Implementation of CIS AWS v1.5 Foundation Benchmark for AWS Cyber Posture Assessment
Overview
Cybersecurity threats are constantly evolving: As technology advances, so do the methods and tools used by cybercriminals to exploit vulnerabilities. Hence, it is important for an organization to continuously monitor its cyber security posture via an automated cyber security monitoring and assessment. This will help to stay on top of these evolving threats.
In addition to this, a continuous assessment can be more cost-effective than periodic assessments as it helps to identify and address issues before they become more significant and more expensive to fix.
Why is continuous security monitoring important?
A security breach can happen at any time, and the consequences can be devastating for an organization. Continuous assessment can help to identify vulnerabilities and address them before they are exploited. Furthermore, it helps to identify risks and vulnerabilities and prioritize them based on their potential impact. This allows organizations to focus their resources on addressing the most critical risks first.
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) is a set of tools and activities that help organizations assess, manage, and improve the security posture of their cloud environments.
The goal of CSPM is to provide visibility into an organization's cloud infrastructure, identify potential security risks, and enable remediation of those risks before they can be exploited. CSPM enables organizations to benchmark systems against CIS standards, so they can get a better understanding of their security posture.
Center for Internet Security (CIS) Benchmarks
CIS publishes benchmarks that provide secure configuration best practices for various IT systems and cloud infrastructures. These benchmarks are developed by the CIS team along with a wider community of technology vendors, subject matter experts, and others.
These benchmarks are considered the global best practices for security for any organization implementing secure configuration for their cloud infrastructure. We adjusted this benchmark relevant to our environment and needs.
CIS AWS v1.5 foundation benchmark for AWS Cyber Posture Assessment
CIS and AWS publish the CIS AWS Foundations benchmark. This benchmark is used to validate their security posture in the AWS environment. One of the tools used by Halodoc in relation with identification of security vulnerabilities is Pingsafe, an agentless solution which could analyze critical vulnerabilities in our cloud infrastructure through vulnerability scanning and compliance posture checking against many security best practices.
And as we are running on AWS cloud, the CIS AWS Foundations Benchmark plug-in in Pingsafe serves as a set of security configuration best practices for AWS based infrastructure. These industry-accepted best practices provide you with clear, step-by-step implementation and assessment procedures.
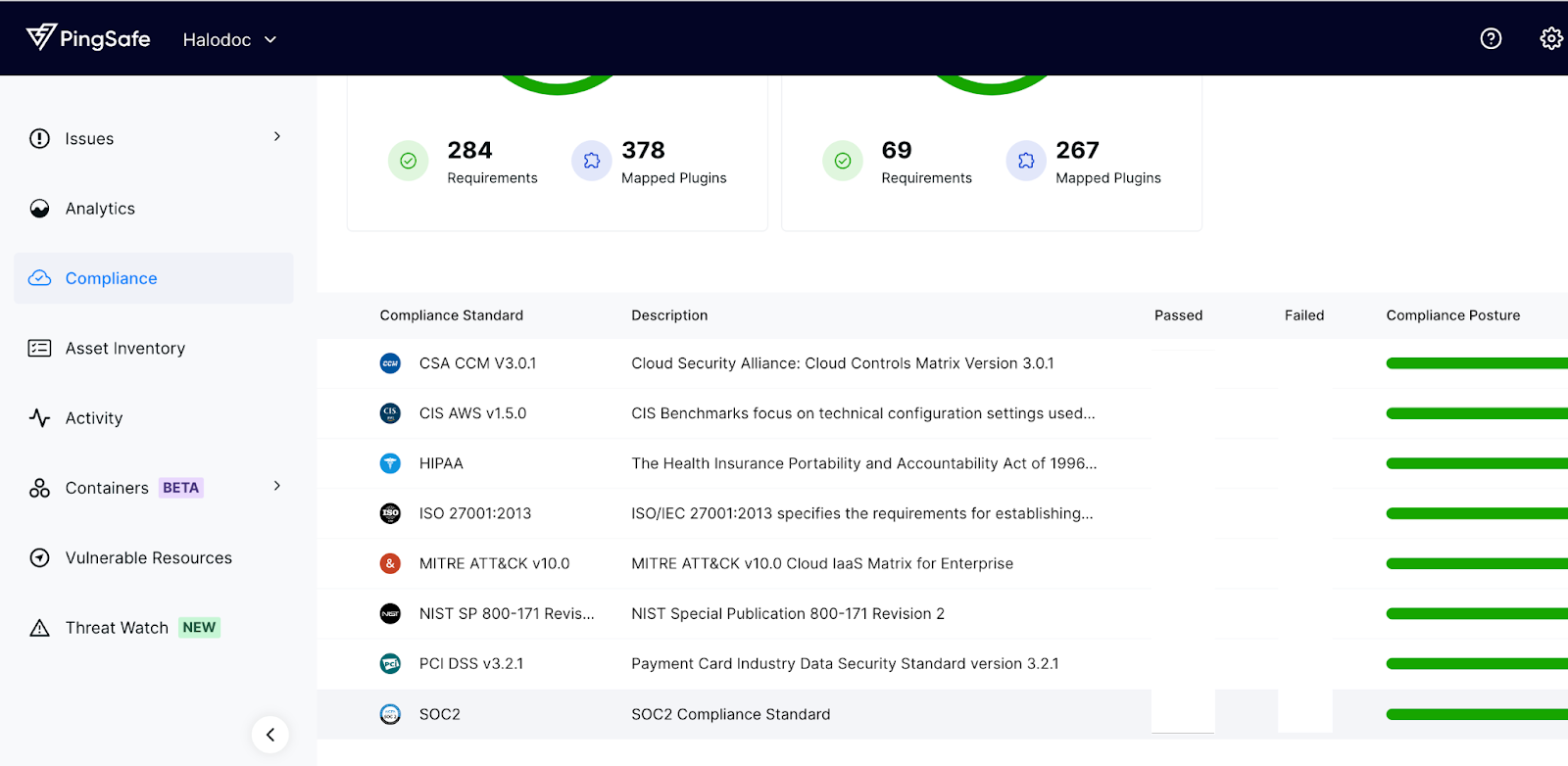
A brand new version of Benchmark v1.5.0 was published on 12 August 2022, and has been used as Halodoc’s standard for compliance since this early 2023, as shown below in Halodoc’s Pingsafe compliance report.
What are the new recommendations of this new version?
5 new recommendations have been added under different sections and subsections of the benchmark, as described below. We have also deployed these 5 recommendations into our monitoring.
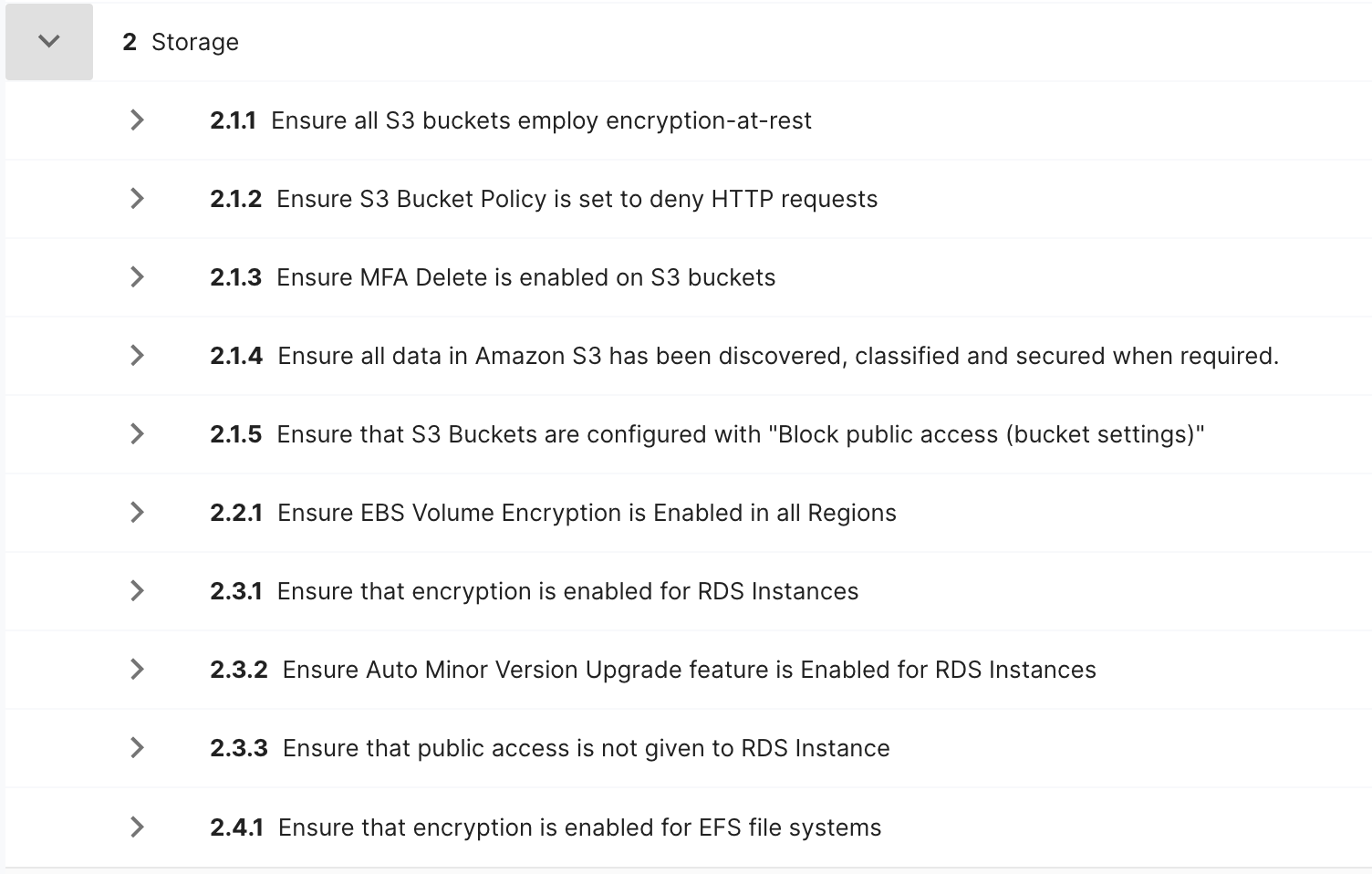
2.3.2 Ensure Auto Minor Version Upgrade feature is Enabled for RDS Instances — RDS database instances should have the Auto Minor Version Upgrade flag enabled in order to receive automatically minor engine upgrades during the specified maintenance window. So, RDS instances can get the new features, bug fixes, and security patches for their database engines.
2.3.3 Ensure that public access is not given to RDS Instances — RDS database instances provisioned in your AWS account should restrict unauthorized access in order to minimize security risks. To restrict access to any publicly accessible RDS database instance, you must disable the database Publicly Accessible flag and update the VPC security group associated with the instance.
2.4.1 Ensure that encryption is enabled for EFS file systems — EFS data should be encrypted at rest using AWS KMS (Key Management Service).
Below are the complete list of area 2 (Storage) recommendations in CIS AWS v1.5.
4.16 Ensure AWS Security Hub is enabled — Security Hub collects security data from across AWS accounts, services, and supported third-party partner products and helps analyze security trends and identify the highest priority security issues. When Security Hub is enabled, it begins to consume, aggregate, organize, and prioritize findings from AWS services that have been enabled, such as Amazon GuardDuty, Amazon Inspector, and Amazon Macie. You can also enable integrations with AWS partner security products. Implementation of other third-party products such as Pingsafe can be considered as mitigating controls to achieve the objectives of the recommendation.
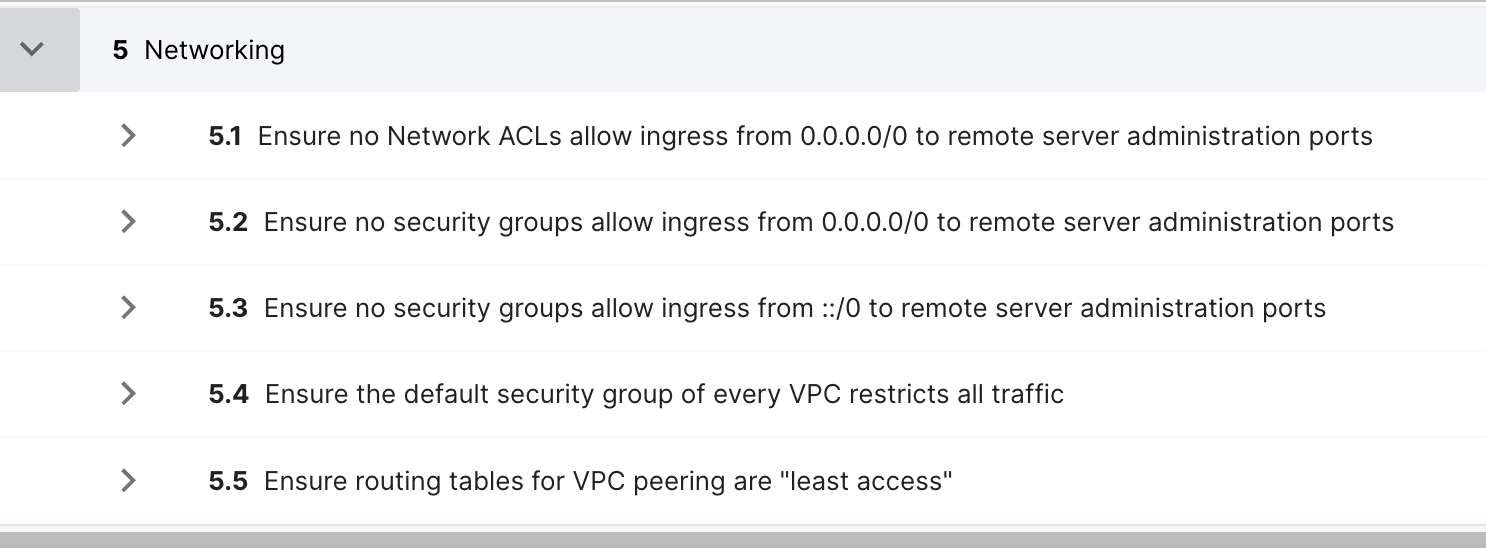
5.3 Ensure no security groups allow ingress from ::/0 to remote server administration ports — This is the IPv6 version of "5.2 Ensure no security groups allow ingress from 0.0.0.0/0 to remote server administration ports."
Below are the complete list of area 5 (Networking) recommendations in CIS AWS v1.5.
These updates are one of our continuous efforts to proactively identify, detect, and implement security improvements to a continuous security monitoring of our technology environment.
Conclusion
A continuous security monitoring using CIS v1.5 benchmark provides an insight into the security posture of an organization. The insight will be the basis to further strengthen the security and remediate any vulnerabilities in the system. Consistent implementation of the assessment will enable an organization to improve their security posture and remediate security vulnerabilities on a timely basis.
Join us
Scalability, reliability, and maintainability are the three pillars that govern what we build at Halodoc Tech. We are actively looking for engineers at all levels and if solving hard problems with challenging requirements is your forte, please reach out to us with your resumé at careers.india@halodoc.com.
About Halodoc
Halodoc is the number 1 all around Healthcare application in Indonesia. Our mission is to simplify and bring quality healthcare across Indonesia, from Sabang to Merauke. We connect 20,000+ doctors with patients in need through our Tele-consultation service. We partner with 3500+ pharmacies in 100+ cities to bring medicine to your doorstep. We've also partnered with Indonesia's largest lab provider to provide lab home services, and to top it off we have recently launched a premium appointment service that partners with 500+ hospitals that allow patients to book a doctor appointment inside our application. We are extremely fortunate to be trusted by our investors, such as the Bill & Melinda Gates Foundation, Singtel, UOB Ventures, Allianz, GoJek, Astra, Temasek and many more. We recently closed our Series C round and In total have raised around USD$180 million for our mission. Our team works tirelessly to make sure that we create the best healthcare solution personalized for all of our patient's needs, and are continuously on a path to simplify healthcare for Indonesia.
