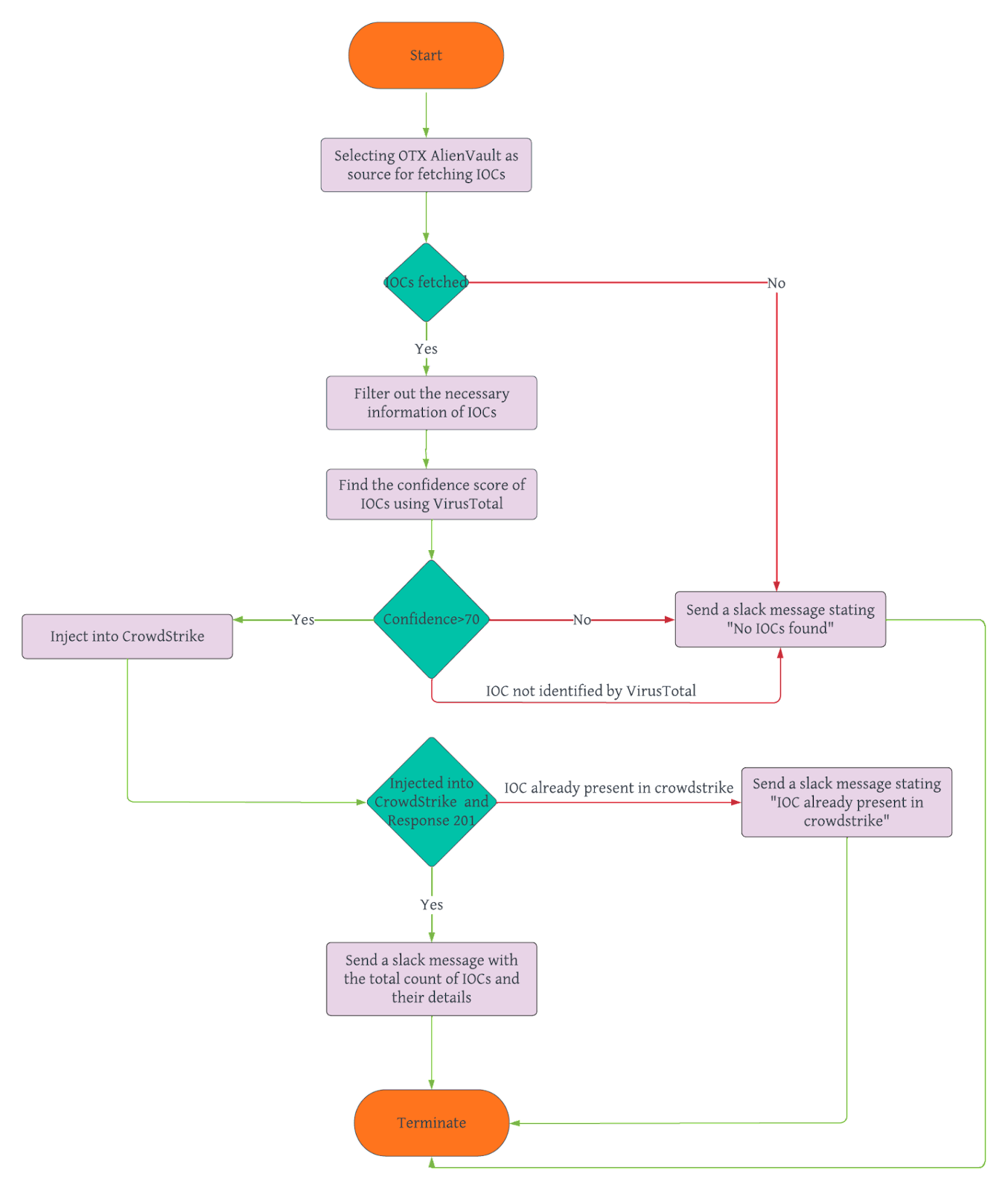
Flowchart to visualise the automated IOC injection process
There are four primary steps followed in this project are listed below:
1. Collecting IOCs from AlienVault
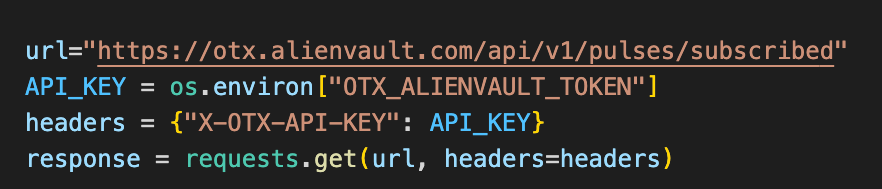
The first step in the automation process is to collect IOCs from the OTX AlienVault platform. We make an API call to the AlienVault API using the endpoint https://otx.alienvault.com/api/v1/pulses/subscribed and provide the necessary authentication headers. The response contains information about the IOCs, including their types, values, and other metadata.
2. Analysing IOCs with VirusTotal
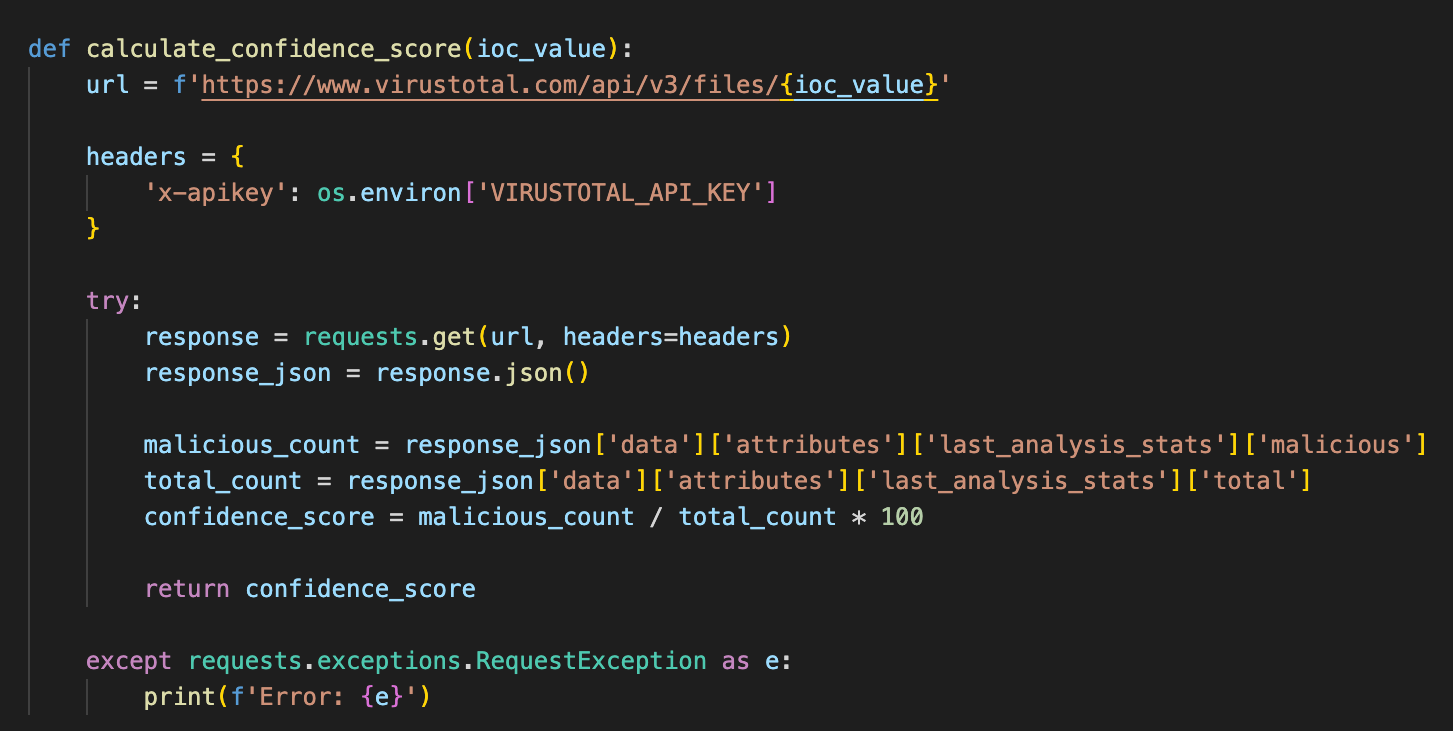
Once we have the IOCs from AlienVault, we utilise VirusTotal's API to analyse each IOC and calculate a confidence score based on the number of sources that have flagged the IOC as malicious. The confidence score helps determine the level of suspicion associated with each IOC.
3. Injecting IOCs into EDR
After calculating the confidence scores, a predefined threshold of 70% is currently utilized to identify IOCs with a significant level of suspicion. These IOCs surpassing the threshold are then injected into EDR-CrowdStrike for bolstered security measures. Authentication with the CrowdStrike API is achieved by obtaining an access token through the OAuth2 authentication flow. It's important to note that in future the confidence score threshold can be adjusted according to the requirements and risk tolerance.
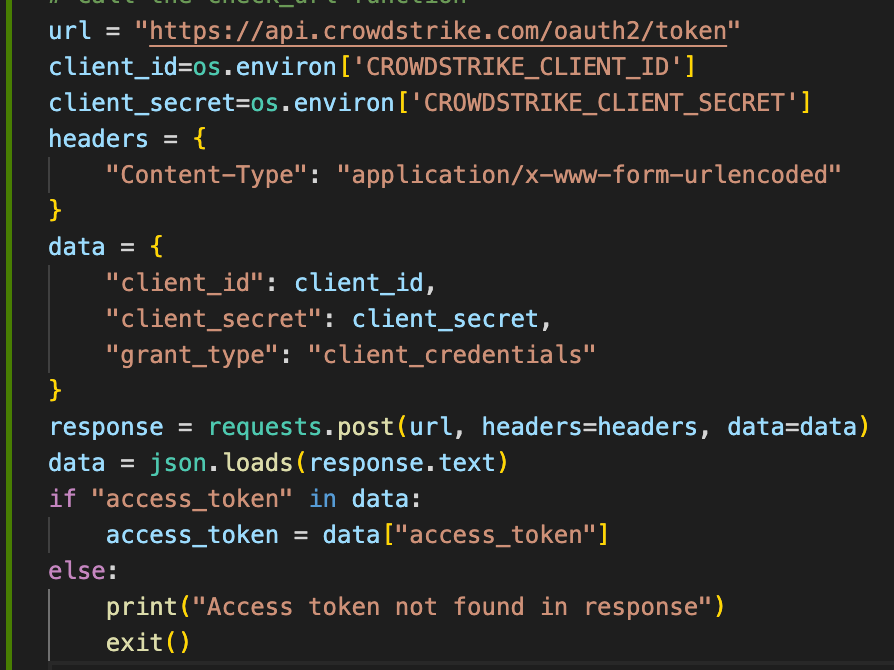
Finally, we loop through the IOCs and inject them into EDR using the CrowdStrike API's IOC injection endpoint. The injected IOCs are associated with a confidence score, action type (prevent or detect), and other relevant metadata.
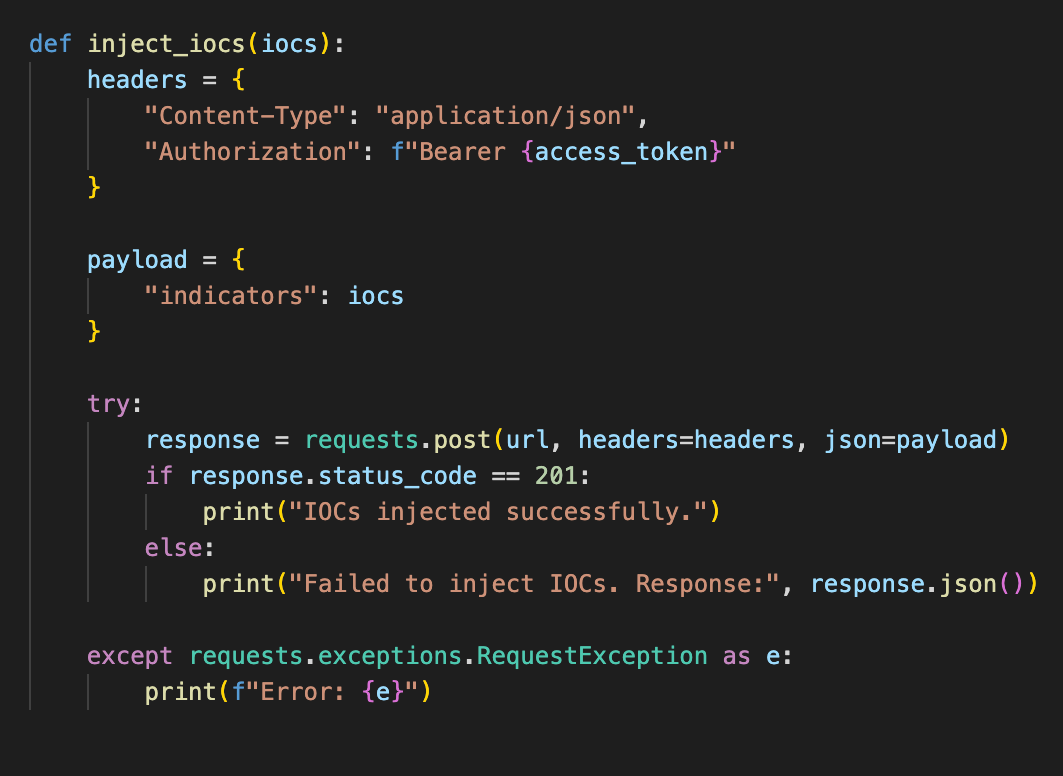
4. Monitoring IOCs with Slack Integration
To ensure better monitoring and maintain a centralised log of IOC changes, we have integrated Slack into the automation script. The details of the added IOCs, including their types, values, scores, and action types, are sent as notifications to a private channel in Slack. This integration enables the security team to have real-time visibility into the IOCs injected into EDR and take prompt actions against emerging threats.
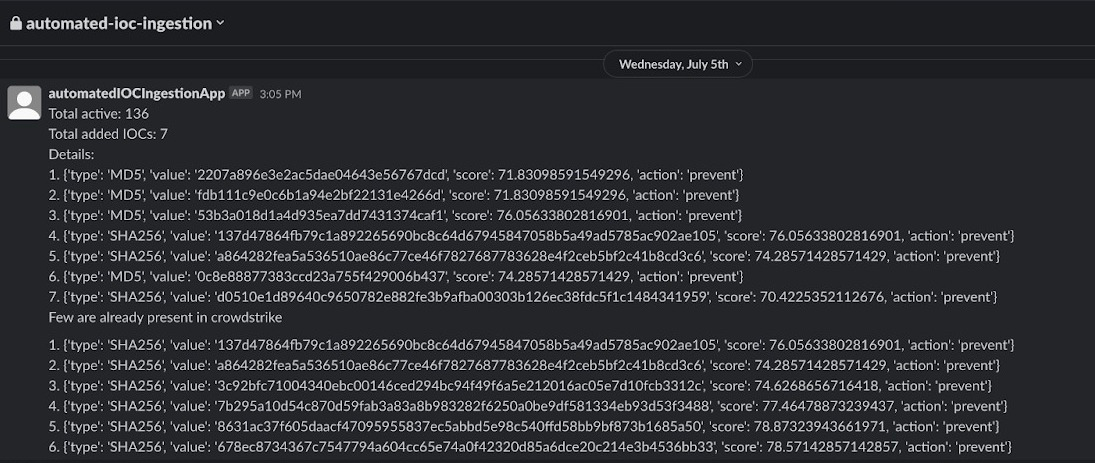
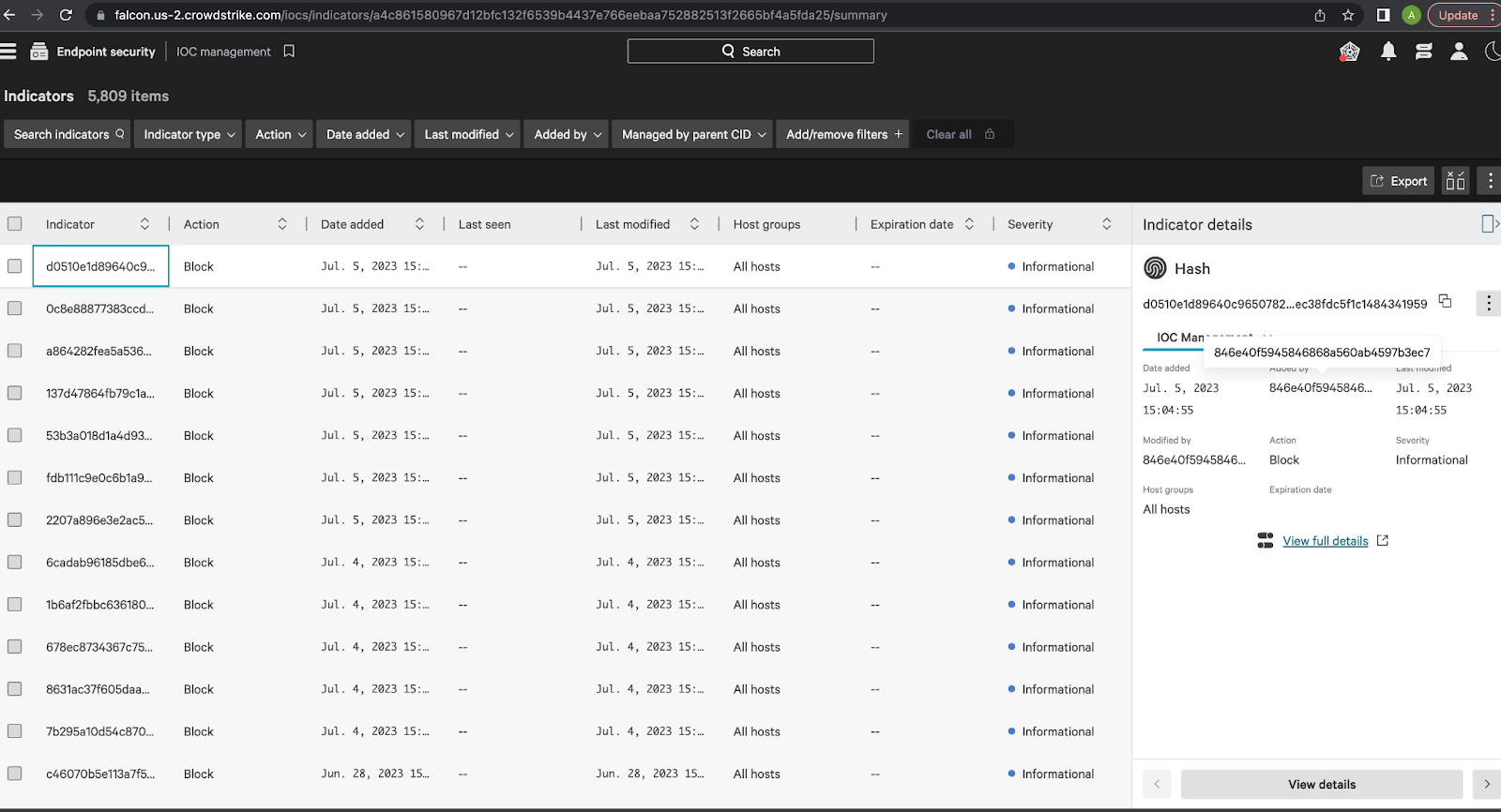
It can be confirmed that the IOCSs mentioned in the slack notification have been successfully added to the CrowdStrike management dashboard as shown in the below screenshot. The dashboard also provides details of the client ID who added these specific IOCs. This client ID is used for the project mentioned in this blog.
These notifications serve the purpose of providing information regarding the Indicators of Compromise (IOCs) sourced from AlienVault OTX. However, it has been observed that some of these IOCs are already present within the CrowdStrike platform. The presence of duplicate IOCs in CrowdStrike can be attributed to a few possible reasons.
- Firstly, it is possible that these IOCSs were previously injected into CrowdStrike by the automation script when it was run earlier. Due to the unupdated input from OTX AlienVault, there is a possible case that the automation script may analyse and identify the same IOCs again which must have been analysed and injected earlier.
- Secondly, it is also possible that the same IOCs that the automation script had identified and tried to inject were manually added by an individual who recognized the significance of those specific IOCs.
- Lastly, these IOCs may already be included in the comprehensive IOC information identified by CrowdStrike. This implies CrowdStrike has already flagged and recognized these IOCs as potentially malicious or significant.
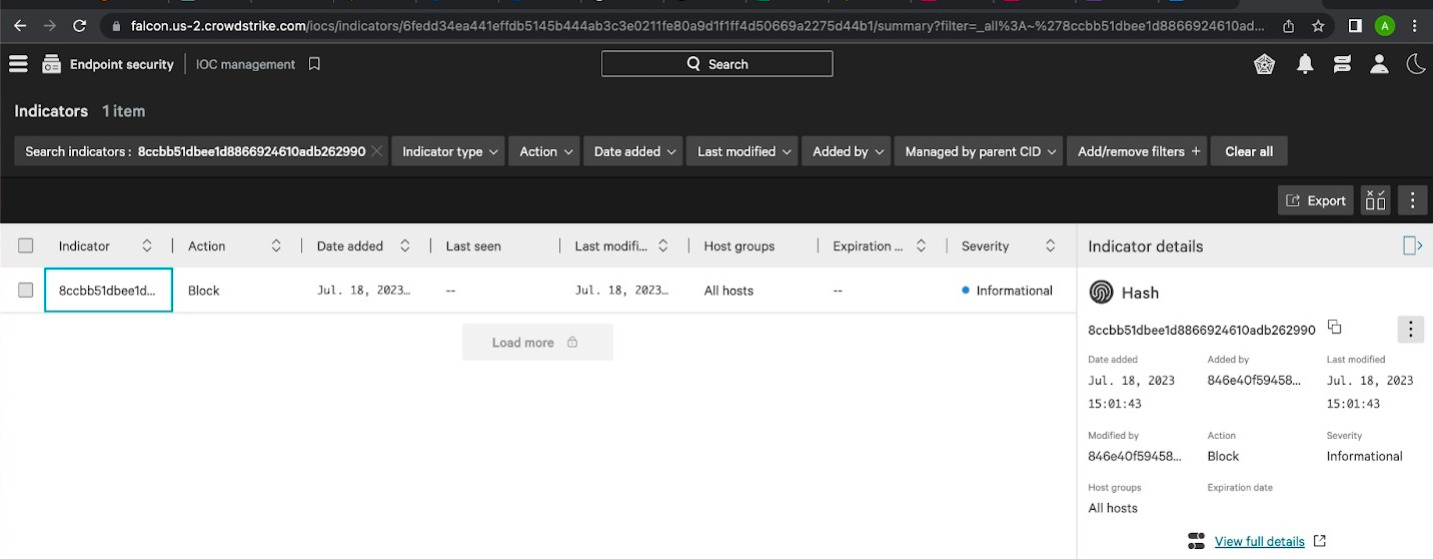
For illustration, let’s consider the IOC value highlighted in the following screenshot, which represents one of the notifications on slack on July 19th 2023. The notification states that this particular IOC is already present in CrowdStrike.
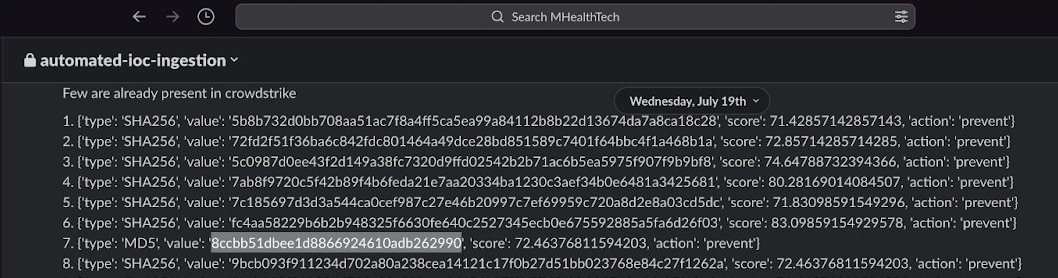
To verify the veracity of this claim, we search for this IOC value in the CrowdStrike IOC management dashboard. From the provided screenshot, it is evident that this particular IOC had already been added on 18th July 2023.
These features enable Halodoc's security team to have comprehensive visibility and control over the IOCs integrated into EDR, enhancing their ability to protect against emerging threats.
Conclusion
In conclusion, Automation of IOC (Indicators of Compromise) management and integration brings significant benefits to organisations' cybersecurity efforts. By leveraging platforms like OTX AlienVault, VirusTotal, and EDR (CrowdStrike), we can streamline the collection, analysis, and injection of IOCs, enhancing threat detection capabilities, proactively blocking potential threats, and responding swiftly to security incidents. This automation saves time, reduces human errors, and enables organisations to maintain a proactive and robust security posture, leveraging collective intelligence and ensuring efficient and accurate IOC management.We also can enhance our threat detection capabilities, enabling us to proactively mitigate risks and manage security incidents effectively.
Join Us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek, and many more. We recently closed our Series C round and In total have raised around USD$180 million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.
