How Halodoc Prevents Data Leaks with CrowdStrike Falcon Data Protection
At Halodoc, we handle millions of user interactions every month. With this responsibility comes the challenge of keeping sensitive health and identity information safe, even on employee devices.
As data becomes the most valuable corporate asset, protecting it at the source has become a fundamental security requirement. Traditional network-centric DLP (Data Loss Prevention) systems focus primarily on traffic leaving the perimeter, but in today’s hybrid, cloud-first world, data often originates, moves, and transforms within endpoints long before it crosses the network boundary.
To address this, we implemented CrowdStrike Falcon Data Protection (FDP), a lightweight and intelligent endpoint-level DLP solution that safeguards data directly where it’s created and accessed.
What is Falcon Data Protection (FDP) ?
Falcon Data Protection (FDP) is a data security solution designed to prevent sensitive information from being exposed, misused, or transferred outside approved channels.
As part of the CrowdStrike Falcon platform, FDP enforces data protection directly on the endpoint, ensuring that confidential information, such as personal, financial, or medical data, remains secure and traceable across company devices.
In essence, FDP empowers organizations to define and apply data protection rules that align with regulatory and operational needs, maintaining compliance and preventing both accidental and intentional data leaks.
Think of FDP as a smart gatekeeper inside every laptop: it scans files in real time, identifies sensitive content (like ID numbers or payment data), checks them against predefined policies, and blocks unauthorized transfers—even when the device is offline.
FDP’s decentralized enforcement and centralized governance model ensures that detection and policy logic run locally on the device, while telemetry and configuration are managed centrally through the Falcon Console.
FDP Architecture and Workflow
When a user interacts with data, such as copying, uploading, or attaching a file, FDP performs three key steps:
- Content Recognition: Scans the file or data stream for sensitive patterns (e.g., ID numbers, medical records).
- Policy Evaluation: Checks the action against department-specific data handling policies.
- Enforcement: Allows, blocks, or logs the action based on policy compliance.
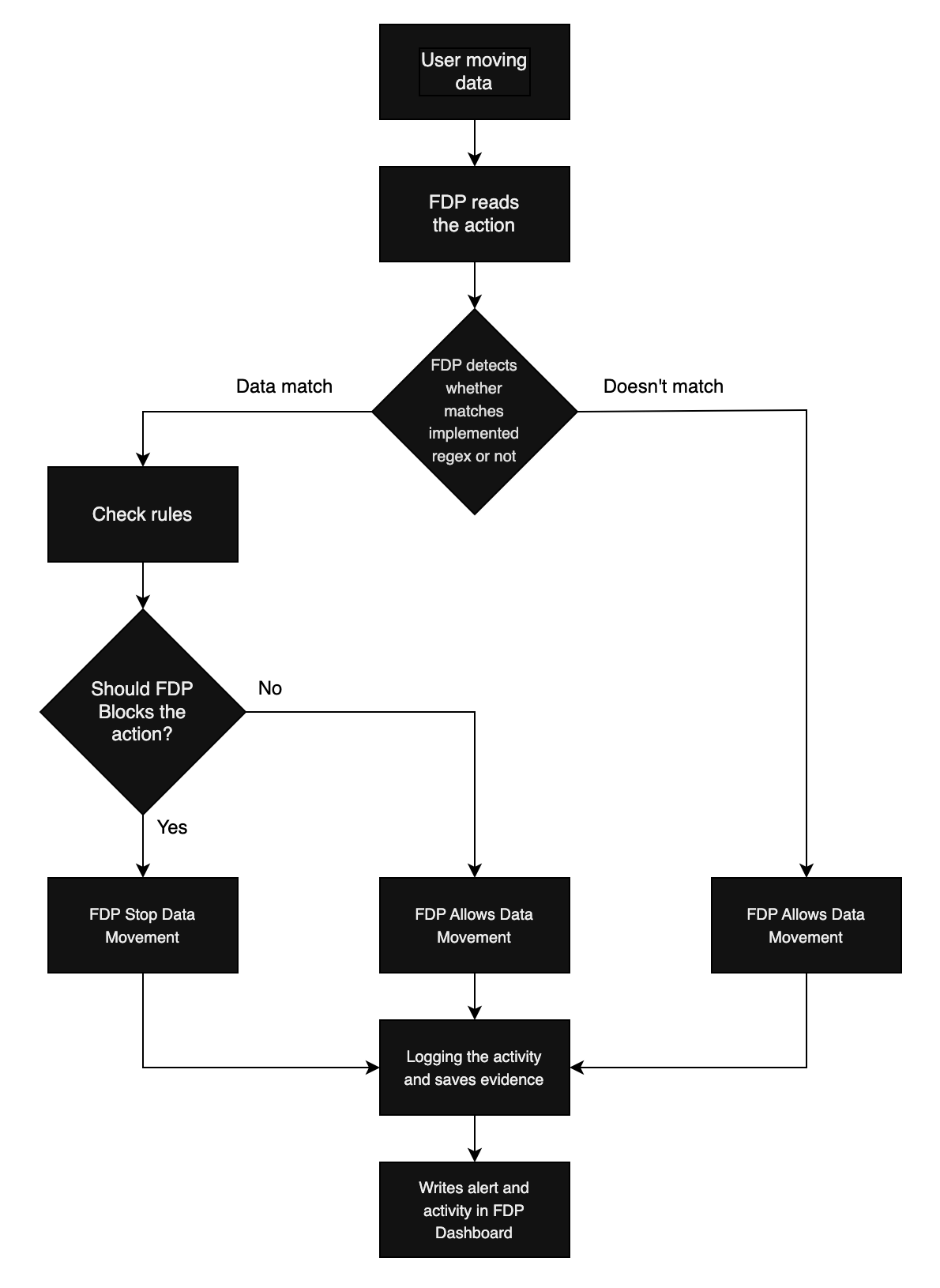
This enforcement happens directly on the endpoint—ensuring protection even without network connectivity.
The Purpose and Context of FDP
The primary challenge FDP solves is the lack of real-time visibility into data movement. Without FDP, organizations often rely on logs or manual audits that only provide historical insight, not prevention. FDP is designed to proactively detect, classify, and control sensitive information before it leaves an endpoint.
This means that even if a user copies a file to an external USB, attaches a confidential document to an email, or tries to upload data to an unapproved cloud service, FDP will intercept the action, analyze the content, and decide, based on defined rules, whether to allow, block, or log it.
FDP’s design philosophy centers on decentralized enforcement and centralized governance. Detection and policy logic are executed locally by the endpoint agent, while configuration and telemetry are managed through a centralized Falcon console. This ensures that protection continues even when the device is offline, while still providing organization-wide visibility for administrators.
How FDP Protects Halodoc's Data
FDP runs silently across all managed devices in our organization. It works as an intelligent guardrail, monitoring and controlling how data is handled, not by blocking productivity, but by preventing risky or non-compliant transfers.
When a user interacts with data (for example, copying, uploading, or sharing a file), FDP performs three key actions:
- Content Recognition: It analyzes the file or data stream in real time to determine if it contains sensitive information such as identification numbers, health records, or financial data.
- Policy Evaluation: Based on internal policies, tailored for each department, FDP checks whether the intended action complies with data handling standards.
- Enforcement: If the action violates policy, FDP blocks it immediately and records the event for auditing, without exposing any sensitive data.
This approach ensures that sensitive data, including client records, patient details, financial documentation, and internal reports, remains within our approved systems at all times.
Policies are reviewed and refined quarterly by our Information Security and Data Privacy teams, incorporating user feedback to reduce false positives and maintain precision.
False Positive Handling: User feedback loops and detection reports are continuously analyzed to fine-tune regex patterns for better accuracy without sacrificing protection.
Technical Enforcement at the Endpoint
The strength of FDP lies in its position on the endpoint, the very place where data is created and used.
Every company-issued laptop, personal working laptop, and company workstation, runs an FDP sensor that integrates with the operating system’s kernel-level hooks. This allows it to observe operations such as:
- File creation, copy, and modification
- Email attachments
- Clipboard activity
- Uploads to browsers or third-party services
- External device usage (e.g., USB drives)
Each operation is inspected in real time. If FDP detects that the content matches sensitive information, for instance, a client ID pattern, medical record number, or any data type classified as confidential, it evaluates the user’s permissions and the target destination.
If the action is unauthorized, FDP instantly blocks it. If it’s legitimate, it proceeds but logs the event for traceability. This enforcement happens locally, meaning protection remains active even if the device is offline or disconnected from our network.
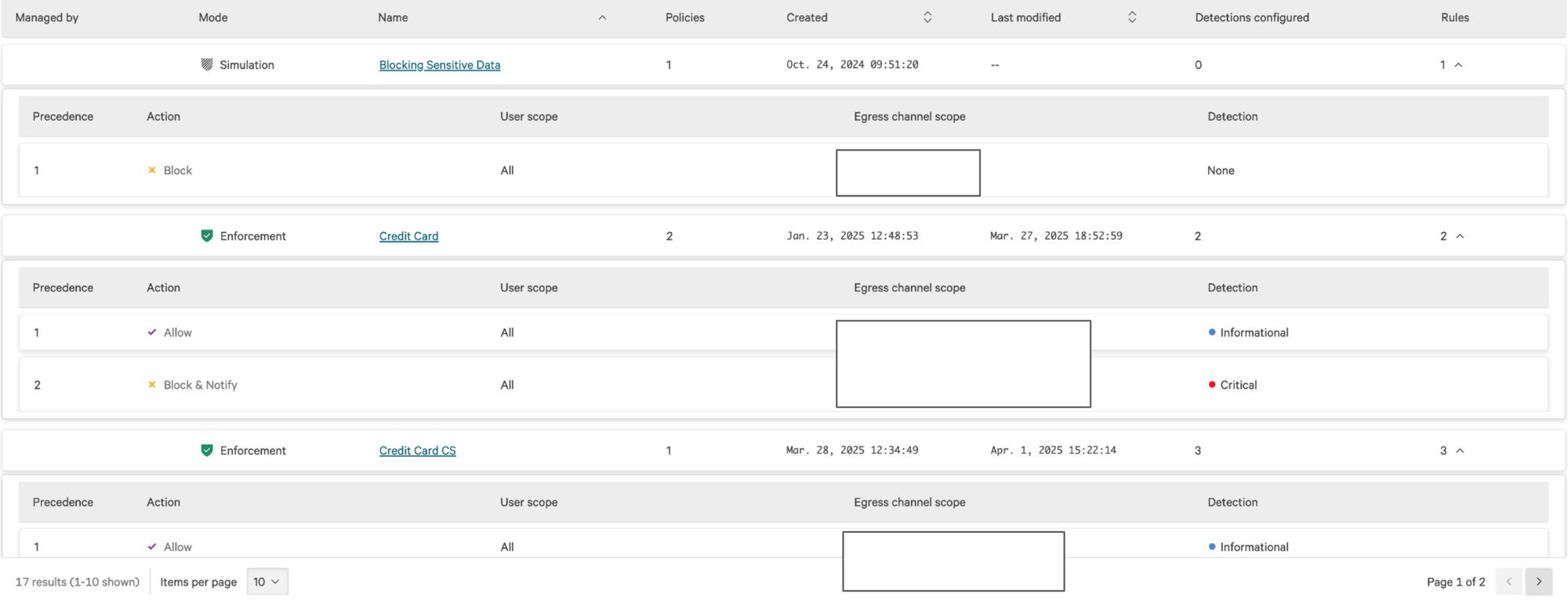
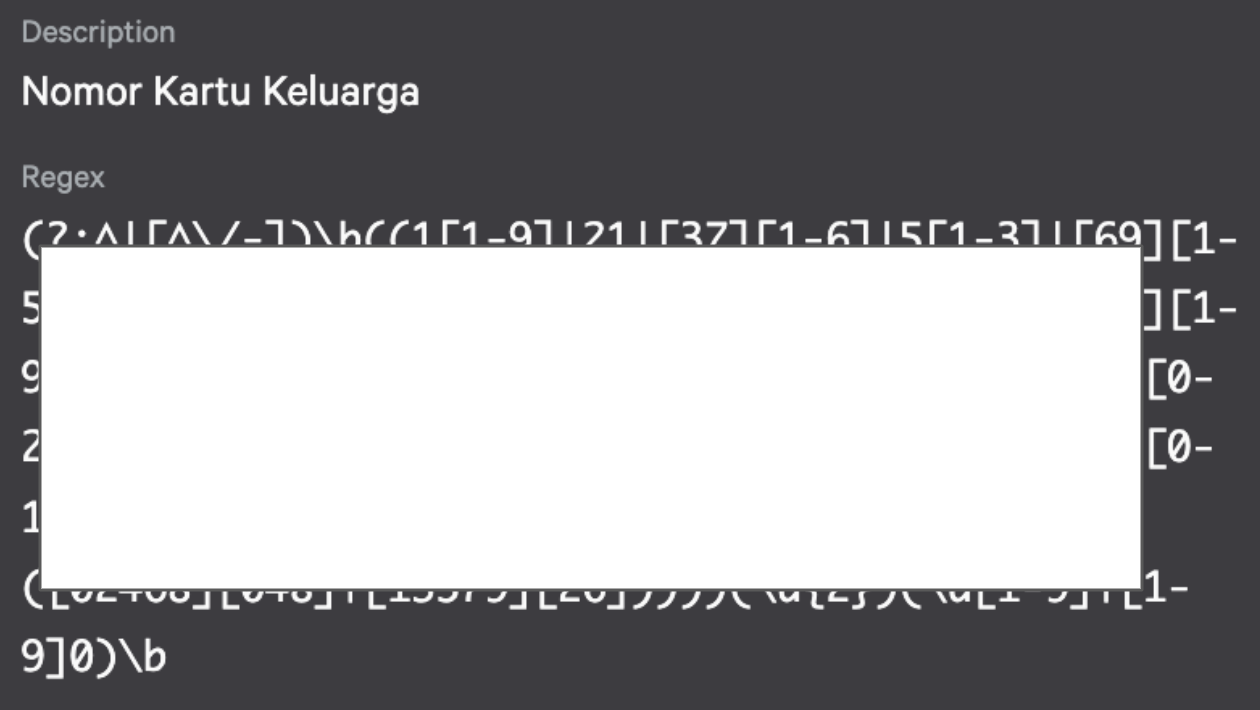
A policy is first created for each department, tailored to its specific data protection needs. This policy is then linked to certain data types relevant to that department’s operations, for example, financial identifiers for Finance or employee information for HC. Each data type is defined by a unique regex pattern that enables Falcon Data Protection (FDP) to recognize it accurately within files, messages, or uploads. When FDP detects a match with any of these patterns, it automatically enforces the predefined action rules, such as allowing the operation, blocking it entirely, or generating an alert, based on what’s specified in the policy.
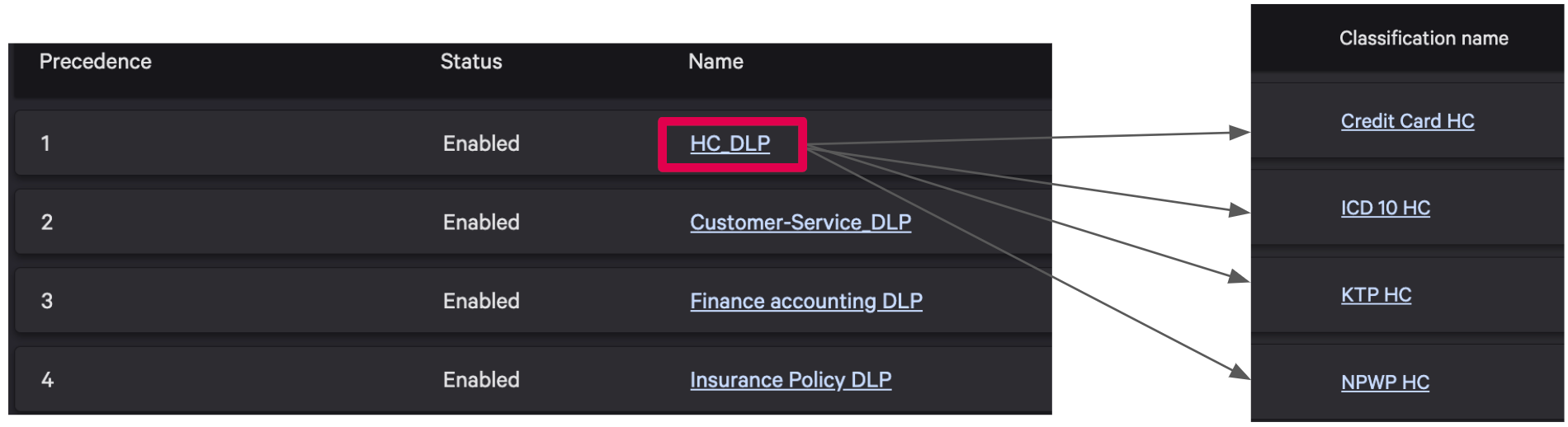
From the snippet above, we can see that each policy is designed for a specific department. Within each policy, we can define different data types based on the sensitive information relevant to that department. For each data type, we can create a regex pattern that represents the actual document, such as credit cards, NIK, KK, NPWP, and others.
Demonstrating Real Protection: True Positive Detection Example
While most of our Falcon Data Protection (FDP) activity operates quietly in the background, it continuously prevents data from leaving our environment through unauthorized channels. The following example illustrates a real, verified detection where FDP successfully blocked a potential data exfiltration attempt, confirming that our policies are working as intended.
On October 27, 2025, FDP detected an attempt by a user to copy a file named Cek Order Feb.xlsx , categorized under the Finance department’s policy, to an external USB storage device identified as a Ugreen Storage Device. The content within that file contained sensitive identifiers, specifically Nomor Kartu Keluarga (Family Card Number), which matches our predefined data protection regex pattern for personal information.
Upon inspection, FDP immediately recognized this activity as a rule-based policy violation and classified it under the tactic “Exfiltration via Physical Medium.” The system automatically enforced the configured response action: Blocked. The event was logged as Critical severity, with full metadata captured, including the user account, detection source, data type, and destination device.
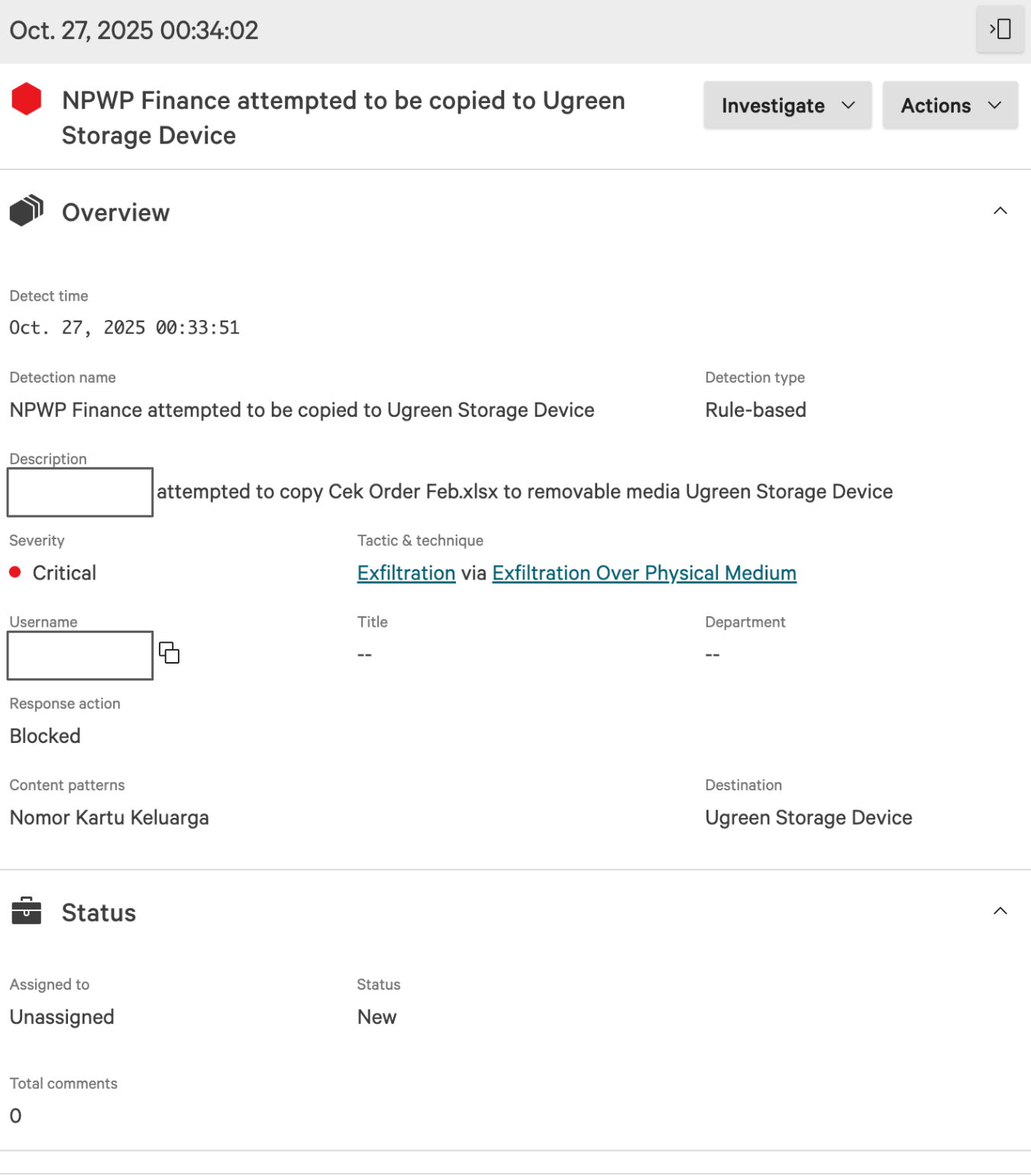
This event was classified as a true positive, meaning the detection was accurate, the data was indeed sensitive, and the attempted transfer was properly blocked in real time, without relying on manual intervention.
This validation is significant because it confirms that our FDP configuration, specifically, the Finance policy’s regex patterns and removable media restrictions, is functioning exactly as designed. It also demonstrates the precision of our detection logic: legitimate work activities are allowed, but unauthorized data movement is immediately stopped.
In practice, this type of detection ensures that:
- Sensitive client or financial information cannot be copied to removable drives.
- FDP prevents both accidental and intentional data leakage.
- Our security and compliance teams maintain an auditable record of every event for review and reporting.
Such real-world detections provide concrete assurance that client data remains protected even in the most granular user actions, reinforcing our zero-tolerance approach to data exfiltration risks. It also demonstrates that FDP’s protection coverage isn’t limited to applications or web-based transfers; the system is equally effective at detecting and blocking data movement to physical external media, such as USB flash drives, portable hard disks, or any other removable storage devices. This ensures that even offline exfiltration attempts are intercepted and contained before any sensitive data can leave our secured environment.
Operational Insights
The rollout of FDP across Halodoc was executed in stages, integrated seamlessly into our endpoint management workflow.
- Centralized Management: All policies are configured and monitored through the Falcon Console.
- Scalable Deployment: FDP sensors are deployed through existing endpoint agents, requiring minimal user interaction.
- Performance Efficiency: Since FDP operates at the kernel level, it introduces negligible performance overhead, ensuring smooth user experience.
Challenges & Learnings
During the initial rollout, our primary challenge was reducing false positives, especially for shared files containing numeric identifiers.
Through collaboration between security engineers and department heads, we refined regex accuracy and introduced department-based policy exceptions, improving detection precision while maintaining protection.
Key lessons:
- Continuous tuning is essential for effective DLP accuracy.
- Clear communication with end-users helps reduce alert fatigue.
- Cross-team feedback accelerates policy maturity.
Conclusion
CrowdStrike FDP has become a cornerstone of Halodoc’s data security strategy, helping us protect sensitive health and personal data at the source. As we continue to evolve our security posture, endpoint-level DLP ensures that every device remains a trusted extension of our infrastructure.
Join us
Scalability, reliability and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com.
Bug Bounty
Got what it takes to hack? Feel free to report a vulnerability in our assets and get yourself a reward through our bug bounty program. Find more details about policy and guidelines at https://www.halodoc.com/security
About Halodoc
Halodoc is the number one all-around healthcare application in Indonesia. Our mission is to simplify and deliver quality healthcare across Indonesia, from Sabang to Merauke.
Since 2016, Halodoc has been improving health literacy in Indonesia by providing user-friendly healthcare communication, education, and information (KIE). In parallel, our ecosystem has expanded to offer a range of services that facilitate convenient access to healthcare, starting with Homecare by Halodoc as a preventive care feature that allows users to conduct health tests privately and securely from the comfort of their homes; My Insurance, which allows users to access the benefits of cashless outpatient services in a more seamless way; Chat with Doctor, which allows users to consult with over 20,000 licensed physicians via chat, video or voice call; and Health Store features that allow users to purchase medicines, supplements and various health products from our network of over 4,900 trusted partner pharmacies. To deliver holistic health solutions in a fully digital way, Halodoc offers Digital Clinic services including Haloskin, a trusted dermatology care platform guided by experienced dermatologists.
We are proud to be trusted by global and regional investors, including the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek, and many more. With over USD 100 million raised to date, including our recent Series D, our team is committed to building the best personalized healthcare solutions — and we remain steadfast in our journey to simplify healthcare for all Indonesians

