Implementing AWS Single Sign On (SSO) using G-suite
At Halodoc, we were providing access to AWS accounts using IAM Service. The issue with this approach is that managing IAM users and their access lifecycle is a cumbersome and time consuming activity especially around activation and deactivation of accounts, elevated privileges etc. This problem is magnified if there are multiple AWS accounts to manage. Another significant security challenge is the management of access and secret access keys across users across accounts.
In order to address the challenges detailed above and simplify our AWS security and its associated management, we reviewed and implemented AWS SSO which will allow us to access specific AWS services via G-suite integration which has the policies defined in the groups.
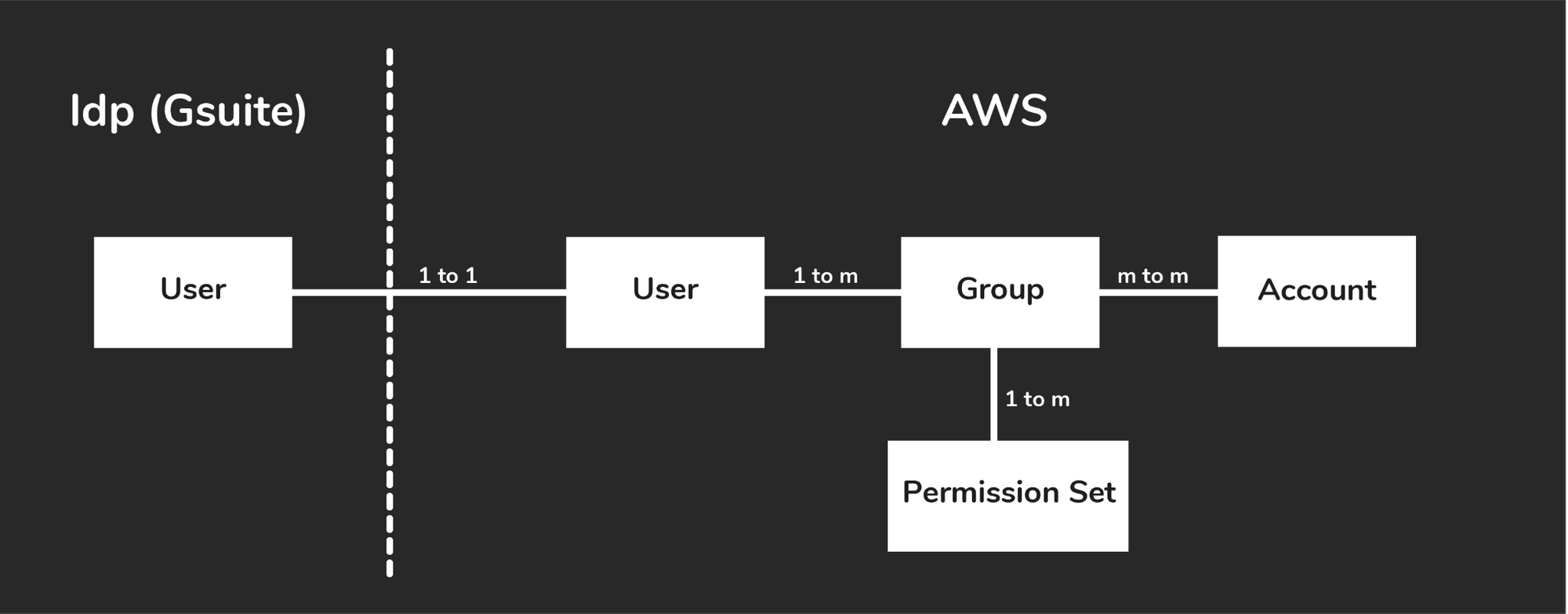
AWS Single Sign-on (AWS SSO) is a cloud service that allows users to access AWS resources such as Amazon EC2 instances, CloudFront, RDS, etc.., across multiple AWS accounts. AWS SSO provides a default store for users and groups. To store them in AWS SSO, all we need to do is the following (refer fig:1):
- Create Users and Groups.
- Add Users as members to the Groups.
- Assign the Groups with the desired level of access via permission set to AWS accounts and applications.
Benefits of AWS SSO
AWS SSO has multiple benefits, for Halodoc, we identified the following three areas to be off highest priority.
- User Management
AWS SSO helps in smooth on-boarding and off-boarding of the users across multiple AWS accounts. Managing users can be done centrally using G-Suite or AWS SSO( using default store) across all the AWS Accounts. One of the benefits of doing this is the rotation of access keys and secret access keys for the users can be automatically achieved via session duration for the users ( which is configurable). - Group Management
AWS SSO also helps in managing groups for the users across multiple AWS Accounts. Groups are useful when assigning access to AWS accounts and applications. Users can be the part of the groups and groups will be assigned to the multiple AWS Accounts. Groups can be centrally managed from G-suite or AWS SSO (using default store) across all the AWS Accounts. - Permission Management
AWS SSO gives a capability to assign similar permissions across all the AWS Accounts based on the roles, so that creating multiple policies or roles and tracking will be smooth. This will help in restricting users across services across all the AWS Accounts. Modifying changes on one policy or permission can help to change the permissions for all the AWS Accounts in an organisation.
Implementation steps
At Halodoc, the AWS SSO integration via G-Suite was achieved by using the high level steps detailed below:
- Enabling AWS SSO in master account
- Integration G-Suite with AWS SS
2.1 Create SAML application
2.2 Creation of groups in G-Suite
2.3 Mapping G-Suite with AWS SSO - Creation of permission sets
- Creation of users and groups in AWS SSO
Enabling AWS SSO in master account
- Open AWS SSO from AWS Console.
- Enable AWS SSO.
- On the overview page of the service, select Choose your identity source.
- In the Settings, check the Identity source and choose Change.
- For G Suite as an identity provider, switch to an external identity provider. User External identity provider from the available identity source.
- Choosing the External identity provider reveals additional information needed to configure it. Choose Show individual metadata values to show the information you need to configure a custom SAML application.
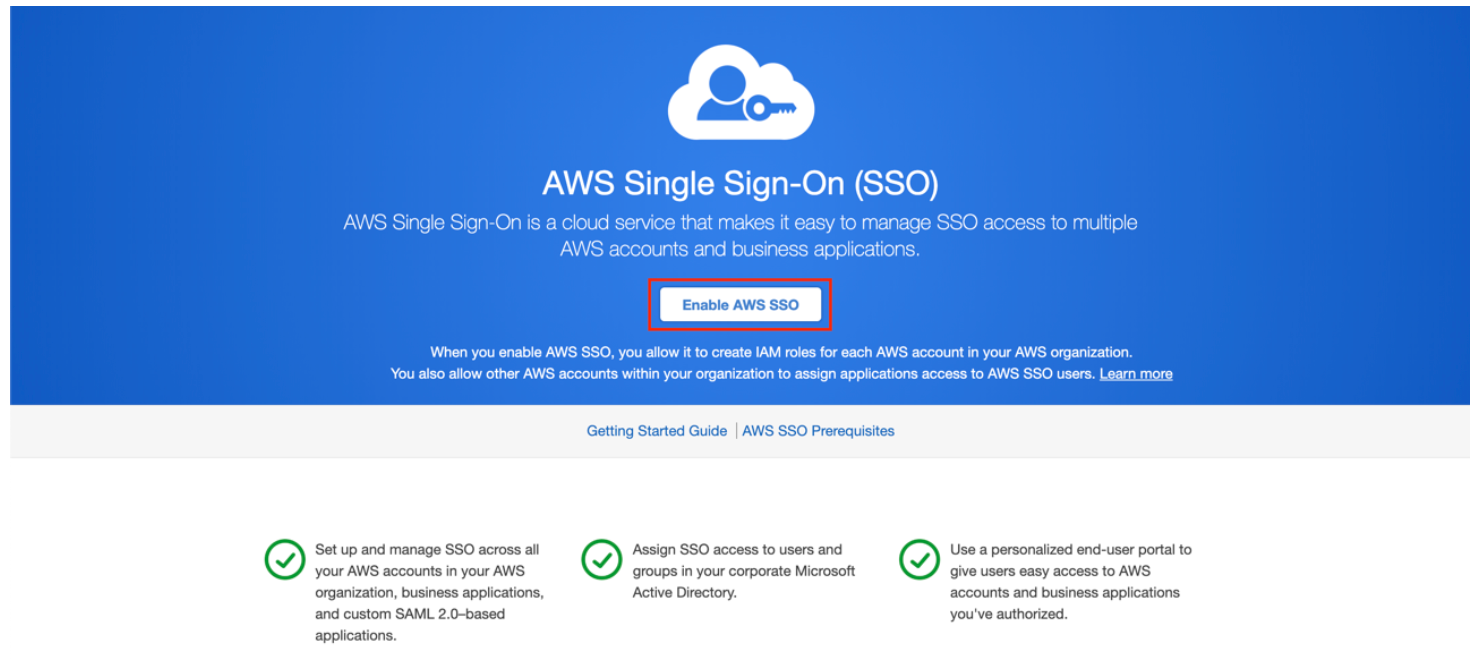
This information will be used in the G-suite account for creating AWS SAML.
Integration G-Suite with AWS SSO
Creation SAML Application
- On the G-Suite account in Google Admin console, Add custom SAML app.
- Add the APP Name and add the Icon of AWS( This will viewed by all the users)
- Download Metadata IDP which will be used in IDP of AWS SSO.
- Using the data from AWS SSO, provide information in the Service provider details, and then choose CONTINUE. The mapping for the data is as follows:
- For ACS URL, Enter the AWS SSO ACS URL.
- For Entity ID, Enter the AWS SSO Issue URL.
- For the Start URL, Leave the field blank.
- For Name ID format, Choose EMAIL.
- For Name ID, Choose Basic Information > Primary email.
- On the Attribute mapping screen, leave the default settings and choose FINISH.
- In the Service status section, select OFF for everyone and choose SAVE. ( This will help in authentication only the user which will need the access )
Creation of Groups in G-Suite
- On the Admin console Home page, navigate to Groups.
- In the upper-left corner, click Create group. This group will be used to give access to the user.
- Add this group to the APP created Earlier and enable service status as on.
Note: This step is used for automatic sync of the groups to the AWS SSO. If we want to manually create a group and user then we can skip this step.
Mapping G-Suite with AWS SSO
- The downloaded Metadata IDP will be used for mapping G-suite accounts.
- Go to the AWS SSO page we configured in Step 1.
- Click on Browse, and add the Metadata IDP.
- Click Review and confirm.
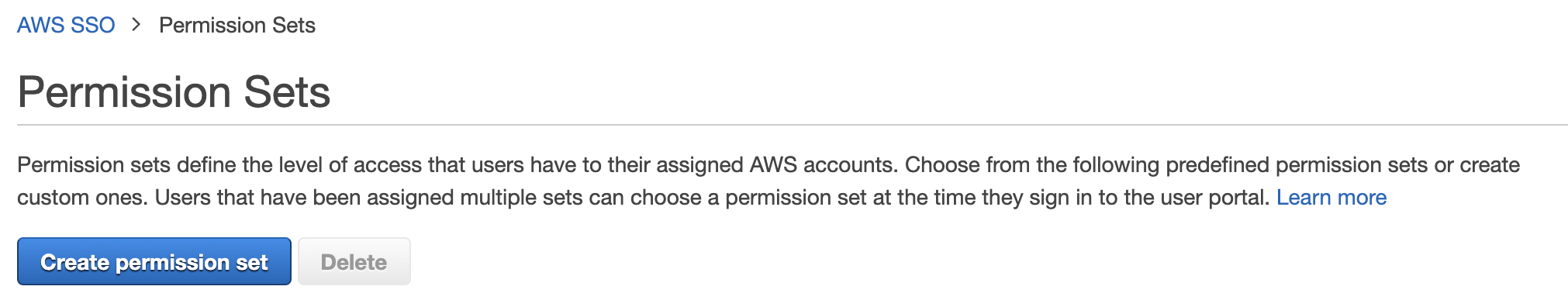
Creation of Permission Sets
- Open AWS SSO from AWS console.
- Select AWS accounts from the left Tab, you will be able to see the permissions set tab.
- Choose the permissions set and click on create permissions set.
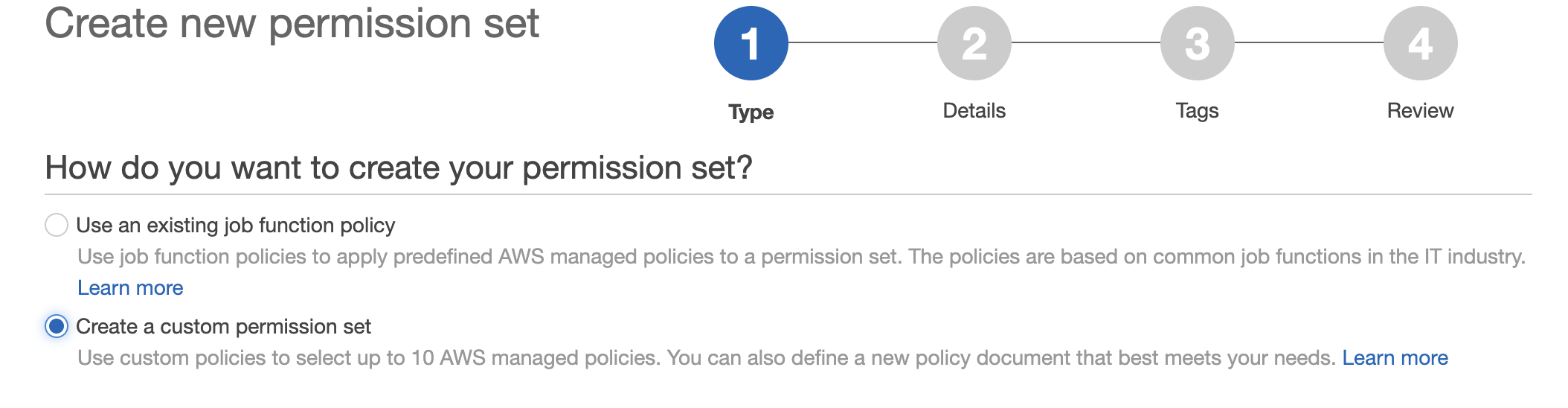
- Choose Create a custom permission set, and click next.
- After that provide Name, Session durations and choose any one from the policy you want to apply.
- Create a policy you want to assign to the users and attach to it.
- Click create
Creation of Users and Groups in AWS SSO
- Go to AWS SSO Console
- Click on groups link on the left side menu.
- Give the group name and description required to be created.
- After creation of the group , add users to the group. Users will automatically get populated.
Note: The above steps is for manually creation of groups and users to the AWS SSO.
For dynamic provision of Groups in AWS SSO using G-Suite , We have to write a small lambda function which will help to continuously synchronise the G-suite and AWS SSO account.
The steps and code is already provided by AWS in the public Github repo here.
Benefits observed post implementation
Based on our observations for the last six months post implementation of AWS SSO via G-Suite, we have seen the following benefits.
- User management is structured
We are using automatic provision of the groups in AWS using G-suite as an active directory. So all the groups and users are maintained on G-suite which helped us on better onboarding of the users in multiple AWS accounts. This has also helped us in improving the security with better management of users and groups across all AWS accounts. - Effective management of permissions on multiple AWS accounts.
We have seen that now we don't have to make changes or modify changes for the access to the users or groups in multiple places. Changes made in one policy helps in making changes across all the AWS accounts. It also gave us a better understanding on what type of access the user or group has in each of the AWS accounts which enhanced our security more. - Enhance security of AWS accounts and services.
We have realised after implementation of AWS SSO service, access and secret access keys for the users are rotated automatically using session duration, thereby not needing forceful key rotations. Session duration for the users to the AWS Accounts can be set up according to need which enhances our overall security.
Summary
Based on the above benefits that we've realised, the convenience offered by this integration between G-Suite and AWS SSO has significantly improved our team's productivity and have improved the overall efficiency of our DevOps practice with regards to Identity Management for our cloud infrastructure.
Interested in exploring with us ?
We are always looking out for top engineering talent across all roles for our tech team. If challenging problems that drive big impact enthral you, do reach out to us at careers.india@halodoc.com
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek and many more. We recently closed our Series C round and In total have raised around USD$180 million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalised for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.
References:
https://aws.amazon.com/blogs/security/how-to-use-g-suite-as-external-identity-provider-aws-sso/
https://aws.amazon.com/single-sign-on/
