AWS Client VPN Using SAML Authentication
Halodoc, with its wide range of digital healthcare services, is a pioneer in the Indonesian healthcare industry. Halodoc's extensive portfolio of services, which includes quick telemedicine consultations, rapid medication delivery, lab tests, appointment scheduling, and health insurance access, provides patients with easy-to-use, comprehensive healthcare solutions.
At Halodoc, there are over 1000 employees working from the office and remotely to build and support our platform. To access the services housed in the AWS (Amazon Web Services) Cloud privately, an AWS Client VPN (Virtual Private Network) with mutual authentication (certificate-based) has been provisioned. Initially, during the early days, no challenges were encountered with the mutual authentication, but with the increase in head count, we started to see a few performance overheads, like intermittent VPN disconnections and client VPN servers crashing during the bulk revocation step of certificates during renewals.
This blog walks through how these challenges were mitigated using the SAML (Security Assertion Markup Language)-based authentication approach.
AWS Client VPN: A Quick Overview
AWS Client VPN is a managed service provided by AWS that enables remote user devices to connect to AWS resources, services, and on-premise networks privately and securely.
We host our whole infrastructure on the AWS Cloud, so selecting the AWS managed Client VPN service was a simple option to maintain everything within AWS. This supports advanced authentication methods like MFA (Multi-factor authentication) and federated authentication, providing heightened security measures. Unlike on-premises VPN services constrained by hardware limitations, this is a scalable cloud solution, operating on a pay-as-you-go model to meet varying client demands effectively. It facilitates remote access to both AWS and on-premises networks through a single VPN connection, streamlining connectivity management. Moreover, this is a fully managed service, handling tasks such as automatic configuration, capacity provisioning, and service updates, while offering centralized monitoring of all connections for ease of administration.
Mutual Authentication:
In the mutual authentication method, digital certificates are provided as a form of identity by CAs (Certificate Authorities). Use the server certificate, a digital certificate that has been uploaded to AWS ACM (AWS Certificate Manager), to set up the Client VPN endpoint. Using the same CA that created the server certificate, create a second certificate called a client certificate and share it with the client. Client VPN software uses these client certificates to carry out authentication between the client and the server. Keeping different certificates for client and server helps to cancel a particular client certificate in the event of revoking specific user access.
Disadvantages of certificate-based mutual authentication:
- Upon each user's onboarding, administrators must create new certificates.
- Every time the client certificate expires, the administrator must renew it.
- In order to facilitate future renewal and revocation operations, all user certificates must be safely saved.
- Failure or a miss in the revoke process of the user's VPN certificate may lead to a security risk.
- VPN disconnection while revoking the client certificate, due to a VPN server restart in the backend.
- Due to a limit on the number of certificates it can update at once, VPN servers can occasionally fail while doing bulk certificate renewal operations.
- Once the user establishes a connection with a VPN, they can access all the endpoints reachable from the VPN with no user- or group-level restriction.
AWS VPN Client Access Revoke Flow in Mutual Authentication:
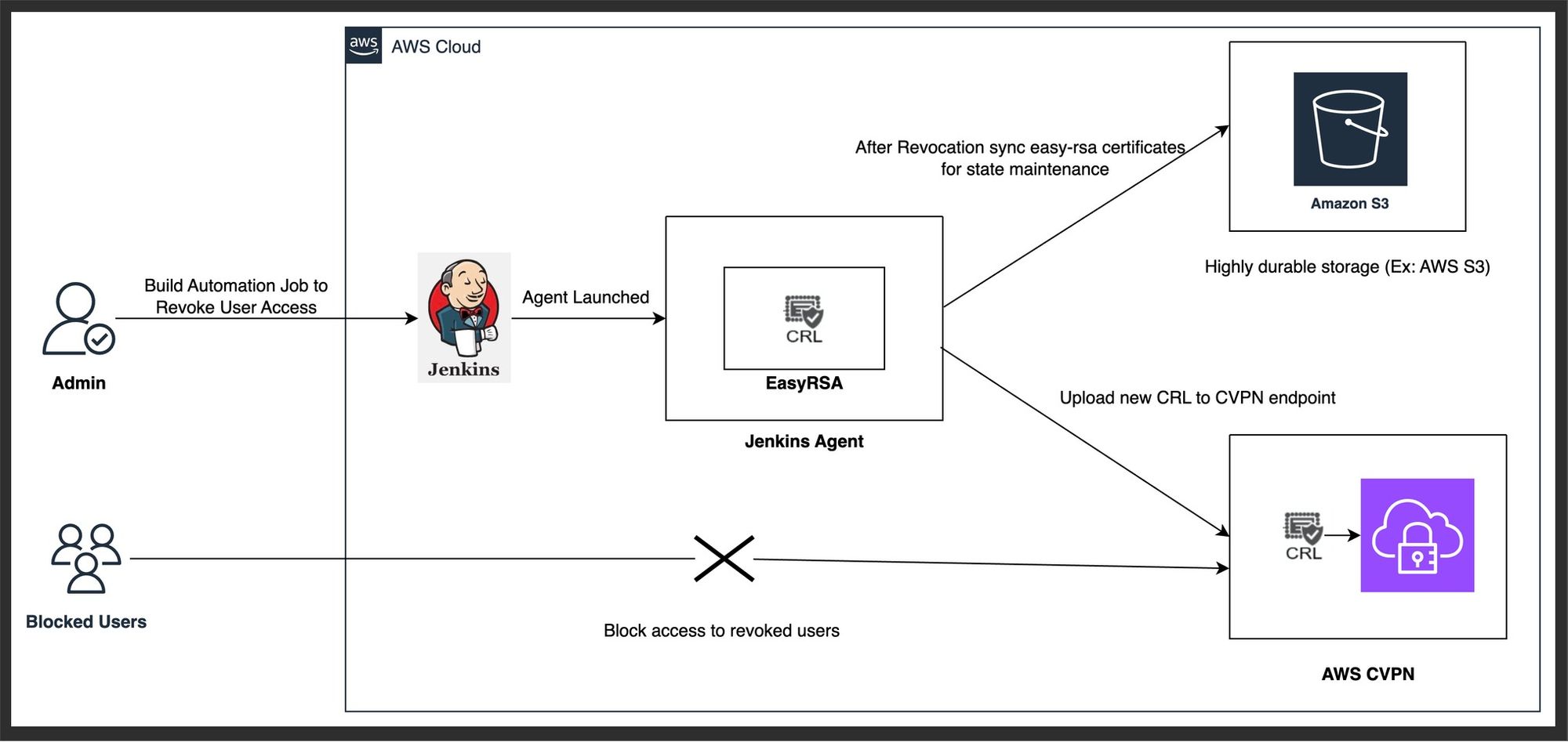
Note: When a user's certificate is revoked and a fresh CRL (certificate revocation list) is sent to the VPN server, all current connections are terminated, not just the revoked user's.
AWS VPN Client Authentication Flow Via Single Sign-On (SAML 2.0-based Federated Authentication):
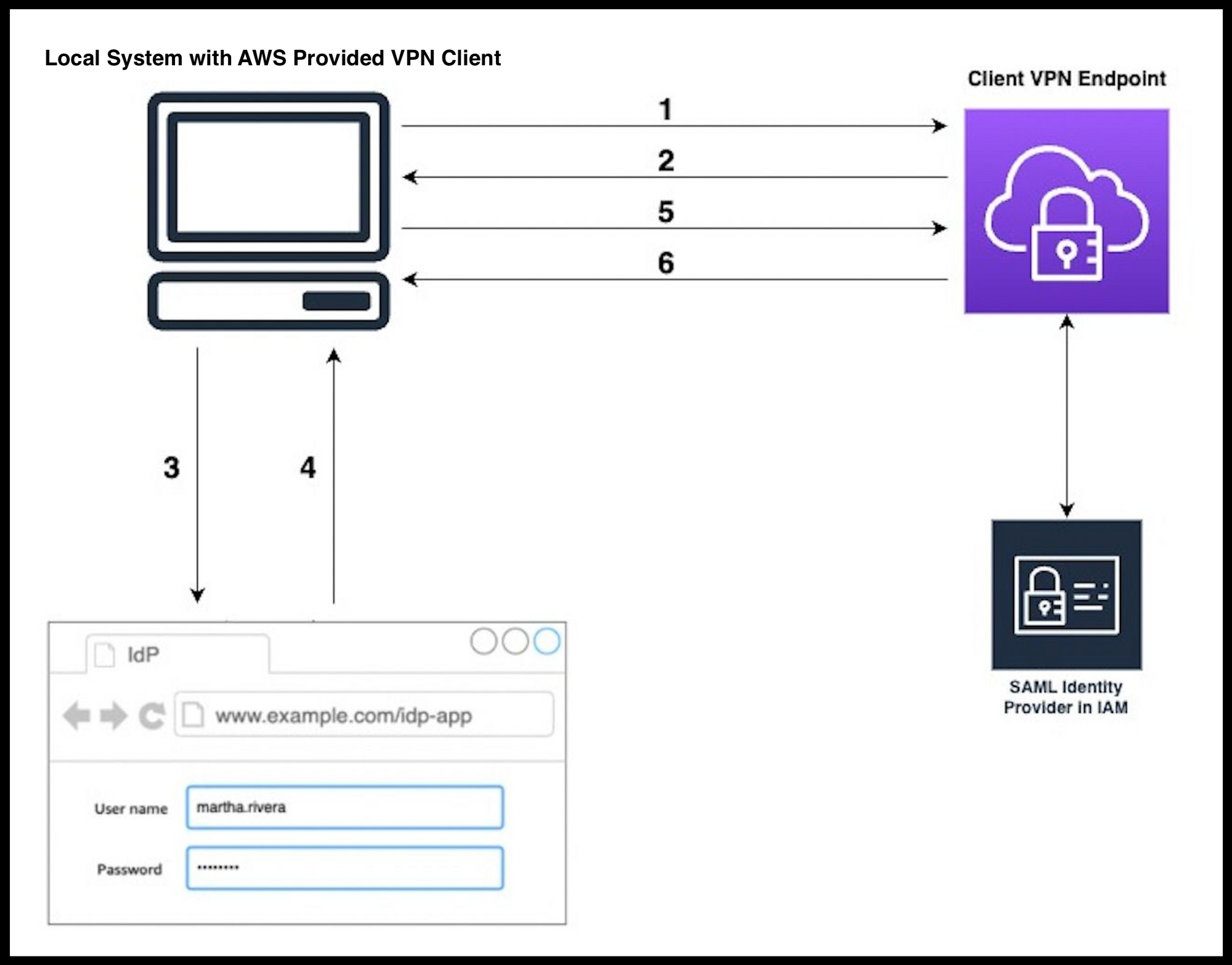
- The user opens the AWS-provided client on their device and initiates a connection to the Client VPN endpoint.
- The Client VPN endpoint sends an IdP (Identity Provider) URL and authentication request back to the client, based on the information that was provided in the IAM SAML identity provider.
- The AWS-provided client application opens a new browser window on the user's device. The browser makes a request to the IdP and displays a login page.
- Then the user enters their credentials on the login page, and the IdP sends a signed SAML assertion back to the client.
- The AWS-provided client sends the SAML assertion to the Client VPN endpoint.
- The Client VPN endpoint validates the assertion and, depending on it, grants or refuses the user access.
Advantages of Single Sign-On (SAML 2.0-based Federated Authentication):
- Eliminates periodic certificate renewal activity.
- Eliminates VPN server outages due to bulk VPN revoke operations.
- There is no need to manage user VPN access explicitly because it is taken care of as part of user onboard and offboard in G-Suite.
- Centralised VPN user management.
- Ability to restrict endpoint access based on user groups.
- Regular password rotation can be enforced in G-Suite.
How to Setup an AWS VPN Client With Single Sign-On (SAML 2.0-based Federated Authentication):
1. Google G-Suite Setup:
- In GSuite Admin account, go to the Admin Console. Select Apps.
- Select SAML apps and add the custom SAML app with meaningful name.
- Under Service Provider Details, please provide the following information:
- ACS URL: https://127.0.0.1:350012
- Entity ID: urn:amazon:webservices:clientvpn3
- Check Signed Response
- Name ID
- Name ID format: UNSPECIFIED
- Name ID: Basic Information > Primary email
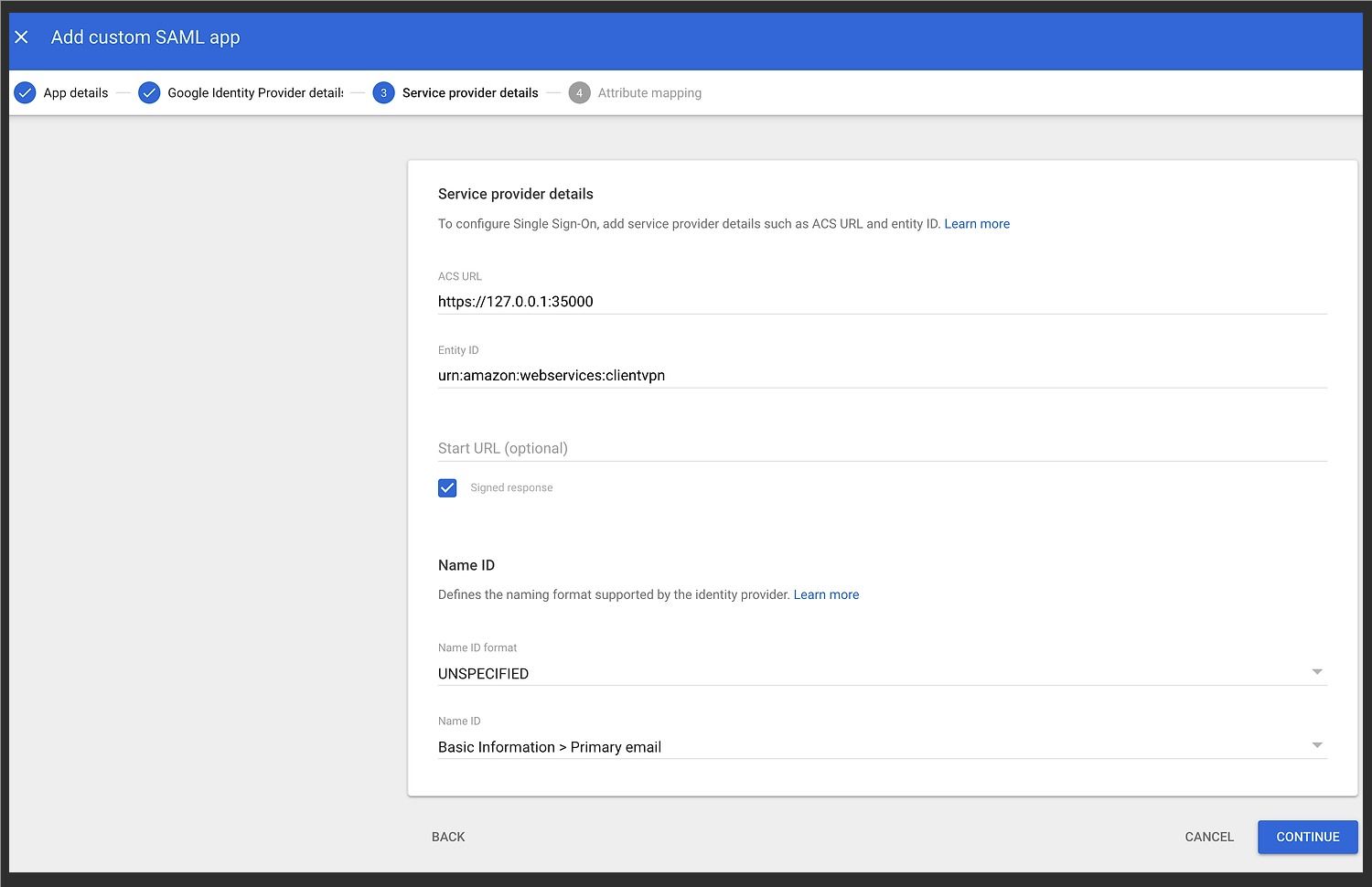
- Add the Attributes Mapping
- FirstName
- LastName
- memberOf
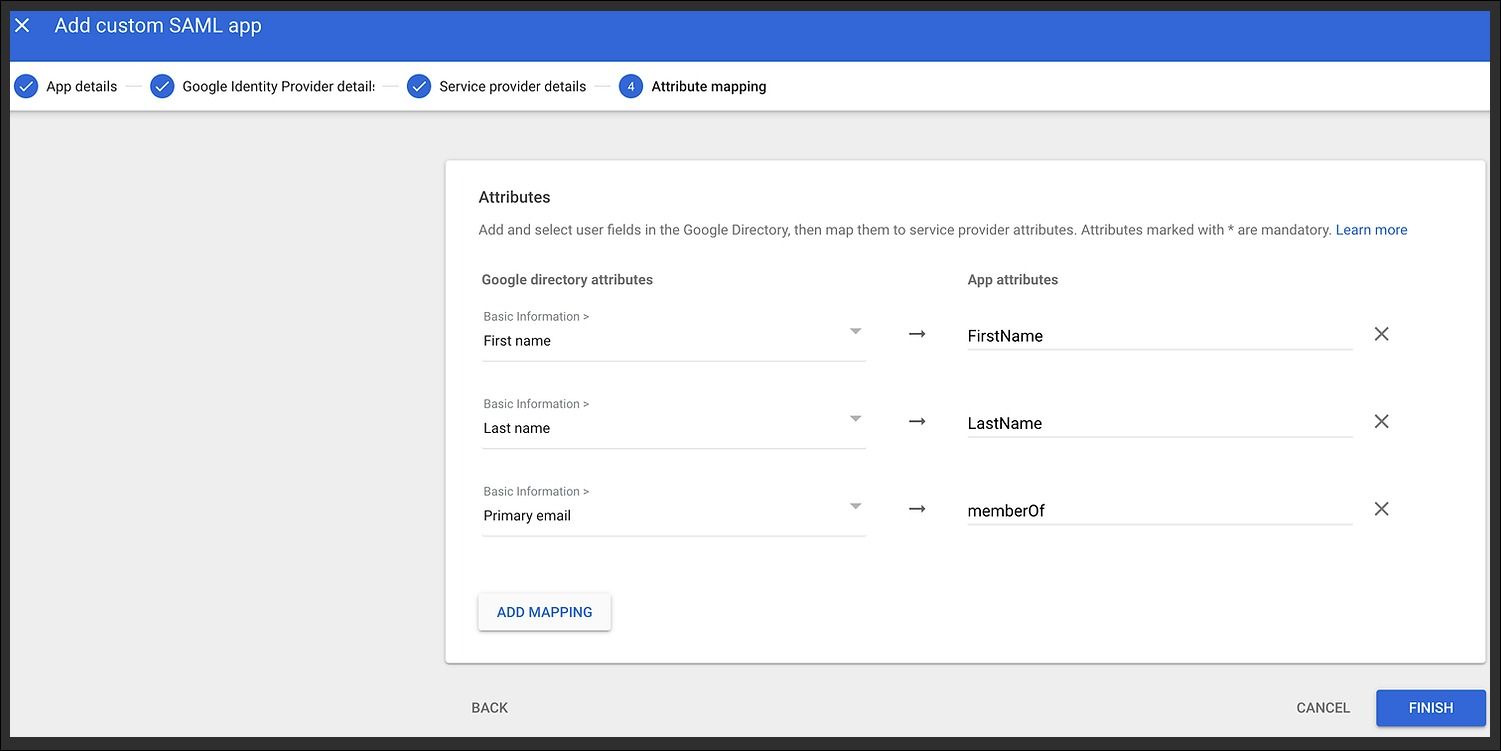
AWS requires the ACS URL to be http instead of https. However, there is a limitation in the UI to accept HTTP. Hence, we need to do some workarounds using the browser developer tools network tab. Let's learn how we overcame this limitation.
Click on the Service Provider Details of the SAML app in Google Admin Console and switch on Network Recording in the browser developer tools. Edit the ACS url to be https://127.0.0.1:35001 (port 35001) and click SAVE. This should show us the following page.
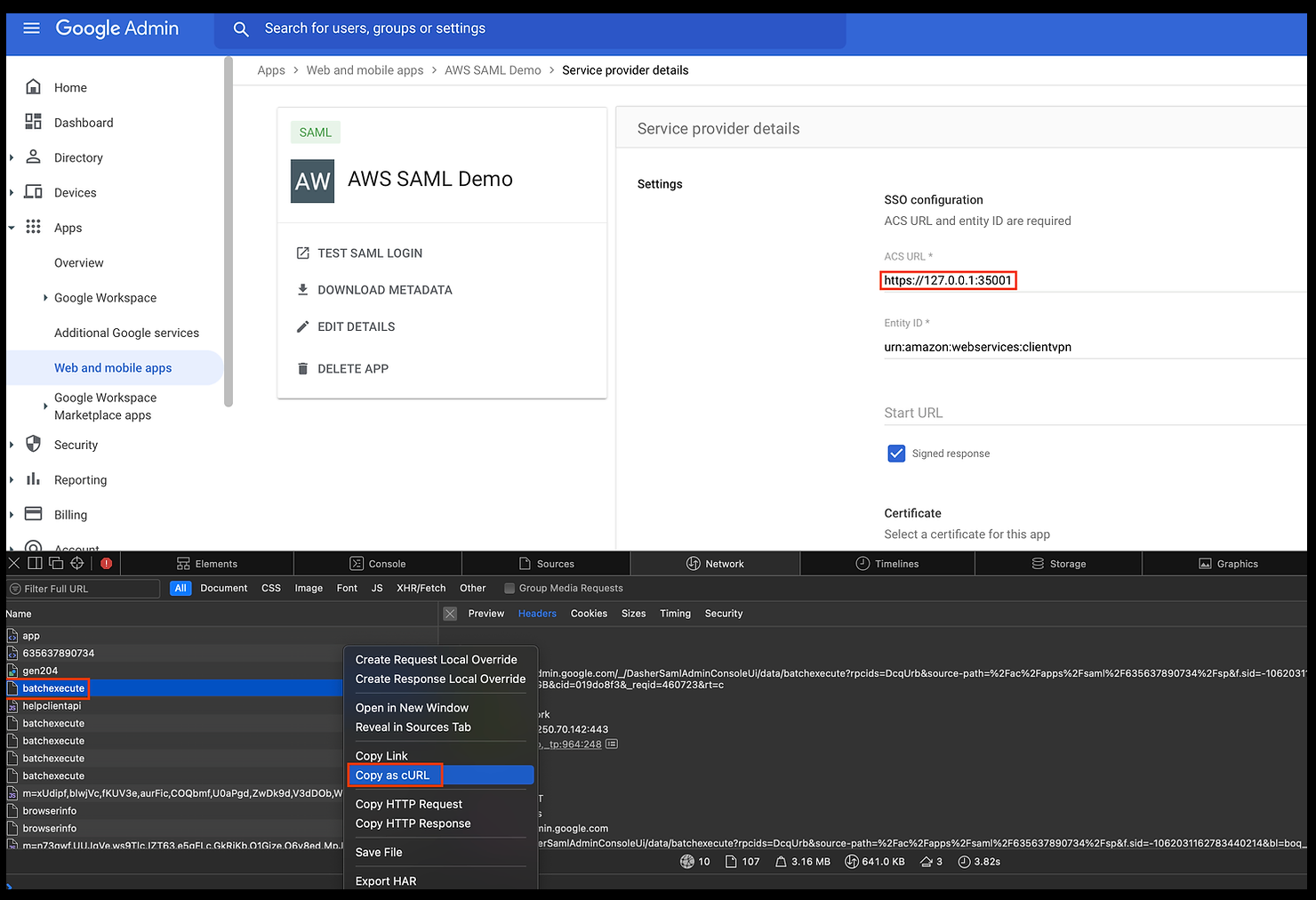
Click on the first HTTP POST request named batch-execute, right-click on it, and select Copy as cURL.Change the data-raw parameter's https to http, then use a terminal to execute the curl command and reload the page in the browser. Now the ACS URL box displays http://127.0.0.1:35001 instead of https.
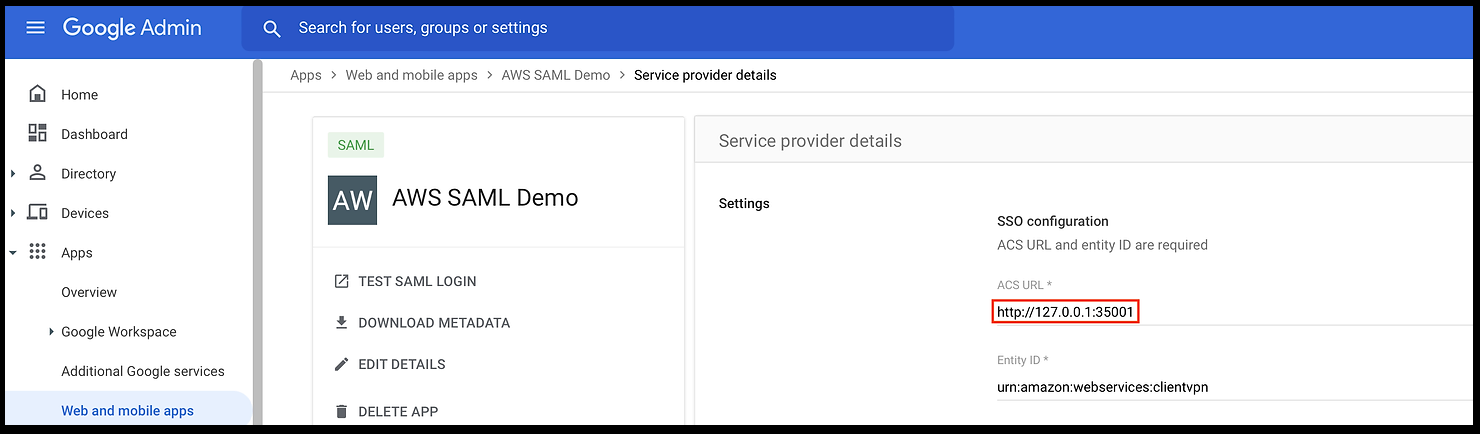
Finally, navigate back to the application's home page and click DOWNLOAD METADATA, which is essential for configuring user trust in AWS for the next steps.
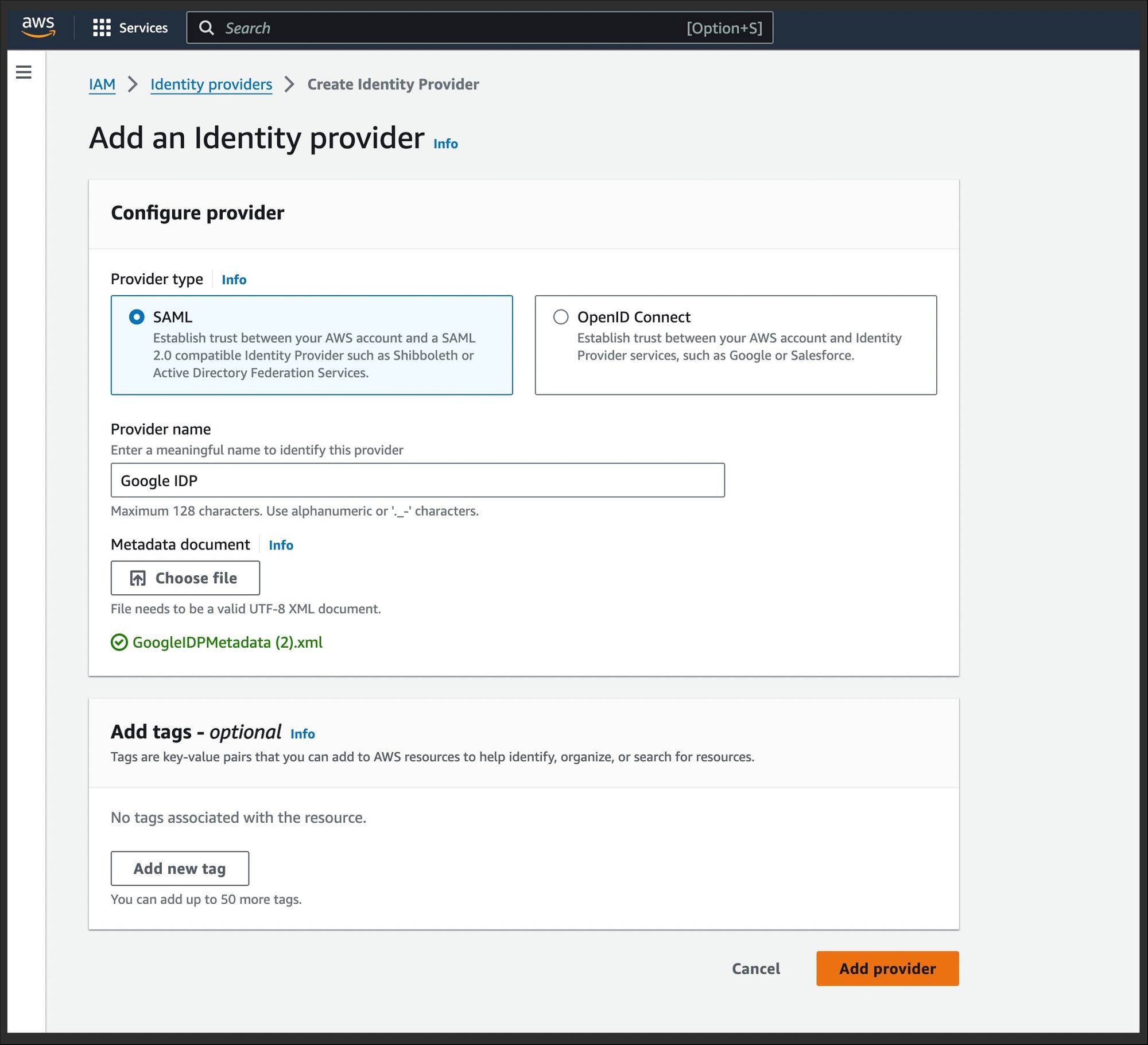
2. Create an IAM Identity Provider in AWS:
- In AWS account, go to IAM. select Identity Providers.
- Add provider
- Select provider type as SAML and give it a name like Google IDP
- Upload downloaded metadata document.
- Click on add provider.
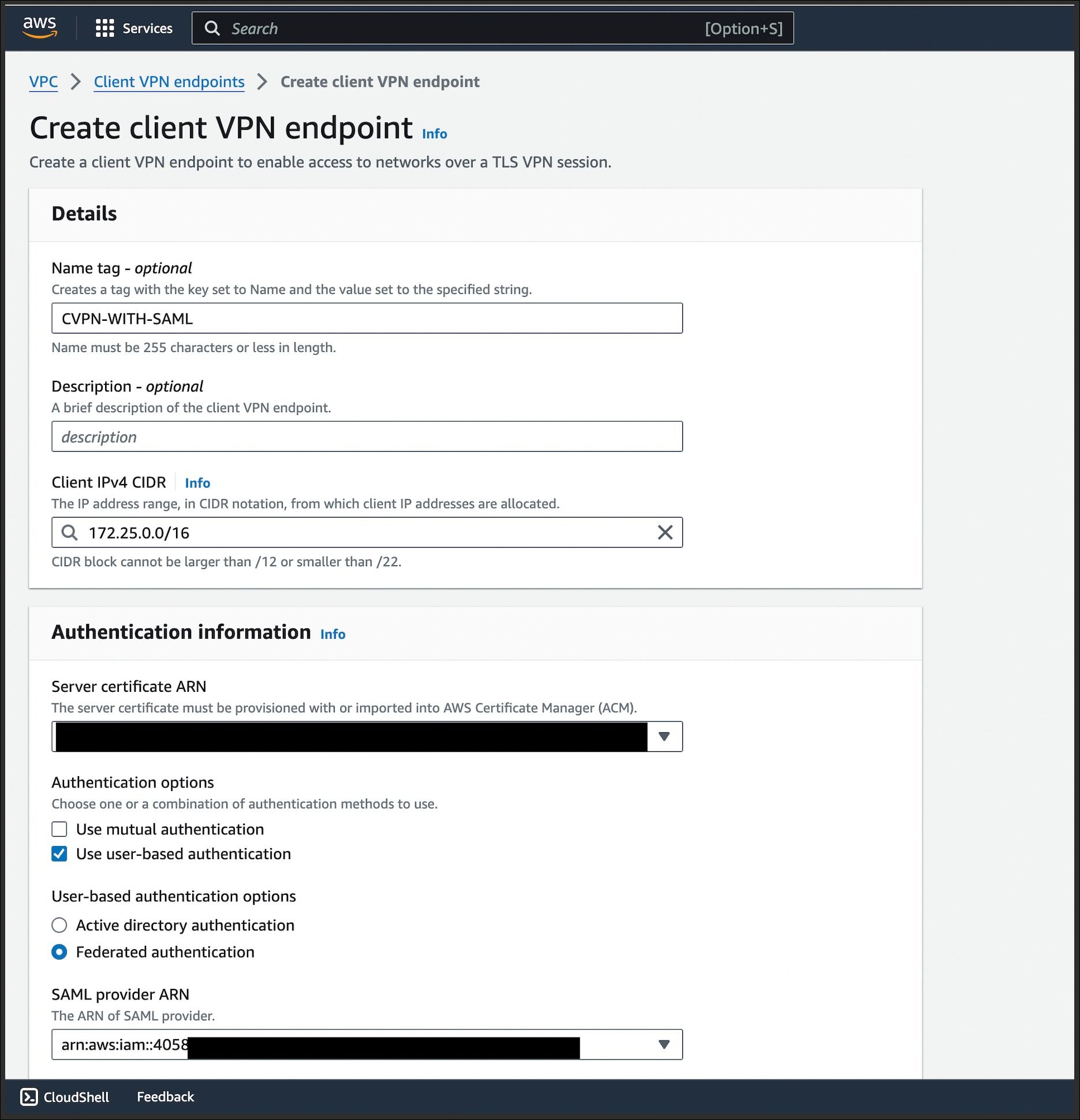
3. Setup AWS Client VPN Endpoint:
- In AWS account, go to VPC and select Client VPN endpoints under the Virtual Private Network section.
- Click on create client VPN endpoint and provide a meaningful name
- Mention the private client IPv4 CIDR.
- Under the Authentication Information, please provide the following details:
- Attach server certificate
- In Authentication options choose Use user-based authentication.
- Select Federated authentication in Use user-based authentication options
- Choose identity provider we created in previous step as SAML provider.
- Enable connection logging and select cloudwatch logs log group name.
- Provide private DNS server ip as primary and secondary as 8.8.8.8
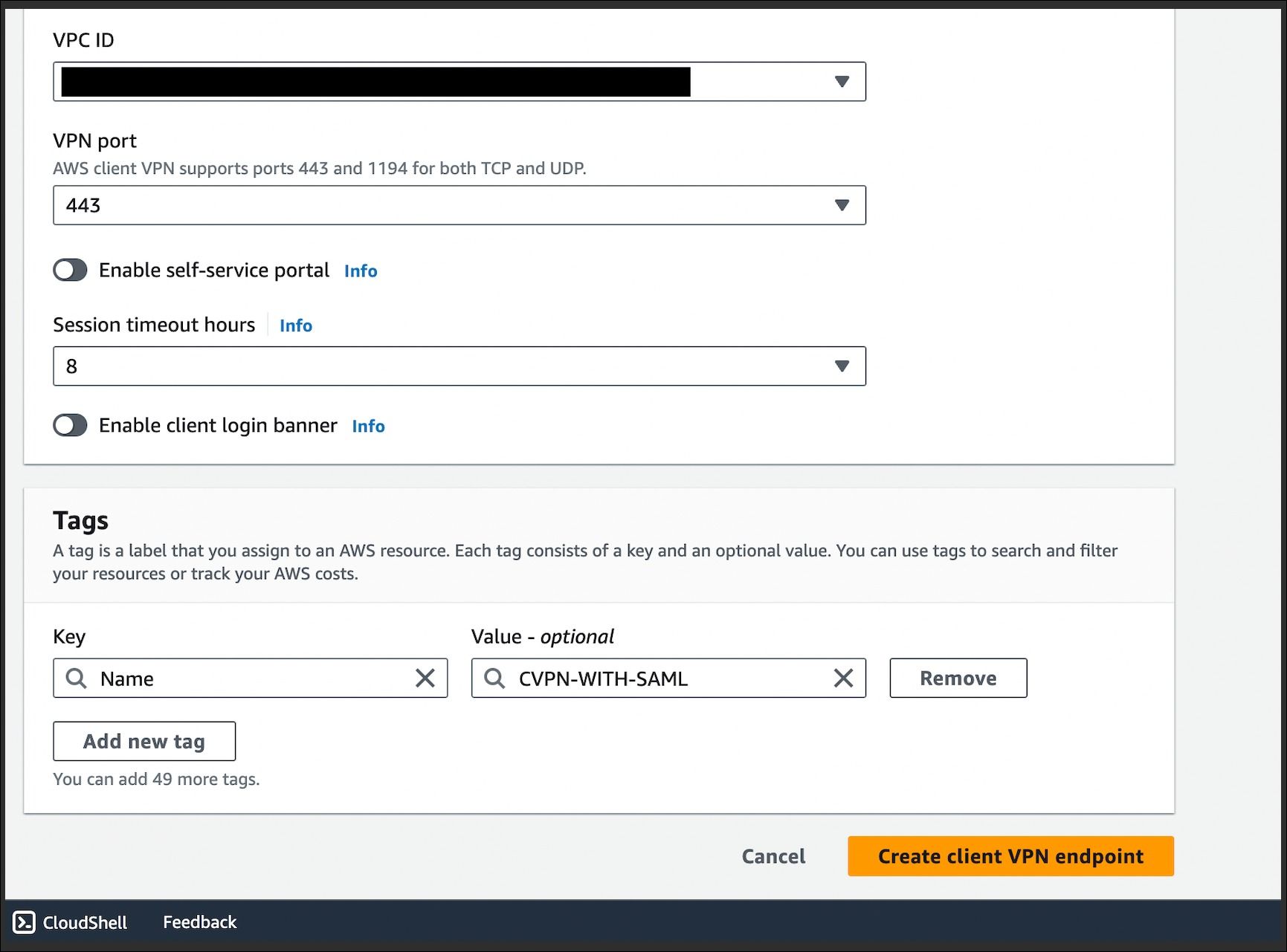
- Select the VPC in which the client VPN needs to be provisioned.
- Enable split-tunnel to transport only internal network traffic via VPN, the rest will be sent directly through the internet.
- Keep the session timeout as per the organization's standards.
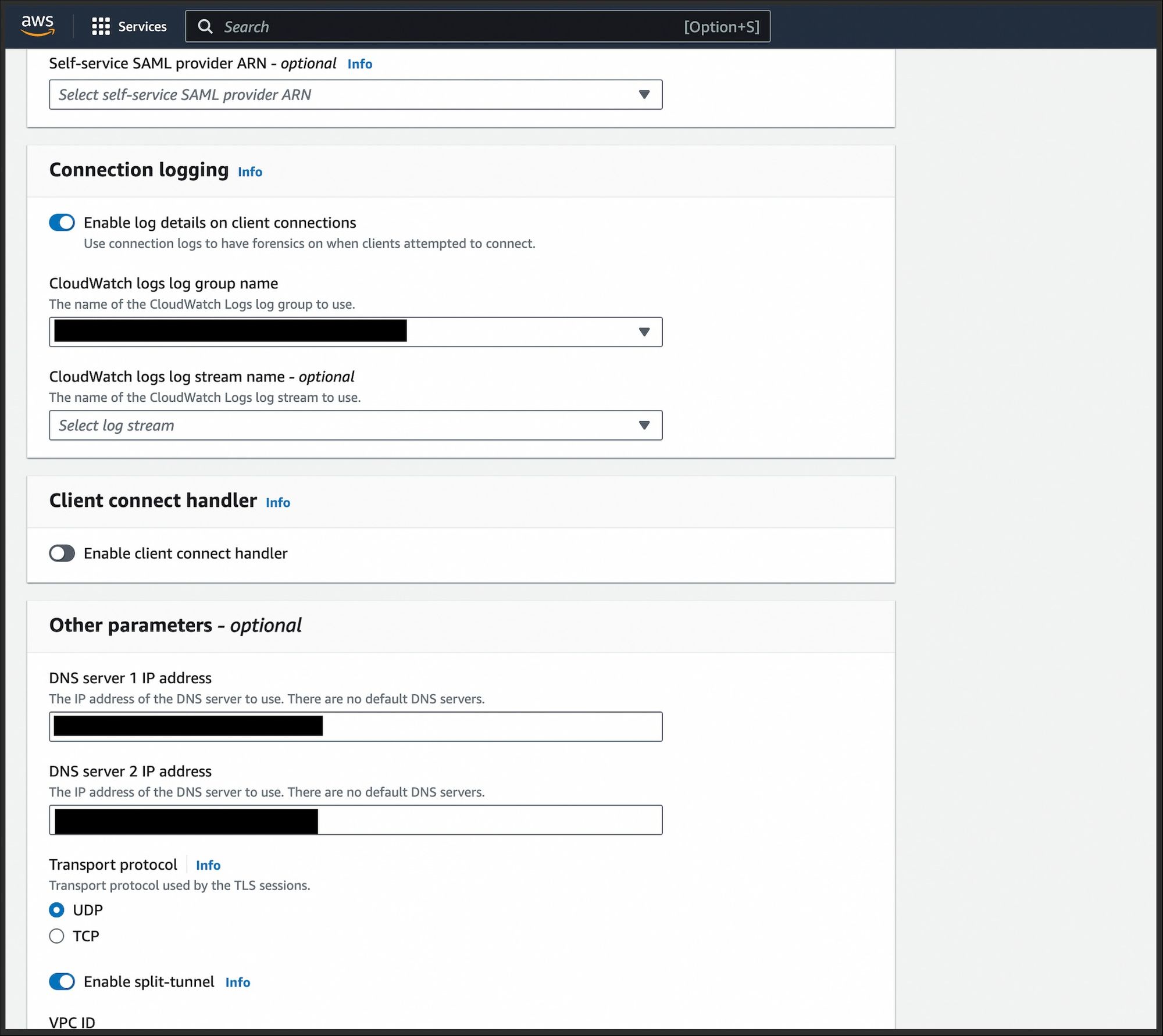
AWS Client VPN Connection Logging :
Enabling connection logging in AWS Client VPN provides vital visibility into connection details such as source and destination IP addresses, connection duration, and data transferred. This feature aids in security monitoring, troubleshooting, compliance, capacity planning, and user activity monitoring, enhancing overall network management and security measures.
4. Create the Target Network Associations:
Creating Target Network associations in AWS Client VPN involves associating the Client VPN endpoint with one or more VPC subnets. This allows traffic from the VPN clients to reach the resources in the associated subnets.
We can configure it via console or else use the below-mentioned AWS CLI command
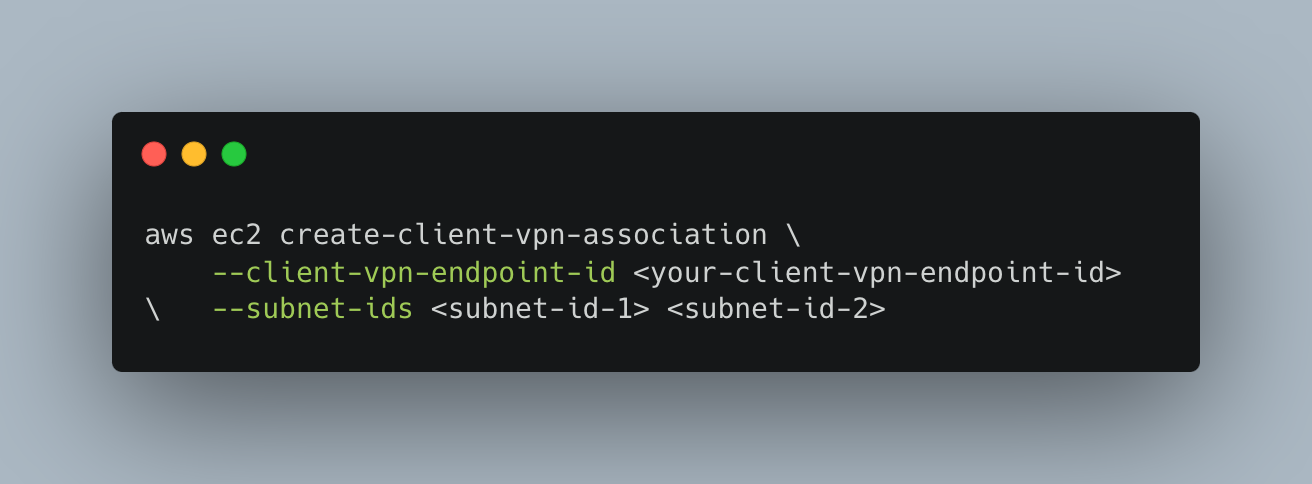
Please remember to replace <client-vpn-endpoint-id>, <subnet-id-1>, and <subnet-id-2> with the actual values.
Note: Add a minimum of two network associations in different subnets to achieve high availability.
5. Adding Route Table Entries:
Adding route table entries is essential for ensuring proper routing of traffic from VPN clients to their intended destinations. This process enables control over the accessibility of networks through VPN connections, ensuring that only specified networks are reachable via the VPN..
Steps to Add Route Table Entries:
- In AWS account, go to VPC. select Client VPN endpoints under the Virtual Private Network section.
- Select Client VPN endpoint to which we wish to add routing entries.
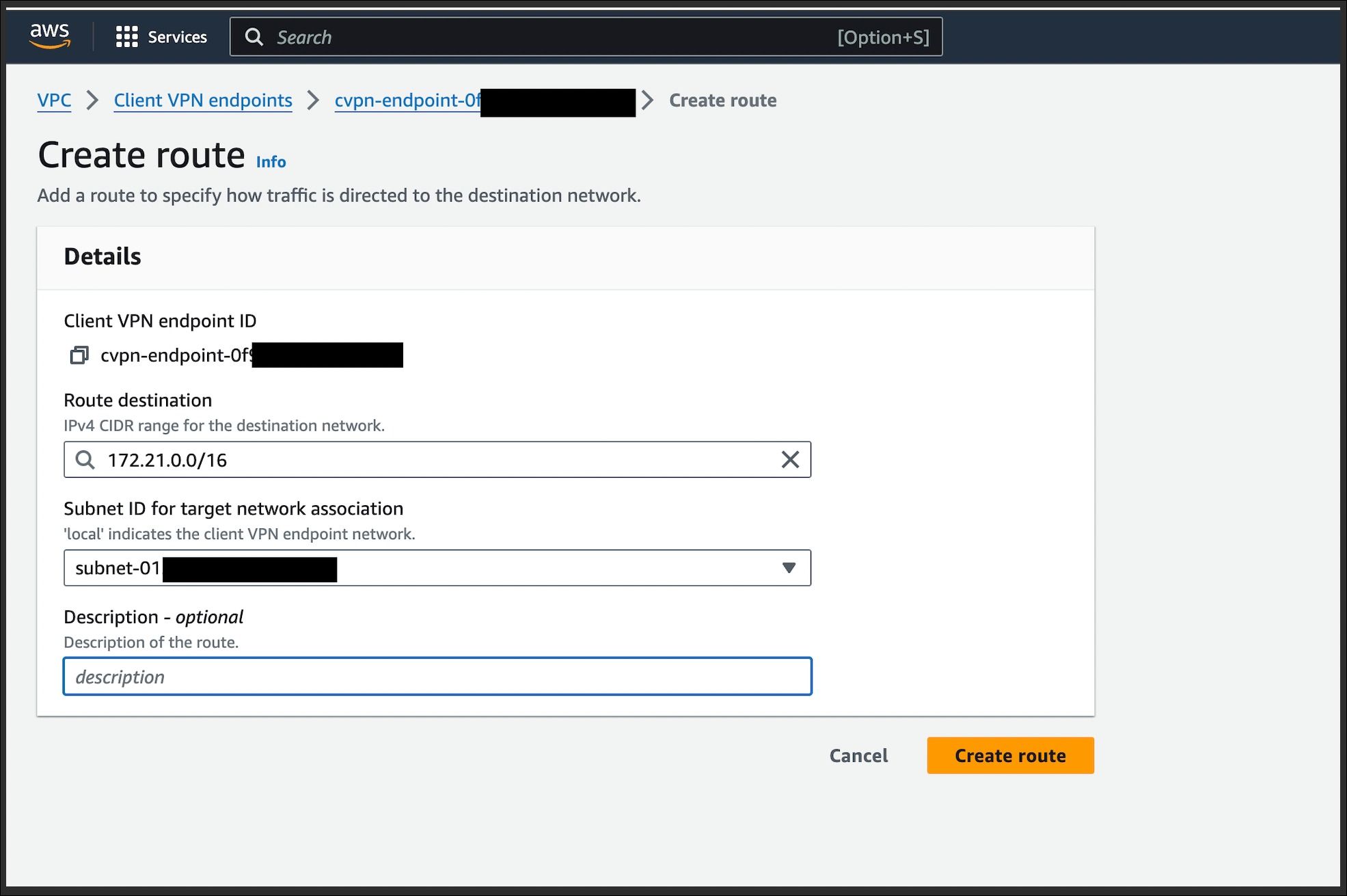
- In the details page, go to the "Route table" click on Create Route.
- Mention IPv4 CIDR range for the destination network.
- Select target network association.
- Click on create.
6. Adding Authorization Rules:
Authorization rules enhance VPN security by restricting access based on client IP addresses and associated security groups. By enforcing these rules, only authorized clients are permitted to establish VPN connections, thereby mitigating unauthorized access and bolstering overall network security
Steps to Add Authorization Rules:
- In AWS account, go to VPC. select Client VPN endpoints under the Virtual Private Network section.
- Select Client VPN endpoint to which we wish to add authorization rules.
- In the details page, go to the "Authorization rules" tab and click on add authorization rules.
- Mention the IPv4 CIDR range for the destination network.
- Select the group name in IDP.
- Click on add authorization rules
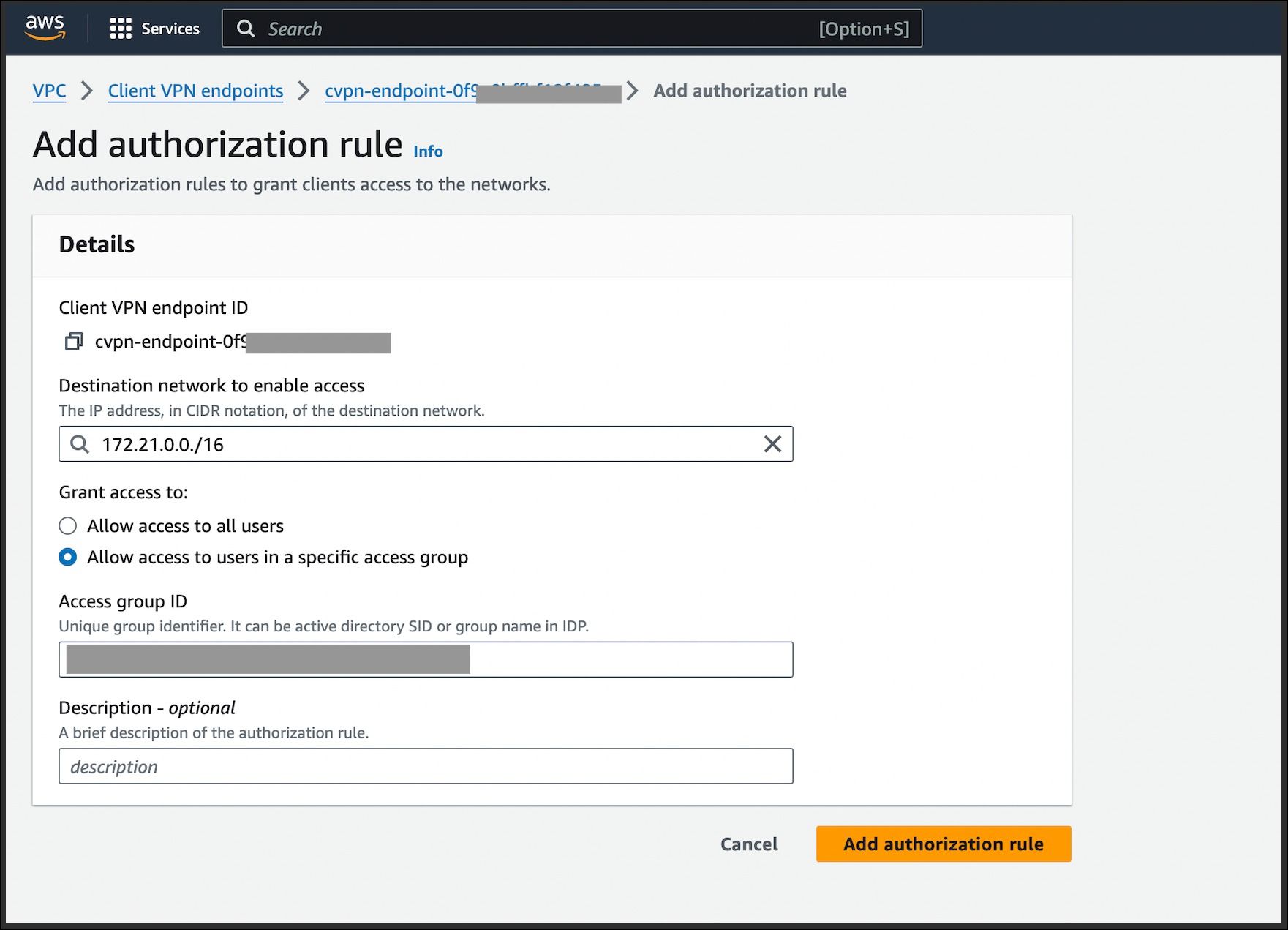
Once the aforementioned processes are successfully completed, the AWS Client VPN endpoint will be provisioned, and an Ovpn file will be generated accordingly. This file, available for download from the AWS Console, must be shared with the employee during the setup of the AWS VPN Client.
Connect AWS Client VPN Endpoint Via AWS VPN Client:
Step 1: Download the AWS VPN client from here as per the system’s OS and install it. It supports MacOS, Windows, & Ubuntu.
Step 2: Once Installation is complete, open the AWS VPN Client Software and click on File → Manage Profiles
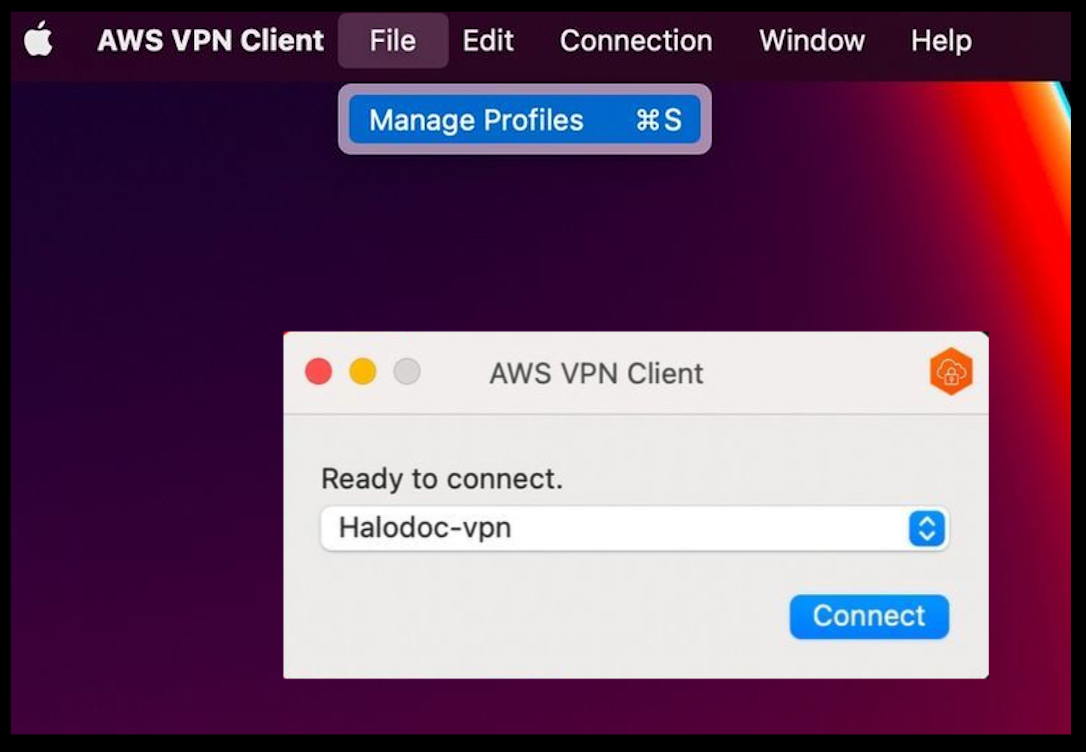
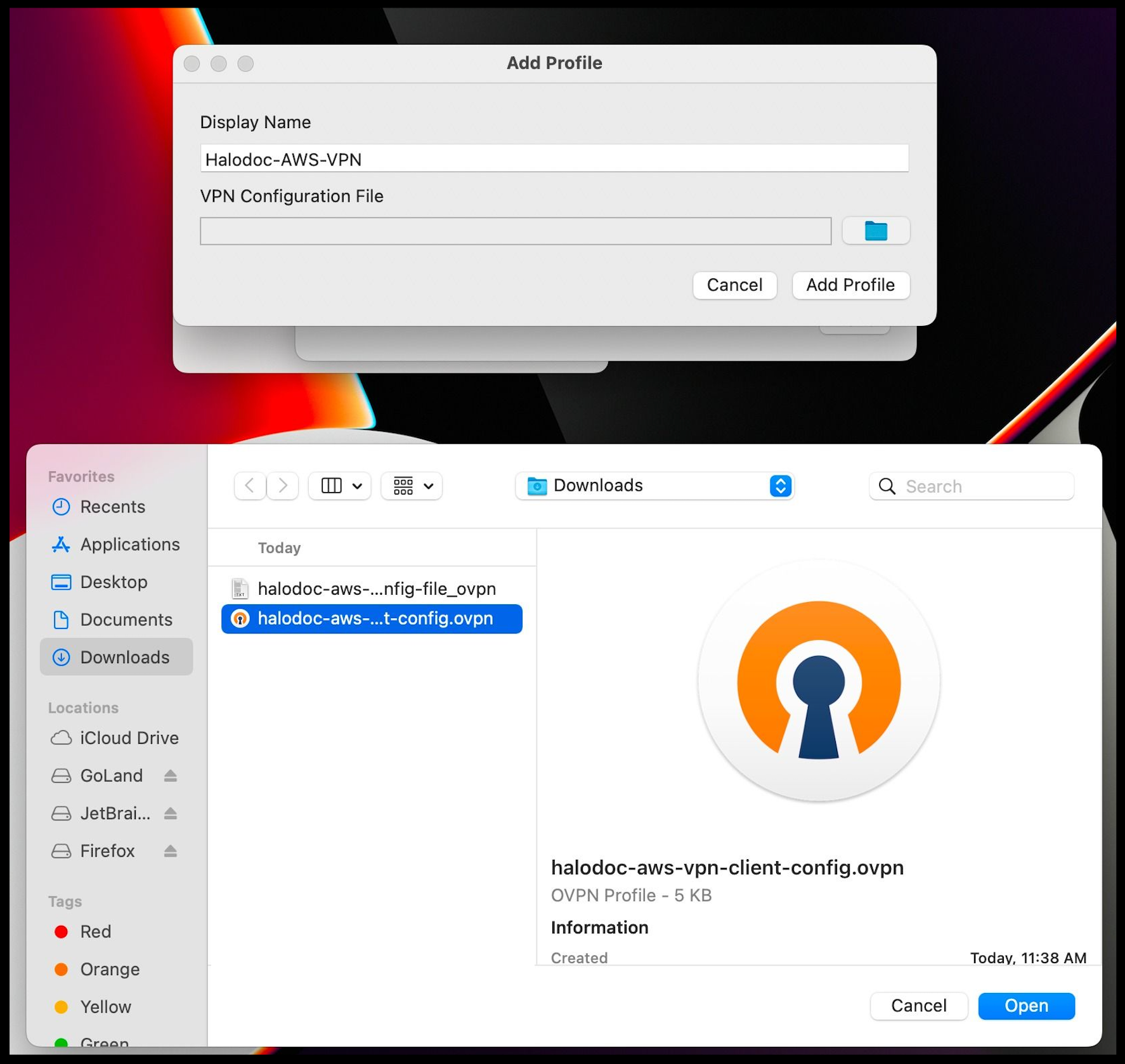
Step 3: Create a new profile using the AWS Client VPN configuration file provided by the IT team through email or any other communication medium.
Add Profile → Provide Display Name → Upload VPN Configuration File shared. → Click on Done
Step 4: Select the Profile → click on Connect.
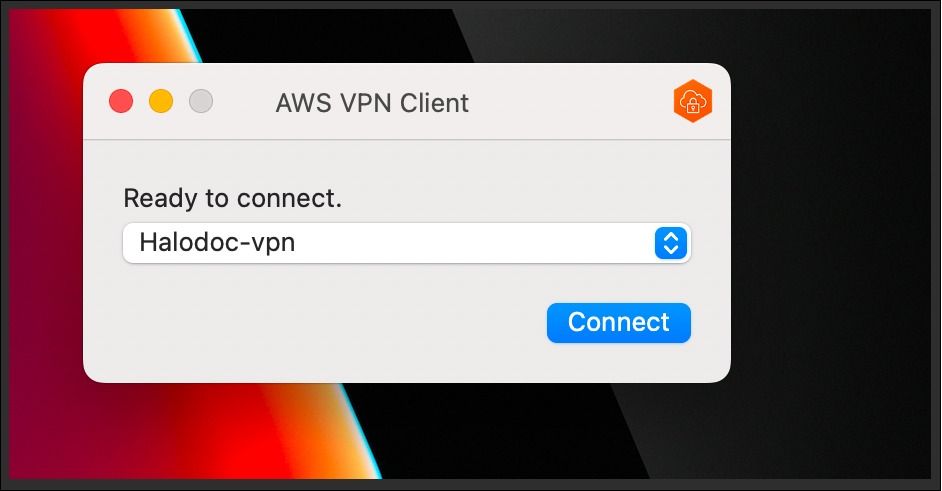
Step 5: A VPN connection will be started if a user is already logged in, or else it will ask them to do so using the Google login console with their official email address.
Once the VPN connection established successfully, will see this interface
Conclusion:
Our journey to a robust remote access solution culminated in successfully implementing AWS Client VPN. Confronted with a diverse array of operating systems, predominantly Windows with a notable Mac minority, we opted for the flexibility and security of SAML authentication. Prioritizing Windows users, comprising 80% of our workforce, facilitated efficient deployment and management of the AWS VPN Client software. However, compatibility challenges emerged with Mac OS versions beyond Ventura 13.6, prompting us to adopt a phased approach. Initially, focusing on equipping Windows-dominant users helped streamline deployment and reduce management complexities. As we await a stable AWS VPN Client version compatible with the latest Mac OS, our strategy underscores a user-centric and adaptive implementation approach. This anticipates seamlessly integrating the remaining Mac users into our secure remote access ecosystem through SAML authentication.
References:
Join us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels, and if solving hard problems with challenging requirements is your forte, please reach out to us with your resume at careers.india@halodoc.com.
About Halodoc
Halodoc is the pioneer of a digital health ecosystem with a mission to simplify healthcare access by addressing users’ pain points through accessible, reliable, and quality services. The company’s commitment to promoting wellness is reflected in the comprehensive range of health solutions, covering preventive to curative approaches, all within a single application.Since 2016, Halodoc has been enhancing health literacy in Indonesia through user-friendly healthcare Communication, Education, and Information (KIE). Our expanding ecosystem offers a range of convenient healthcare services, including Home Lab for home care health test; My Insurance for seamless access to cashless outpatient service benefits; Chat with Doctor teleconsultation with 20,000+ licensed doctors and health workers; as well as Health Store for access to purchase medicines, supplements, and various health products from 4,900+ trusted partner pharmacies. Halodoc has been recognized as one of a telehealth platform making a positive impact on the healthcare sector and received the “supervised” status in the Regulatory Sandbox program by the Ministry of Health of the Republic of Indonesia. It reflects a strong commitment and partnership between Halodoc and the MoH, ensuring participatory supervision to safeguard Digital Health Innovation (IDK) organizers, consumers and healthcare workers as the partner of digital innovations. The platform has also received a string of prestigious awards, including being featured on CB Insights’ Digital Health 150 list in 2019–2020 and receiving the Indonesian government’s 2023 PPKM Award. Download Halodoc app via iOS and Android.
