Vulnerability Prioritisation with Crowdstrike Falcon Spotlight Vulnerability Management
Introduction:
Security remains a paramount concern within the operations of Halodoc. Our unwavering commitment to safeguarding our systems is evidenced by the comprehensive array of measures in place, including robust practices such as Software Composition Analysis (SCA), Static Analysis Security Testing (SAST), Dynamic Analysis Security Testing (DAST), Vulnerability Assessment (VA) and Penetration Testing (PT).
Going above and beyond, we have instituted not only a self-managed Bug Bounty Program but also a private Bug Bounty Program, showcasing our dedication to preemptively identifying and addressing security vulnerabilities.
In the context of this blog post, our focus shifts towards a thorough exploration of the capabilities offered by CrowdStrike Falcon Spotlight. Through an in-depth examination, we will unravel the diverse features and inherent advantages this vulnerability management solution brings to the forefront. By delving into its complexities, we aim to underscore its instrumental role in enhancing and fortifying our overall cybersecurity posture.
What is Vulnerability?
In the realm of cybersecurity, a vulnerability stands as a critical focal point. It signifies a gap or flaw within a computer system, software application, network, or any technological asset that opens a pathway for potential exploitation. Malicious actors, seeking to compromise the security and integrity of the asset, target these vulnerabilities. Rooted in various sources such as programming errors, design deficiencies, misconfigurations, and even inherent weaknesses in underlying components, vulnerabilities act as entry points for cyber threats.
The identification of vulnerabilities occurs through a variety of channels, encompassing automated vulnerability scanning tools, hands-on manual testing, and the engagement of bug bounty programs. Once a vulnerability is identified, it necessitates assessment to gauge its potential impact and likelihood of being exploited. Effective vulnerability management involves prompt actions, such as applying patches, improving security controls, or updating configurations. As technology advances and security measures evolve, identifying and managing vulnerabilities emerges as an ongoing pursuit, vital to upholding a robust cybersecurity posture.
Impact:
The impact of vulnerabilities can vary widely depending on the nature of the vulnerability, the context in which it's exploited, the systems affected, and the intentions of the attacker. Here are some potential impacts of vulnerabilities:
- Data Breaches: Vulnerabilities can be exploited to gain unauthorized access to sensitive data, leading to data breaches. This can result in the exposure of personal information, financial data, trade secrets, intellectual property, and more. Data breaches can have a serious impact for individuals and organizations.
- Malware and Ransomware: Vulnerabilities can be used to deliver and spread malware or ransomware. Malware can disrupt operations, steal information, or use systems for malicious activities. Ransomware can encrypt data and demand a ransom for its release, causing significant financial and operational damage.
- Disruption of Services: Some vulnerabilities can be leveraged to disrupt services, such as Distributed Denial of Service (DDoS) attacks. By overwhelming a system or network with traffic, attackers can render it unavailable to legitimate users.
- Financial Loss: Vulnerabilities that enable unauthorized transactions, financial fraud, or theft of funds can lead to substantial financial losses for individuals and businesses.
- Reputation Damage: Exploiting vulnerabilities can erode the trust customers and stakeholders have in an organization. News of security breaches or compromised systems can lead to reputational damage and loss of business.
Understanding Vulnerability Management
Vulnerability management is a critical component of any comprehensive cybersecurity strategy. It involves identifying, assessing, prioritizing, and mitigating vulnerabilities in the organization's systems, applications, and network infrastructure. The goal is to empower organizations to proactively eliminate potential points of exploitation, fortifying their defenses and reducing exposure to potential cyber threats.
How does Falcon Spotlight help us to manage and perform vulnerability management
CrowdStrike Falcon Spotlight is a state-of-the-art vulnerability management tool that empowers organizations to proactively address security vulnerabilities. Developed by CrowdStrike, a recognized leader in cybersecurity, Falcon Spotlight offers a holistic approach to vulnerability management, providing real-time insights, seamless integration, and actionable intelligence.
Here's how Falcon Spotlight helps organizations effectively manage and perform vulnerability management:
- Real-time Visibility: Falcon Spotlight offers real-time visibility into vulnerabilities across your entire digital environment, including endpoints, servers, and cloud infrastructure. This visibility is crucial for identifying vulnerabilities promptly and comprehensively.
- Continuous Monitoring: The solution provides continuous monitoring, ensuring that vulnerabilities are discovered and addressed as they emerge. This proactive approach minimizes the window of opportunity for attackers to exploit vulnerabilities, reducing the organization's risk exposure.
- Discovery and Assessment: Falcon Spotlight identifies vulnerabilities by scanning the systems, applications, and networks. It goes beyond simple scanning by assessing vulnerabilities in the context of your organization's environment. This assessment helps determine the potential impact and criticality of each vulnerability.
- Risk Prioritization: Leveraging machine learning and threat intelligence, Falcon Spotlight assigns risk scores to vulnerabilities based on their potential impact and exploitability. This prioritization allows security teams to focus on addressing the most critical vulnerabilities that pose the highest risk to the organization.
- Integrated Platform: Falcon Spotlight is part of the broader CrowdStrike Falcon platform, which integrates endpoint protection, threat detection, incident response, and vulnerability management. This integration streamlines workflows, allowing security teams to manage vulnerabilities within the same platform they use for other security operations.
- User-friendly Interface: The user interface of Falcon Spotlight is designed to be intuitive and user-friendly. Dashboards and reports provide clear visualizations of vulnerability data, making it easier for security teams to understand and navigate the vulnerability landscape.
- Comprehensive Reporting: Falcon Spotlight generates detailed reports that provide insights into the vulnerability landscape, risk scores, and the status of remediation efforts. These reports are valuable for communication with stakeholders and for demonstrating compliance with security standards.
- Integration with Existing Tools: Falcon Spotlight supports integrations with other security tools and solutions, allowing organizations to enhance their existing vulnerability management processes. This interoperability enhances the overall effectiveness of the vulnerability management program.
- Support for Compliance: Effective vulnerability management is often a requirement for compliance with various industry regulations and standards. Falcon Spotlight helps organizations meet these requirements by providing the tools needed to identify, assess, and remediate vulnerabilities.
In essence, CrowdStrike Falcon Spotlight equips organizations with the tools and capabilities needed to identify, assess, prioritize, and mitigate vulnerabilities effectively. By providing real-time visibility, risk-based prioritization, and integration with a unified security platform, Falcon Spotlight empowers security teams to proactively manage vulnerabilities and reduce the organization's exposure to cyber threats.
Usage of Spotlight at Halodoc:
At Halodoc, we implement a Single Sign-On (SSO) authentication method, enabling seamless access to the Falcon Spotlight dashboard.
We have established distinct role levels within the security team, ensuring restricted access and granting configuration with least privileges only for authorized personnel.
Falcon Administrator: Access all functionality in the console except certain Real Time Response (RTR) functionality.
Vulnerability Manager: Manage all vulnerability management functionality.
Falcon Analyst: Manage detections and quarantined files and view exclusions and host management. Create and manage scheduled searches and view and download the results. View Falcon Sandbox submissions and reports. View FileVantage file integrity policies, rule groups, and activity. View firewall rules, rule groups, policies, and firewall events. Download Forensics app. View asset data and registered accounts in Cloud Workloads Discovery.
Dashboard Admin: Create, edit, manage, and delete dashboards. This role does not grant basic Falcon console access. Users assigned this role must have at least one other role assigned to access the Falcon console.
Scheduled Report Admin: can assign and revoke the Scheduled Report Analyst role, create scheduled reports, view and manage any scheduled report in the CID, and view, download, and delete any generated report in the CID.
To monitor the vulnerabilities in the halodoc assets, we need to install the agent in the user's assets.
Steps to install Falcon agent:
Installing the CrowdStrike Falcon agent on user assets involves a series of steps to ensure proper deployment and protection. The CrowdStrike Falcon agent is designed to provide advanced endpoint security, threat detection, and response capabilities.
Note: These steps provide a high-level overview of the installation process. Refer to CrowdStrike's official documentation for the most up-to-date and detailed instructions.
- Create Host Groups (Optional):
If desired, create host groups to organize and manage user assets based on roles, departments, or other criteria. - Download Installation Package:
In the Falcon console, navigate to the "Hosts" section or here.
Choose the appropriate host group or the assets you want to install the agent on.
Select the option to download the installation package for the specific operating system. - Deploy the Installation Package:
There are multiple methods to deploy the installation package to user assets:
a. Manual Installation:
Manually install the downloaded Falcon agent package on each user asset.
Run the installer and follow the on-screen prompts.
You might need administrative privileges to install software.
b. Software Distribution Tools:
Utilize software distribution tools like SCCM, Jamf, or others to deploy the Falcon agent across multiple assets simultaneously.
c. Group Policy (Windows):
If you are deploying on Windows, use Group Policy to automate the installation process.
Installation Demo:
Prerequisites:
Installing the CrowdStrike Falcon agent in the user assets requires elevated privileges(Administrator Privileges).
Browser Dependencies:
CrowdStrike currently supports the Google Chrome browser for use with the Falcon UI. Other browsers may work, but we do not support other browsers at this time.
Installing the Falcon Agent in the Mac:
1. Login to the CrowdStrike Falcon Platform. Access the CrowdStrike Falcon console using your administrator credentials.
2. Create a New Host Group (Optional):
You can create a host group to organize and manage your endpoints effectively. This step is optional but can help with policy management.
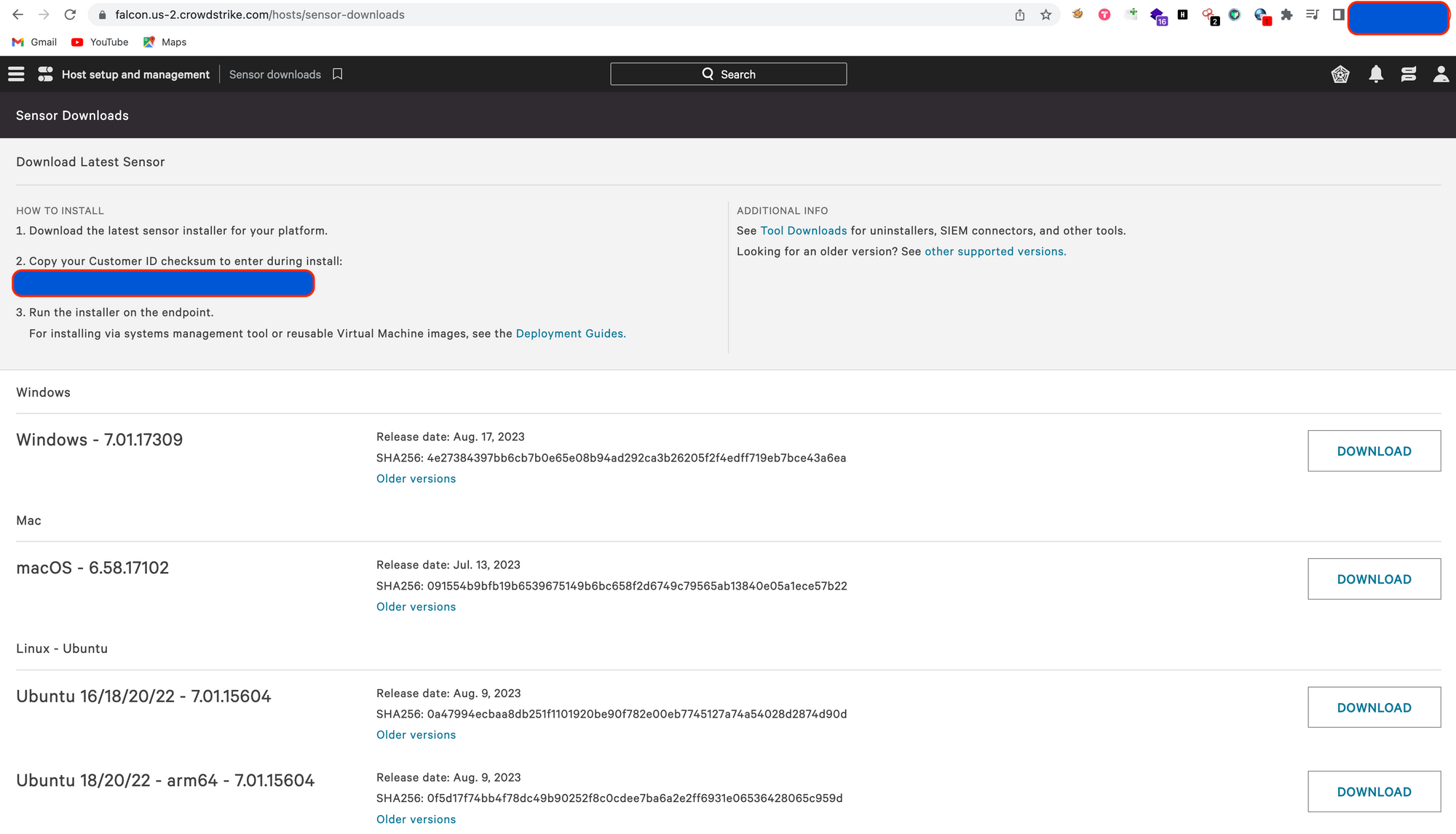
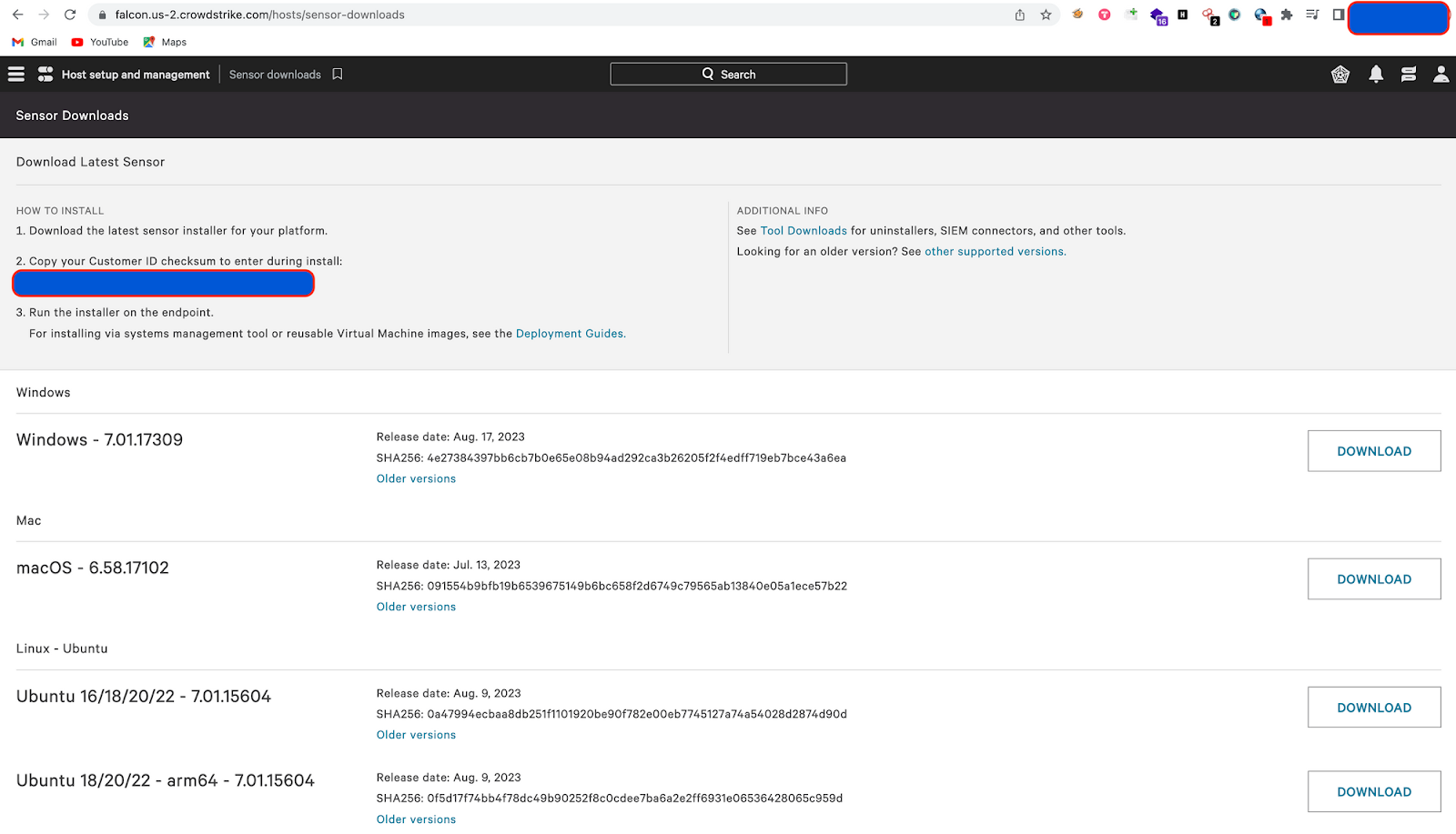
3. Download the agent installer from Host setup and Management > Sensor Downloads option
4. Navigating to sensor downloads
5. Copy your Customer ID Checksum (CID)
6. Download the CrowdStrike Agent Installer.
Select the operating system of the user's laptop (e.g., Windows, macOS, Linux).
Click "Download" or a similar option to download the agent installer for the user's laptop. This will generate an installer package customized for your organization.
7. Distribute the Installer to the User's Laptop:
You can distribute the installer package using various methods, depending on your organization's policies and the user's laptop's environment:
- Email the installer package to the user.
- Upload it to a file-sharing service and provide the user with a download link.
- Use a software deployment tool if your organization has one in place.
8. Run the Installer on the User's Laptop:
During the installation, the user may need to provide an authentication token provided by the Falcon platform.
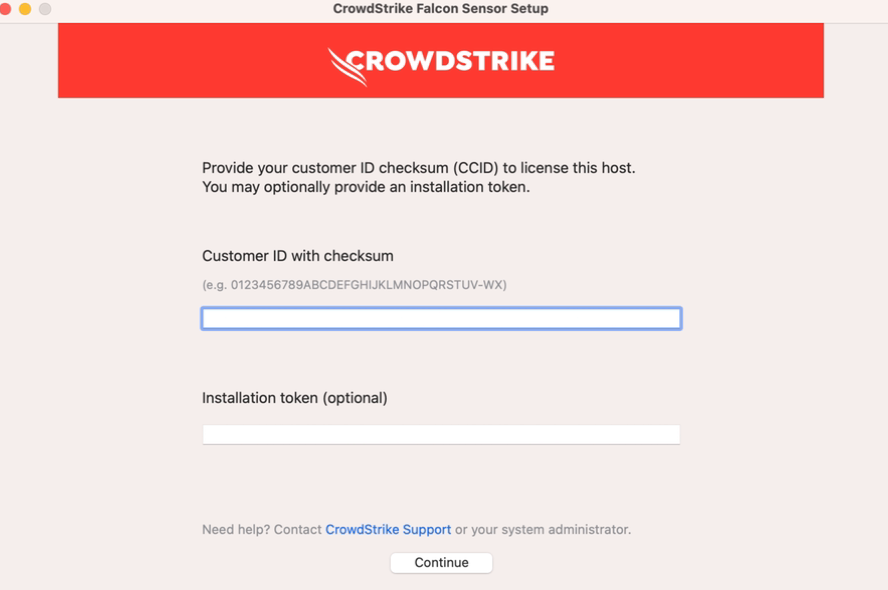
The user should open the installer package and follow the on-screen instructions to install the CrowdStrike agent.
When the System Extension Blocked message appears, click Setup to manually approve to filter network content.
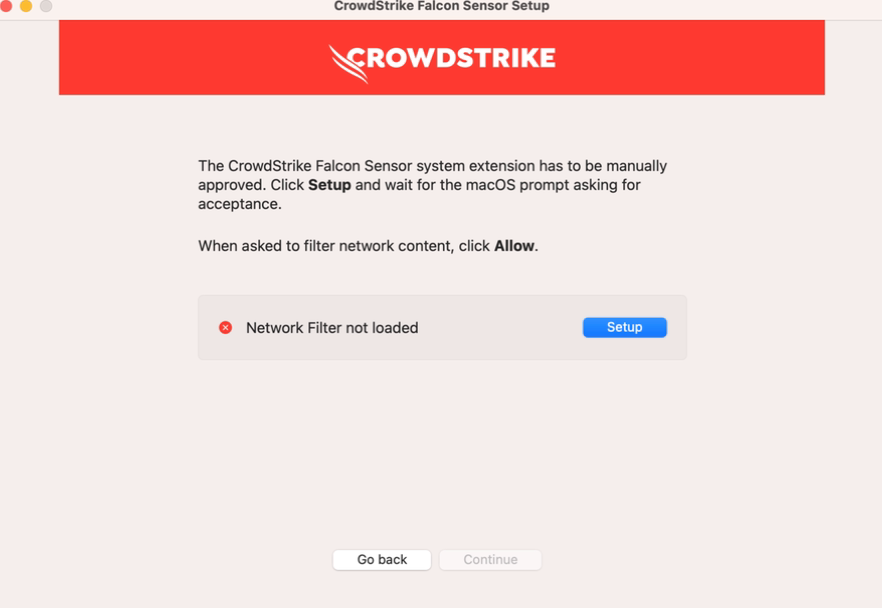
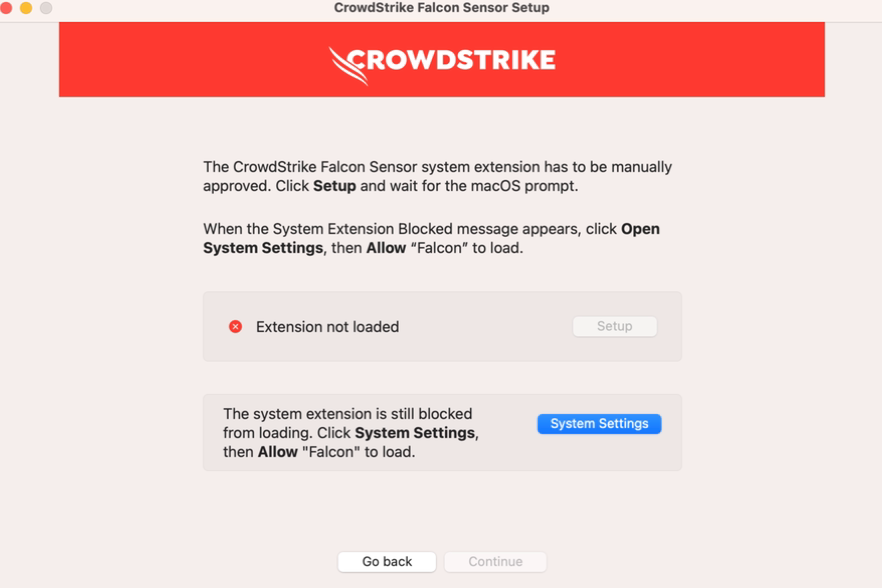
When the System Extension Blocked message appears, click System Settings.
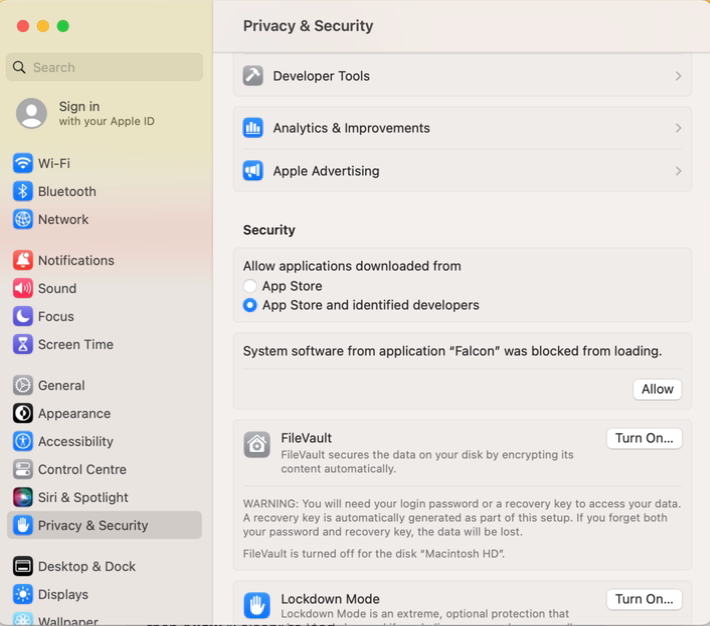
1. Click the Apple icon and open System Preferences, then click Security & Privacy.
2. On the Privacy tab, if privacy settings are locked, click the lock icon and specify the password
When the System Extension Blocked message appears, click System Settings
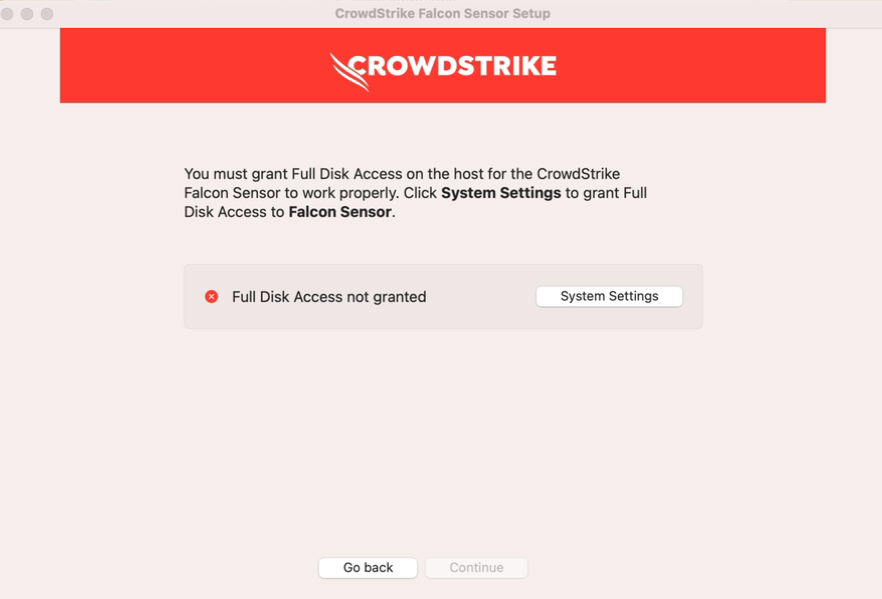
In the Right pane, select Full Disk Access.
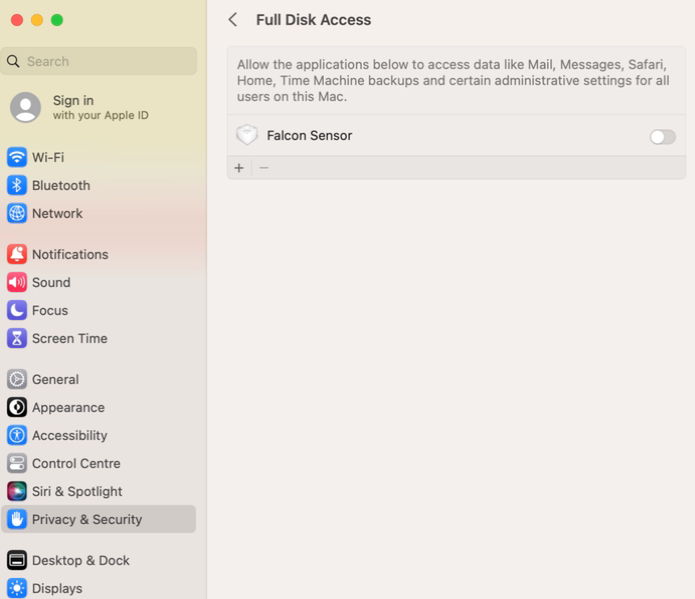
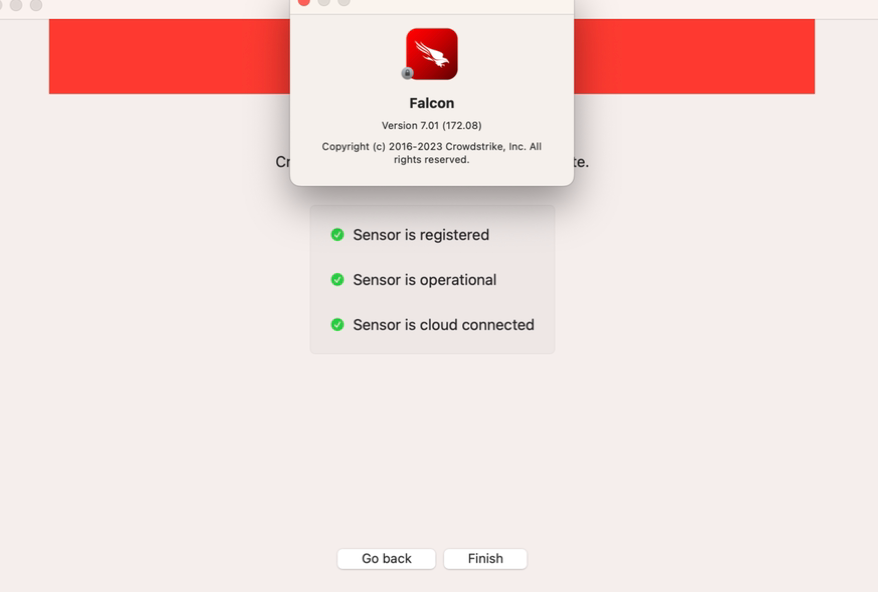
9. Verify Installation:
Once the installation is complete, the user can verify that the CrowdStrike agent is running by checking for its icon in the system tray (Windows) or the menu bar (macOS).
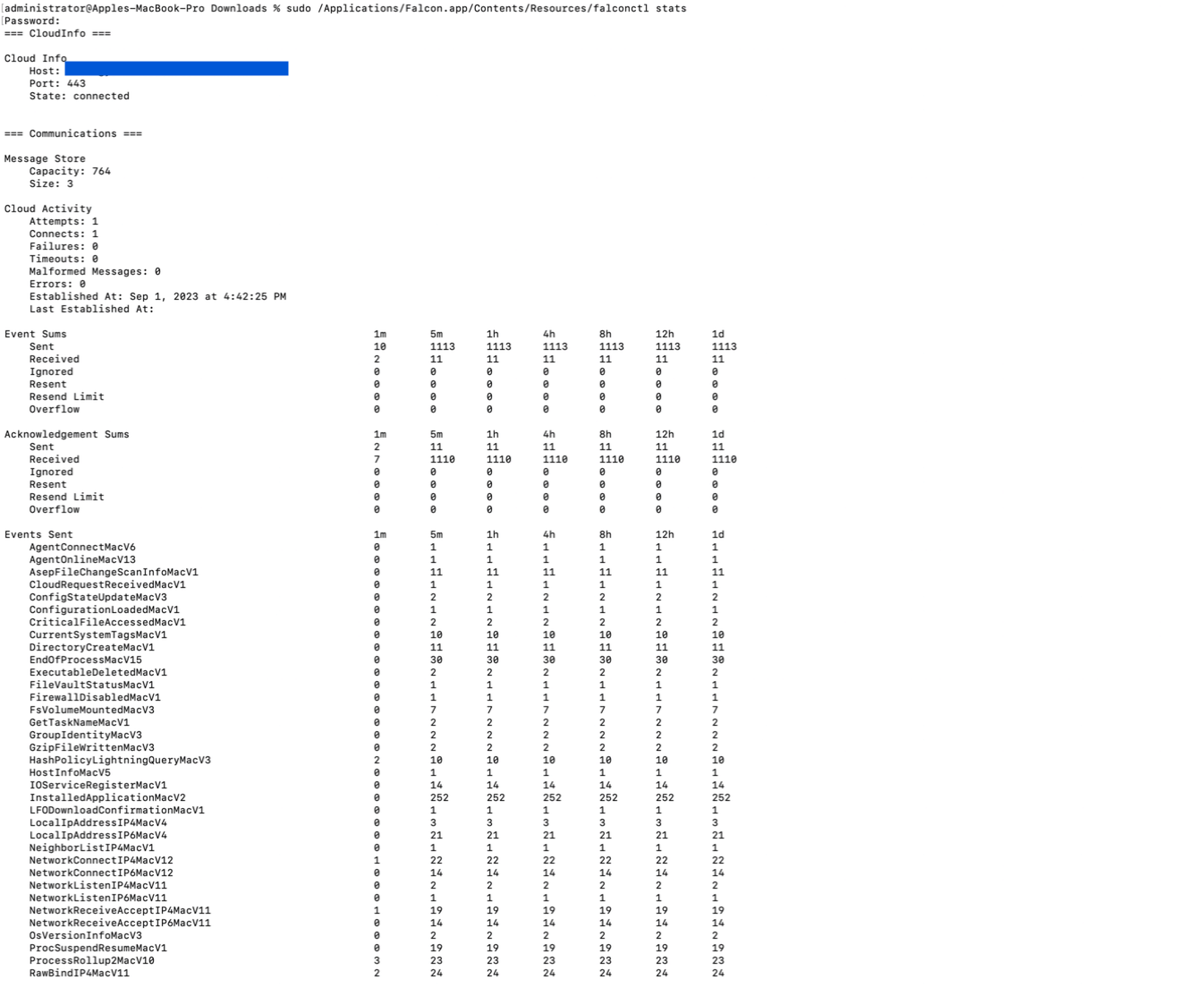
After installation, the sensor runs silently. To confirm that the sensor is running, run this command at a terminal
sudo /Applications/Falcon.app/Contents/Resources/falconctl stats
The output shows a list of details about the sensor, including its agent ID (AID), version, customer ID, and more.
Additionally, you can verify the agent's status in the Falcon console.
10. Configure Policies (Optional):
In the Falcon console, configure security policies for the user's laptop, specifying how the CrowdStrike agent should behave and respond to threats.
11. Monitor and Manage Endpoints:
Use the Falcon console to monitor and manage the user's laptop and other endpoints within your organization. You can view threat alerts, run scans, and apply policies as needed.
- Agent Activation:
Once the Falcon agent is installed, it will need to be activated to connect with the CrowdStrike platform.
The agent should automatically activate after installation, but in some cases, manual activation might be required. - Verification and Monitoring:
After activation, the Falcon agent will start communicating with the CrowdStrike platform.
Monitor the CrowdStrike console to ensure the agent's connectivity and receive real-time threat data. - Policy Configuration (Optional):
Customize security policies in the Falcon console to suit your organization's security needs.
Apply policies to specific host groups or user assets to enforce security settings. - Testing and Validation:
Perform tests to ensure that the Falcon agent is functioning as expected.
Test its ability to detect and respond to threats, as well as communicate with the CrowdStrike platform. - Ongoing Management:
Regularly monitor the CrowdStrike console for security events, alerts, and updates.
Keep the Falcon agent up to date by applying software updates and patches as provided by CrowdStrike.
Remember that specific steps might vary depending on your organization's environment, operating systems, and deployment methods. Always refer to the official CrowdStrike documentation and guidelines for the most accurate and up-to-date installation instructions here.

The Falcon agent will perform the real-time monitoring of vulnerabilities for application's installed in the Halodoc assets and helps to track in the spotlight dashboard.
Based on the requirement of the organization, we can filter out the identified vulnerabilties by the spotlight based on severity, number of days etc.
Crowdstrike provides complete details about the vulnerabilites identified, in order to reduce the amount of time taken to know about the vulnerabilities.
To add a point , we can see two types of severity ratings provided in the dashboard.
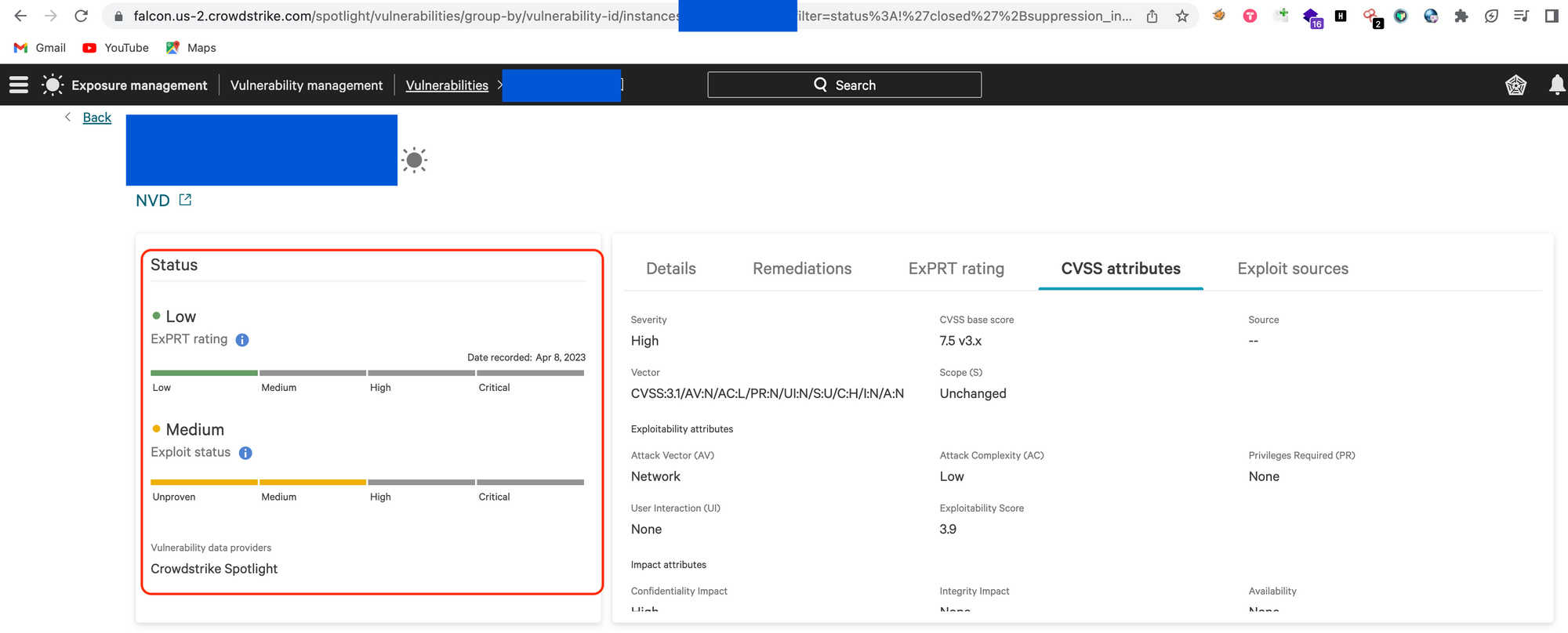
ExPRT Rating: CrowdStrike developed ExPRT.AI for Falcon Spotlight. ExPRT.AI or the Expert Prediction Rating artificial intelligence model capitalizes on a wide variety of vulnerability and threat-based telemetry, including CrowdStrike’s own threat intelligence to provide a dynamic, responsive ExPRT Rating within Falcon Spotlight’s console.
The advanced real-time artificial intelligence model is continuously monitoring the evolving threat landscape to evaluate the likelihood of exploitation.
The Falcon Spotlight ExPRT Rating is dynamically adjusted based on the likelihood of exploitation. This enables security teams to proactively prioritize the small percentage of vulnerabilities that are likely to be exploited, instead of reacting once vulnerabilities are exploited.
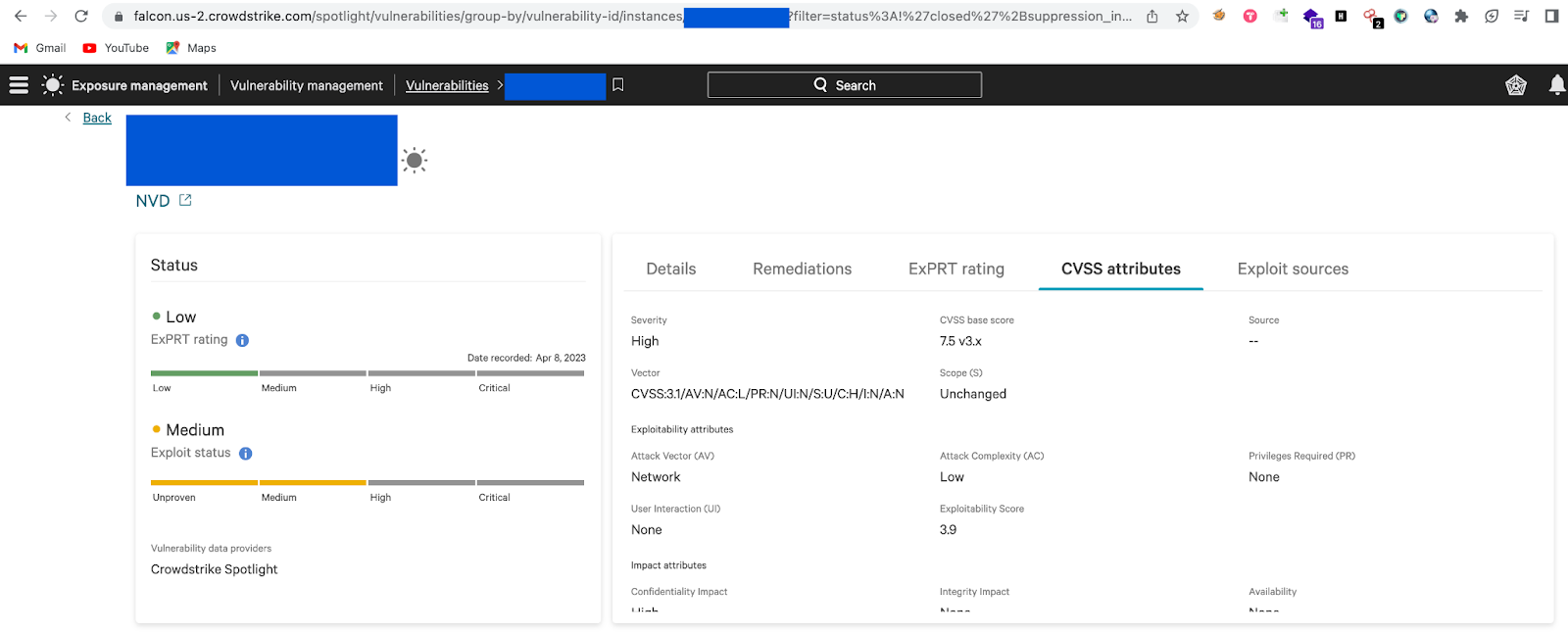
CVSS Severity: CVSS stands for Common Vulnerability Scoring System. It is a standardized framework used to assess and communicate the severity of vulnerabilities in software systems, networks, and applications. The CVSS score provides a quantitative representation of the risk associated with a particular vulnerability, helping organizations prioritize their efforts in addressing security issues. The score is intended to assist in decision-making processes related to vulnerability management.
The CVSS framework comprises several metrics that collectively contribute to calculating a numeric score. The resulting score is divided into three severity levels: Low, Medium, and High.
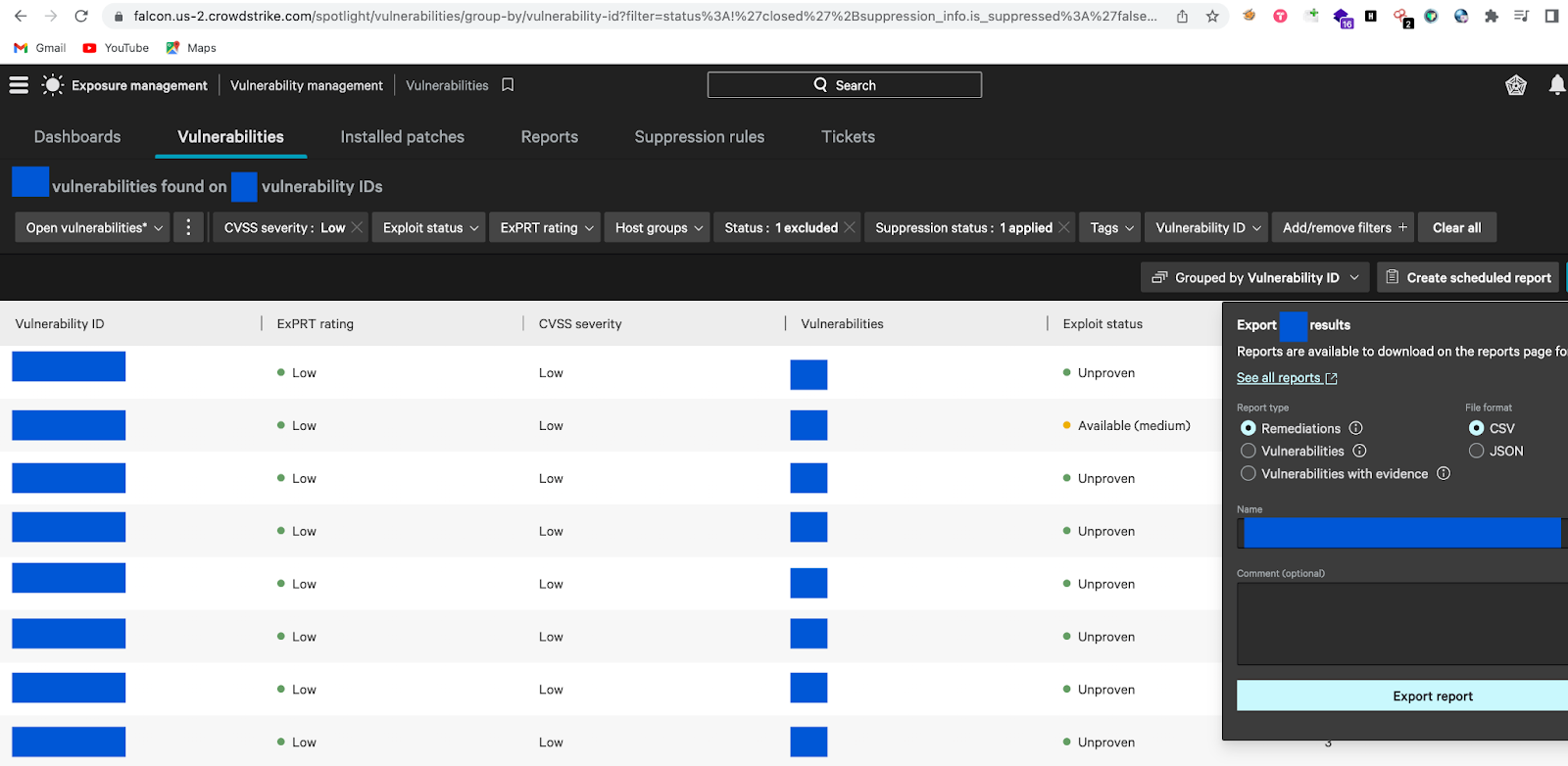
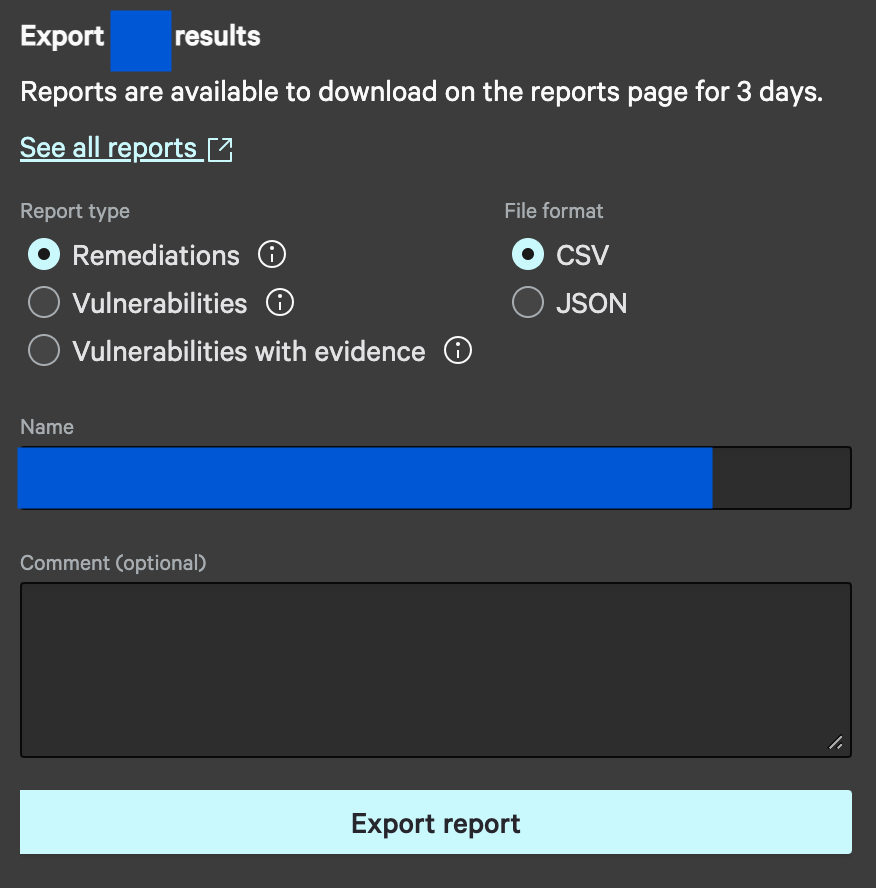
Falcon Spotlight also helped us to create the report on the identified vulnerabilities easily which was easy to understand and track the patch update. The reports can be generated in two formats (JSON and CSV). Based on the organization's needs we can choose the report format.
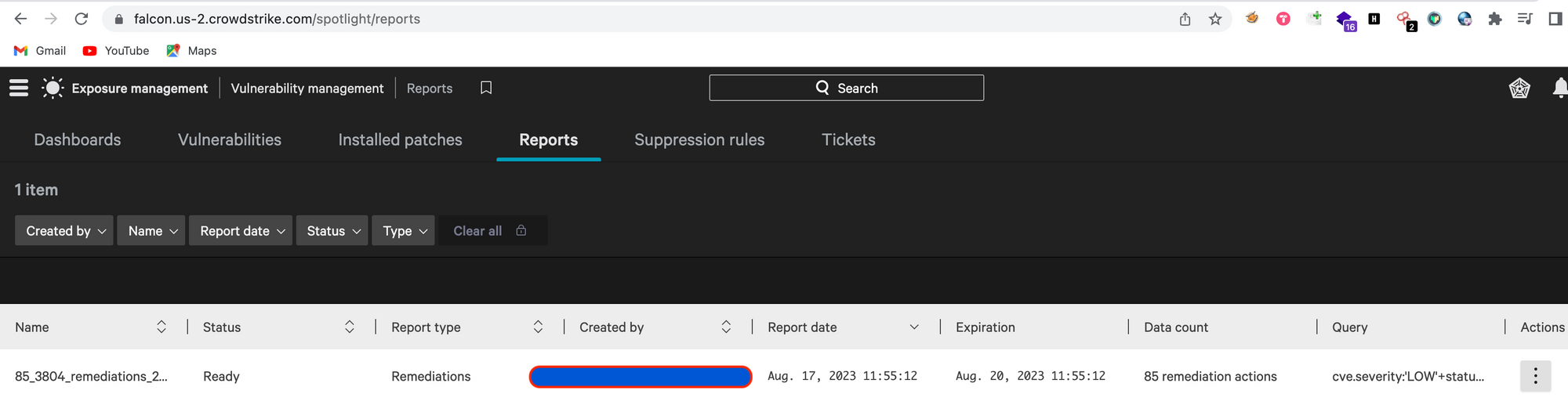
Note: The report generated by spotlight will available in the dashboard only for 3 days, after that it will be deleted automatically.
Once the report was generated , we shared the report with Patch Management team. The Patch management team will do the patches to reported assets using ManageEngine.
Conclusion
In the ever-evolving landscape of cybersecurity, having a robust vulnerability management tool is essential to safeguarding your organization's assets and data. CrowdStrike Falcon Spotlight stands out as an advanced solution that provides real-time insights, prioritization, integration, and automation to effectively manage vulnerabilities.
By adopting Falcon Spotlight, organizations will be able to proactively address vulnerabilities, enhance its security posture, and stay ahead of potential threats in today's digital world. With its cutting-edge features and seamless integration with the CrowdStrike platform, Falcon Spotlight is a powerful tool that empowers organizations to bolster their cybersecurity defenses with confidence.
Join Us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek, and many more. We recently closed our Series D round and in total have raised around USD$100+ million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia..




