Defending against Website Cloning attack with Canary Tokens
In today’s digital landscape, website cloning has become one of the common techniques used by adversaries to deceive users and steal sensitive information. There are several layered approaches to protect against these threats. One of the eminent approach is to use Canary Tokens, which can be leveraged for early detection of website cloning to prevent further attack chain exploitation like domain impersonation and phishing attacks. In this blog post, we will start with an introduction of Canary Token, explaining the benefits of Canary Token, how Halodoc is leveraging Canary Token as our early detection system, and we will continue to take you through on how we handle and remediate the potential threats against the website cloning.
Introduction of Canary Tokens:
The concept of Canary Tokens originates from the miners' practice by using canaries to detect harmful gasses in underground mines. When the canary became distressed or stopped singing, it served as an early warning sign for the miners to evacuate the area quickly. In the world of cybersecurity, the Canary Token serves a similar purpose by acting as an early warning notification to proactively identify the potential threats. Canary Tokens typically appear as normal files or documents that an attacker would find enticing. Once the attacker interacts with the token, it triggers an alert and provides information about the source of the attack, such as the attacker's IP address or location. This allows an organization to promptly respond and analyze the alert to contain the potential threats before getting exploited by the attacker.
These are the lists of the common alert parameter in the Canary Tokens :
- IP Addresses: Canary Tokens capture the IP Address of the system or device that triggered the token. This helps in identifying the source of the potential threat.
- Token Identifier: Each Canary Token has a specific identifier associated with it. The token identifier is recorded to track and identify the token.
- Timestamp Of Access: Canary Tokens record the timestamp of when the token triggered that helps in understanding the timeline of the events.
- User-Agent Information: Canary Tokens also capture user-agent information, revealing details about the device or browser used by the attacker.
- Interaction Context: Canary Tokens will capture some additional context, such as the type of interaction (e.g., accessing a specific file or URL) to ease us understand the nature of the potential threats.
Understanding of Website Cloning and Canary Alerting
Website cloning is a technique wherein attackers create an identical replica of a legitimate website to trick users and obtain confidential information such as username, passwords and web session tokens. Cloned websites are often designed to mimic the original websites, making it challenging for users to identify the authenticity of the cloned websites. The associated risks posed by the website cloning are concerning, as users may not be aware of submitting sensitive information, which will be used by the attacker for various malicious intent, such as identity theft, financial fraud, or unauthorized access to the victim's accounts. To detect website cloning, Canary Token compares the origin domain of the legitimate website with the domain of the cloned website. If the domains do not match, alerts will be sent via email or messaging applications, allowing Cybersecurity team to promptly respond to the Canary alerts.
Advantages of Implementing Canary Tokens:
- Proactive Detection In Website Cloning: Canary Tokens introduce a proactive approach to detecting website cloning, enabling organizations to identify unauthorized attempts before they escalate into full-scale attacks.
- Immediate Alerting: Upon any interaction with the Canary Tokens, alerts are triggered instantly, allowing Cybersecurity teams to respond swiftly to potential threats.
- Real-Time Monitoring: Canary Tokens provide continuous and real-time monitoring, ensuring that any suspicious activity is detected promptly, minimizing the risk of deceptive clones being established unnoticeable.
- Granular Insights: Canary Tokens capture detailed information such as IP addresses, timestamps, and interaction context, providing valuable insights into the tactics and methods used by the attackers.
- Lure The Attackers: Besides detection of unauthorized cloning, Canary Tokens also serve the purpose of attracting the attackers. By strategically placing Canary Tokens in various locations such as S3 bucket objects, kubernetes configurations, AWS keys, and other enticing assets, organizations effectively lure the potential attackers to reveal their presences.
- Reduced Risk Of Data Breach: By enabling early detection, Canary Tokens help mitigate the risk of unauthorized access and compromise of sensitive information, safeguarding user data and organizational assets.
Implementation flow of Canary Tokens for Website Cloning Detection and Response:
- Canary Token Generation:
Generate a web cloning Canary Token at https://canarytokens.org/generate, configuring it as a script. This token acts as a digital trap, triggering alerts when unauthorized activities like website cloning occur.
- Obfuscation For Enhanced Stealth:
Apply obfuscation techniques to the generated script to obscure its purpose effectively. Obfuscation introduces complexity, making it challenging for potential attackers to decipher the script's functionality. This increased complexity enhances the likelihood of successful integration into cloned websites, ensuring the Canary Token remains covert and effective.
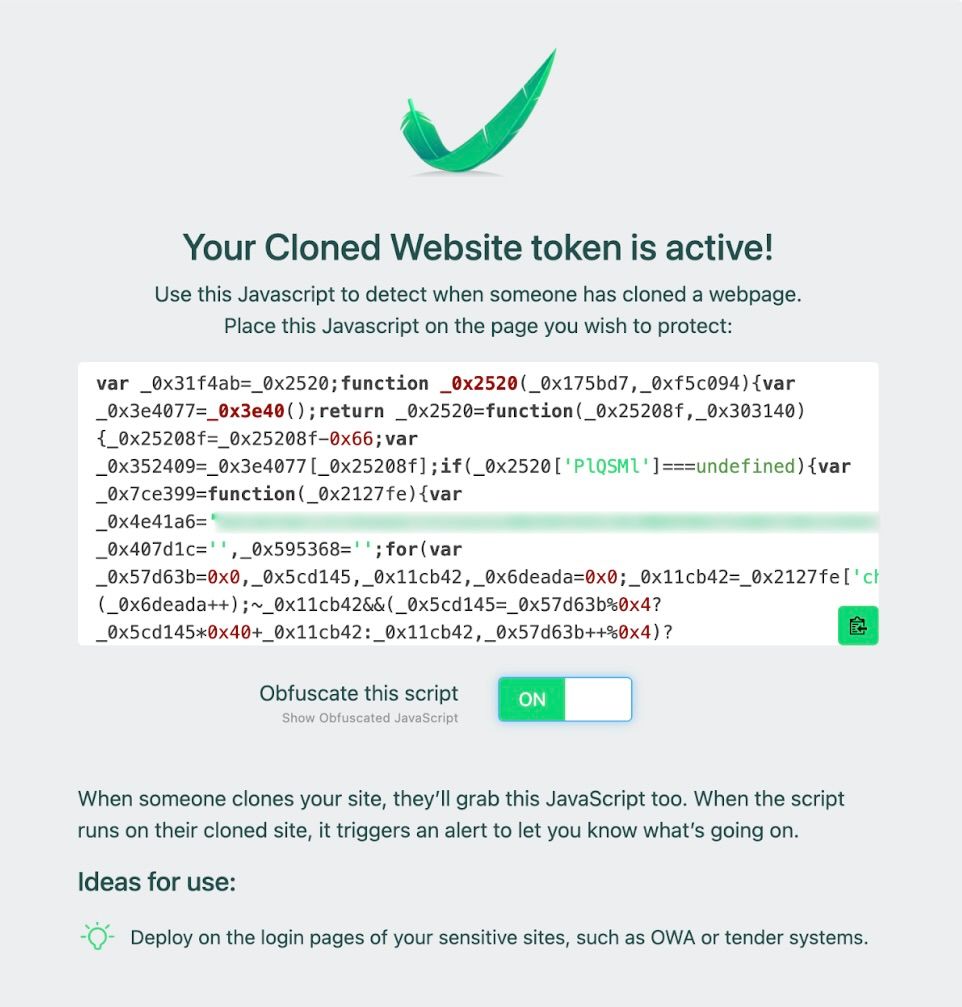
- Covert Token Deployment:
Embedding the obfuscated JavaScript discreetly within the digital assets ensures the covert deployment of the Canary Token, enhancing the detection capability for unauthorized activities like website cloning while minimizing the risk of detection by the attackers. - Detection Of Cloning Through Alerts:
Upon receiving alerts generated by Canary Tokens, we should promptly investigate the reported activity and assess the severity of alerts to determine the appropriate response based on our defined security playbook. Some cloned websites may be locally hosted which do not require any action, while others cloned websites that contain many redflags may require immediate attention.
Website Cloning Defense and Response
- Alert Analysis And Prioritization: Upon receiving alerts triggered by Canary Tokens, an analysis of the reported activity will be initiated based on severity and potential impact on organizational assets and data. Some cloned websites may pose minimal threats if locally hosted, while others may require immediate attention due to their potential to compromise sensitive information or deceive users.
- Domain Characteristics Evaluation: Analysis of the reported domain is conducted to identify its characteristics and behavior by utilizing threat intelligence platforms and manual analysis techniques to assess the presence of phishing elements, malicious scripts, or other indicators of compromise. Initially, registrar information is scrutinized using WHOIS lookup services to ascertain ownership details and registration history. Subsequently, the Threat Intelligence Platform (TIP) is employed to gauge the domain's reputation score, highlighting any past associations with malicious activities and to determine its potential threat level and impact on organizational security.
- Phishing Element Identification: Attention is paid to identifying any presence of phishing elements on the cloned website, encompassing a thorough examination of various indicators such as suspicious URLs, forms soliciting sensitive information, or deceptive design elements intended to deceive users into disclosing personal or financial data. Additionally, the presence of MX Records is checked using common OSINT websites like https://mxtoolbox.com, which can provide insights into potential phishing activities. Any detected phishing attempts are promptly flagged and reported to mitigate the risk of data compromise and safeguard user trust.
- IOC Documentation And Integration Across Security Perimeters: The documentation process involves capturing all relevant Indicators of Compromise (IOCs) associated with potential website cloning activities. This includes recording domains, IP addresses, and any hashes identified during the investigation. These IOCs are then disseminated across various security perimeters, such as Crowdstrike, Firewall, Web Application Firewall (WAF), and Google Workspace, to ensure comprehensive coverage and proactive threat mitigation.
- Takedown Procedures Initiation: Upon confirmation of a cloning website, collaboration with relevant stakeholders is initiated to swiftly commence takedown procedures. This involves close coordination with domain registrars, hosting providers, legal authorities, and leveraging the Threat Intelligence Platform SOCRadar to faciliate takedown process. Documentation of the takedown process and outcomes is undertaken for future reference and improvement.
Result
The implementation of Canary Tokens for website cloning detection has shown promising results in identifying and alerting cloning attempts. By covertly monitoring web page access and comparing it to the expected domain, these tokens provide early alerts, allowing to respond swiftly to potential threats. Below is an illustration of an alert that was activated and subsequently dispatched to the designated email address.
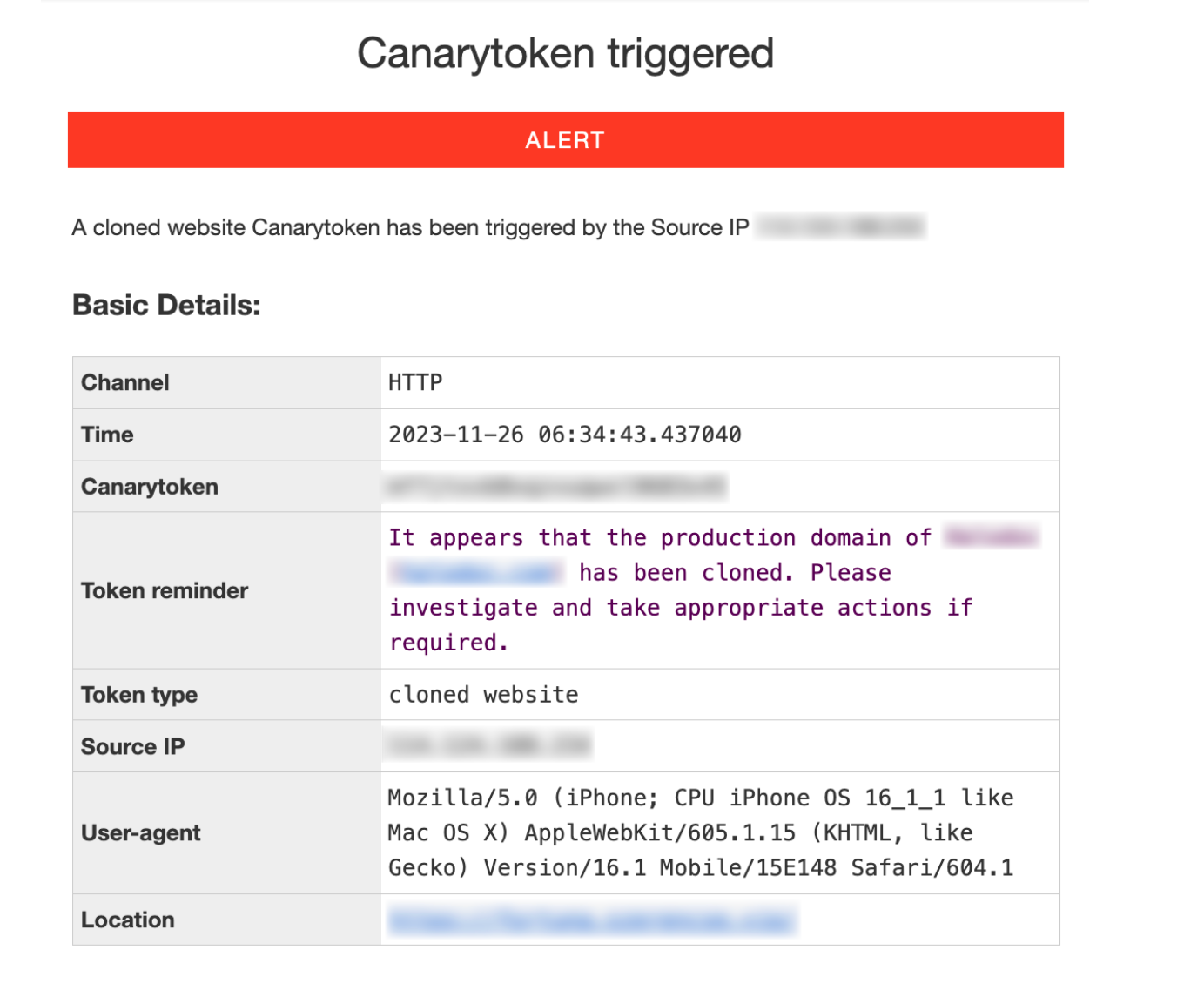
Upon comparing the domain reported in the alert to the legitimate domain, it becomes apparent that the website has been replicated.
Cloned Website:
Original Website:
Conclusion
In conclusion, Canary Tokens emerge as a robust defense mechanism against website cloning, serving as an early warning system that enhances our visibility from the external threats. This proactive approach enables us to swiftly identify and neutralize potential threats posed by website cloning that may impact our digital assets and improve the overall security posture of our organization.
Join Us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek, and many more. We recently closed our Series C round and In total have raised around USD$180 million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.
